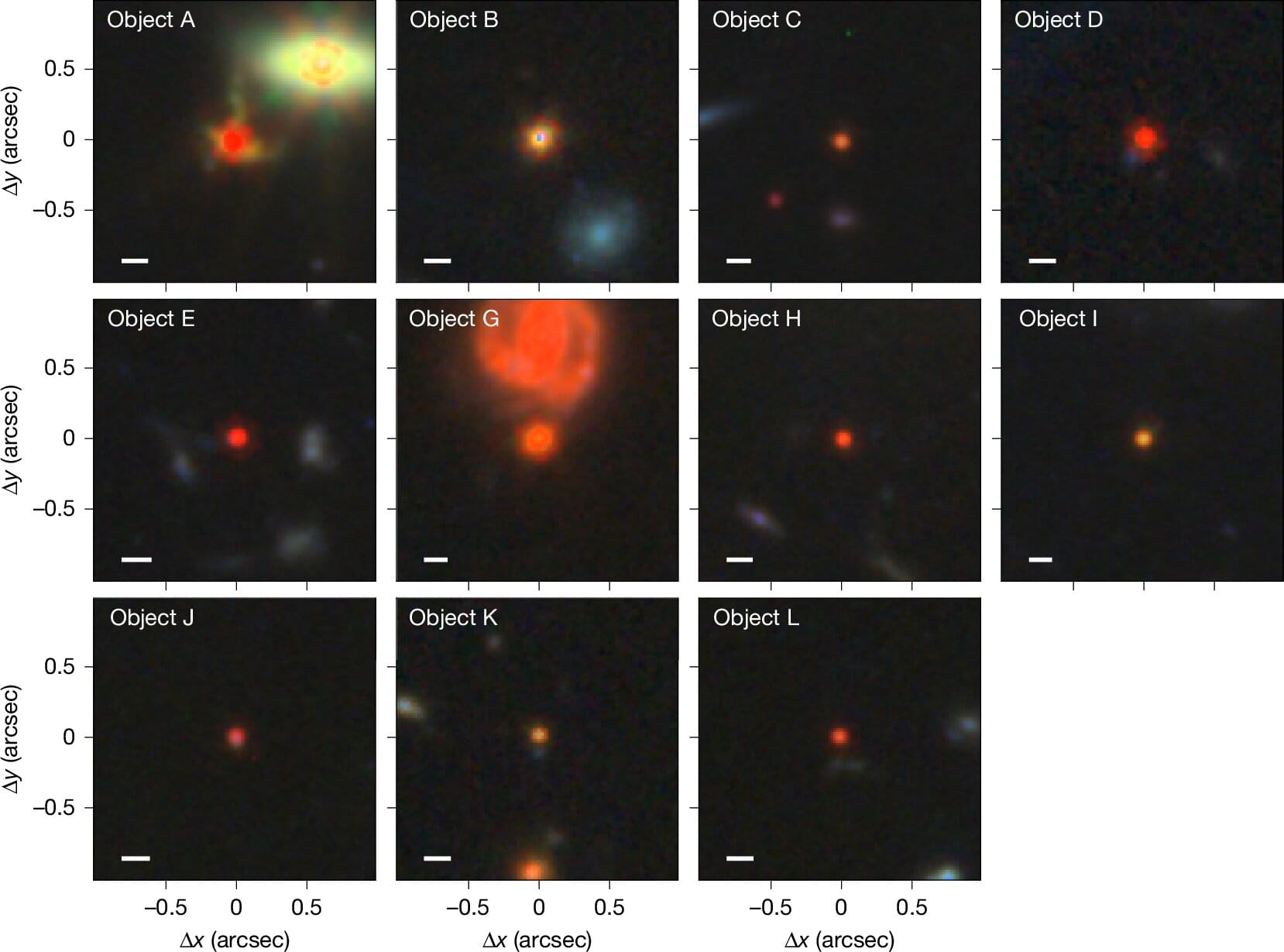
Since the James Webb Space Telescope (JWST) went into operation, red dots in its images have puzzled researchers around the world. Now, researchers from the University of Copenhagen have explained these enigmatic findings, revealing the most violent forces in the universe concealed in a cocoon of ionized gas. The discovery is published in Nature.
Since December 2021, when the James Webb super telescope saw first light, some 1.5 million kilometers from Earth, researchers around the world have been scratching their heads over unexplained red dots among stars and galaxies in the images taken by the telescope.
The so-called ‘little red dots’ can be seen when the universe was “only” several hundred million years old, and a billion years later, they seem to disappear again. So what were they?