Signals recorded by implanted electrodes enable accurate prosthetic control of hand and wrist movements under real-world conditions




Recent advances in biomolecular archaeology have revealed that ancient objects can retain the molecular fingerprints of past aromatic practices. These molecules provide unprecedented insight into ancient perfumery, medicine, ritual, and daily life.
In a publication in Frontiers in Environmental Archaeology, an interdisciplinary research team led by archaeo-chemist Barbara Huber (Max Planck Institute of Geoanthropology and the University of Tübingen), shows how museums can use this molecular evidence to engage audiences with the sensory worlds of the past. The team combined their expertise to create a new workflow for converting biomolecular data into accessible, visitor-ready olfactory recreations.
“This research represents a significant shift in how scientific results can be shared beyond academic publications,” explains Huber.
Kevin Perrott founded OpenCures, has been an adjunct professor at the University of Alberta, co-founded Oisin Biotechnologies, and ran a gym.

Physicists have uncovered surprising order inside one of the most puzzling states in modern materials science. It is a strange middle ground where electrons begin to behave differently, but full superconductivity has not yet taken hold.
Instead of falling into disorder, the system retains coordinated patterns right at the point where normal electrical behavior starts to break down. The finding suggests this transition is guided by an underlying structure, not randomness.
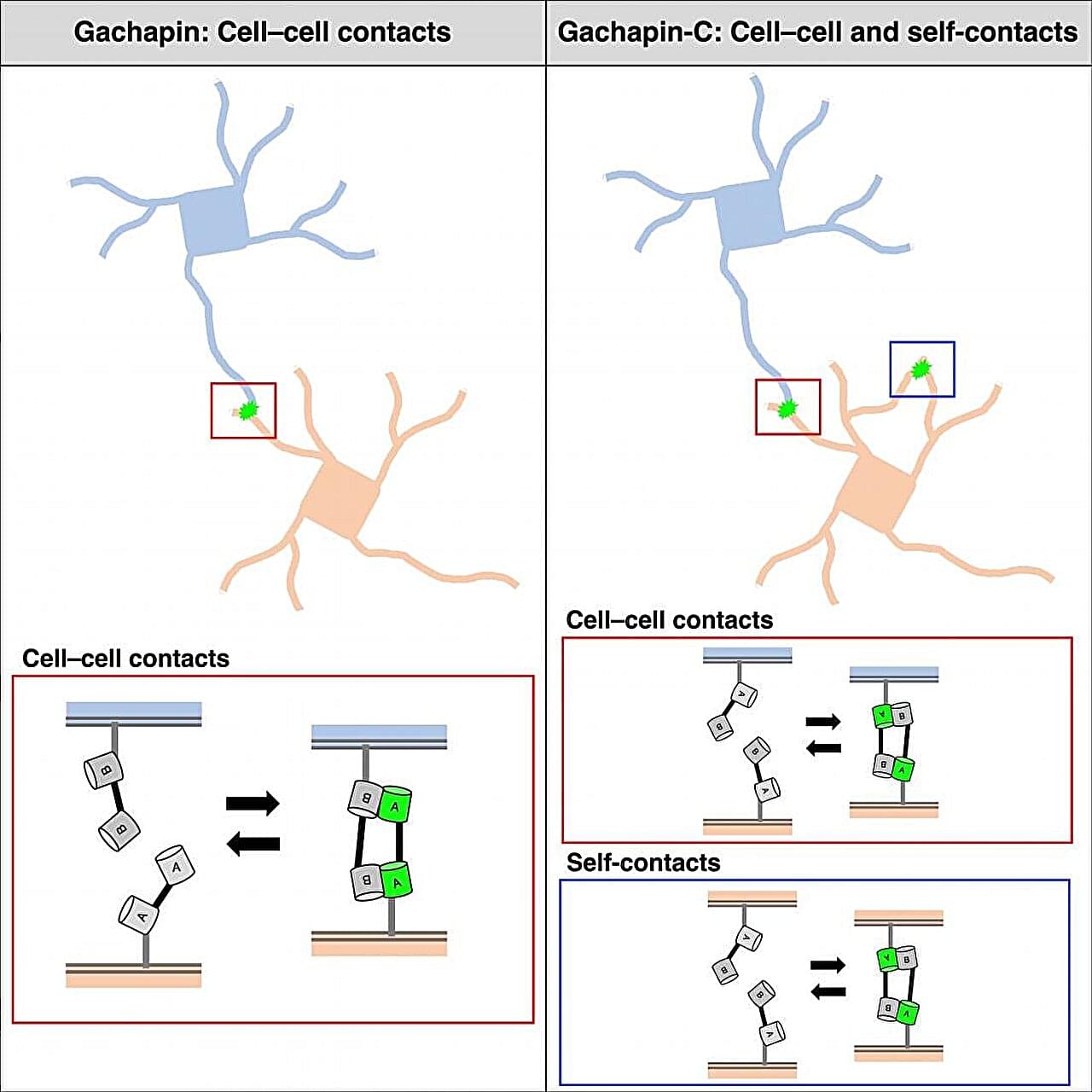
Living organisms are made up of hundreds of thousands of cells that cooperate to create the organs and systems that breathe, eat, move, and think. Now, researchers from Japan have developed a new way to track how and when cells touch each other to work together in these ways. In a study published in January in Cell Reports Methods, researchers from The University of Osaka reported the development of fluorescent markers for monitoring cell communication under a microscope.
Cells communicate with each other by making cell-to-cell contacts, and fluorescent markers are often used to visualize these contacts. The most commonly used marker for this purpose is green fluorescent protein (GFP). GFP can be divided into two halves that are expressed on different cells. When the cells touch, the two halves come together to form a complete GFP, letting off a fluorescent signal.
“Split GFP is useful for detecting the formation of stable connections between cells,” says lead author of the study Takashi Kanadome. “But because it takes time for the rejoined GFP to emit its signal and the association is irreversible, this approach cannot be used to detect dynamic cell–cell interactions in real-time.”