Apple releases security updates fixing exploited dyld zero-day CVE-2026–20700 enabling code execution across iOS, macOS, and Apple devices.



Cybersecurity researchers have discovered what they said is the first known malicious Microsoft Outlook add-in detected in the wild.
In this unusual supply chain attack detailed by Koi Security, an unknown attacker claimed the domain associated with a now-abandoned legitimate add-in to serve a fake Microsoft login page, stealing over 4,000 credentials in the process. The activity has been codenamed AgreeToSteal by the cybersecurity company.
The Outlook add-in in question is AgreeTo, which is advertised by its developer as a way for users to connect different calendars in a single place and share their availability through email. The add-in was last updated in December 2022.

Indian defense sector and government-aligned organizations have been targeted by multiple campaigns that are designed to compromise Windows and Linux environments with remote access trojans capable of stealing sensitive data and ensuring continued access to infected machines.
The campaigns are characterized by the use of malware families like Geta RAT, Ares RAT, and DeskRAT, which are often attributed to Pakistan-aligned threat clusters tracked as SideCopy and APT36 (aka Transparent Tribe). SideCopy, active since at least 2019, is assessed to operate as a subdivision of Transparent Tribe.
“Taken together, these campaigns reinforce a familiar but evolving narrative,” Aditya K. Sood, vice president of Security Engineering and AI Strategy at Aryaka, said. “Transparent Tribe and SideCopy are not reinventing espionage – they are refining it.”




Microsoft has fixed a “remote code execution” vulnerability in Windows 11 Notepad that allowed attackers to execute local or remote programs by tricking users into clicking specially crafted Markdown links, without displaying any Windows security warnings.
With the release of Windows 1.0, Microsoft introduced Notepad, a simple, easy-to-use text editor that, over the years, became popular for quickly jotting notes, reading text files, creating to-do lists, or acting as a code editor.
For those who needed a rich text format (RTF) editor that supported different fonts, sizes, and formatting tools like bold, italics, and lists, you could use Windows Write and later WordPad.

A member of the Crazy ransomware gang is abusing legitimate employee monitoring software and the SimpleHelp remote support tool to maintain persistence in corporate networks, evade detection, and prepare for ransomware deployment.
The breaches were observed by researchers at Huntress, who investigated multiple incidents where threat actors deployed Net Monitor for Employees Professional alongside SimpleHelp for remote access to a breached network, while blending in with normal administrative activity.
In one intrusion, attackers installed Net Monitor for Employees Professional using the Windows Installer utility, msiexec.exe, allowing them to deploy the monitoring agent on compromised systems directly from the developer’s site.

The AgreeTo add-in for Outlook has been hijacked and turned into a phishing kit that stole more than 4,000 Microsoft account credentials.
Originally a legitimate meeting scheduling tool for Outlook users, the module was developed by an independent publisher and has been on the Microsoft Office Add-in Store since December 2022.
Office add-ins are just URLs pointing to content loaded into Microsoft products from the developer’s server. In the case of AgreeTo, the developer used a Vercel-hosted URL (outlook-one.vercel.app) but abandoned the project, despite the userbase it formed.
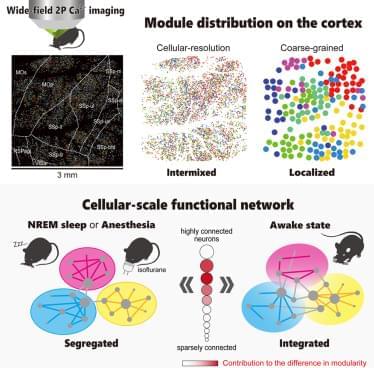
The common neural mechanisms underlying the reduction of consciousness during sleep and anesthesia remain unclear. Previous studies have examined changes in network structure by only using recordings with limited spatial resolution, which has hindered the investigation of the critical spatial scales for the reduction of consciousness. To address this issue, we recorded calcium signals from approximately 10,000 neurons across multiple cortical regions in awake, sleeping, and anesthetized mice and compared network structure at different spatial scales by leveraging single-cell resolution and wide-field two-photon microscopy. At the single-cell scale, both sleep and anesthesia exhibit higher network modularity than an awake state, indicating a segregated network, but modules are spatially intermixed in all three states.