Cisco Talos reports China-linked APT UAT-8837 targeting North American critical infrastructure via a Sitecore zero-day, abusing Active Directory and R.



Microsoft is investigating widespread reports that a January Windows 11 security update is causing the classic Outlook desktop client to freeze and hang for users with POP email accounts.
POP (Post Office Protocol) is an email retrieval protocol used for downloading emails from a server to a local device. While POP isn’t as widely used as IMAP or Exchange, it is still popular among home users and small businesses.
This known issue affects users who have installed the KB5074109 security update for Windows 11 25H2 and 24H2, with those impacted reporting that classic Outlook does not exit properly and will not restart after being closed.

A cross-site scripting (XSS) flaw in the web-based control panel used by operators of the StealC info-stealing malware allowed researchers to observe active sessions and gather intelligence on the attackers’ hardware.
StealC emerged in early 2023 with aggressive promotion on dark web cybercrime channels. It grew in popularity due to its evasion and extensive data theft capabilities.
In the following years, StealC’s developer added multiple enhancements. With the release of version 2.0 last April, the malware author introduced Telegram bot support for real-time alerts and a new builder that could generate StealC builds based on templates and custom data theft rules.

The identity of the Black Basta ransomware gang leader has been confirmed by law enforcement in Ukraine and Germany, and the individual has been added to the wanted list of Europol and Interpol.
Germany’s Federal Criminal Police Office (BKA) identified Oleg Evgenievich Nefedov, a 35-year-old Russian national, as the leader of the Black Basta ransomware gang.
The Ukrainian police in collaboration with German authorities also identified two additional individuals allegedly working for the ransomware operation and conducted raids at two locations in the Ivano-Frankivsk and Lviv regions.
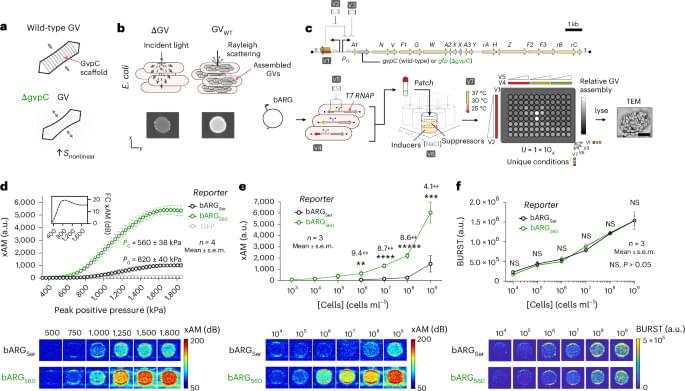
Great paper from Mikhail Shapiro’s lab where Nyström et al. used directed evolution methods to create protein gas vesicles which respond to distinct acoustic pressures, allowing for ultrasound imaging in two ‘colors’! Of note, Mikhail Shapiro is involved in the extremely exciting Merge Labs, which was publicly announced recently. [ https://www.nature.com/articles/s41592-025-02825-w](https://www.nature.com/articles/s41592-025-02825-w)
Ultrasound imaging with acoustic reporter genes has been limited to a single ‘tone’, restricting the types of experiments that can be achieved. This work introduces two acoustic reporter genes that enable multiplexed imaging in vitro and in mice.
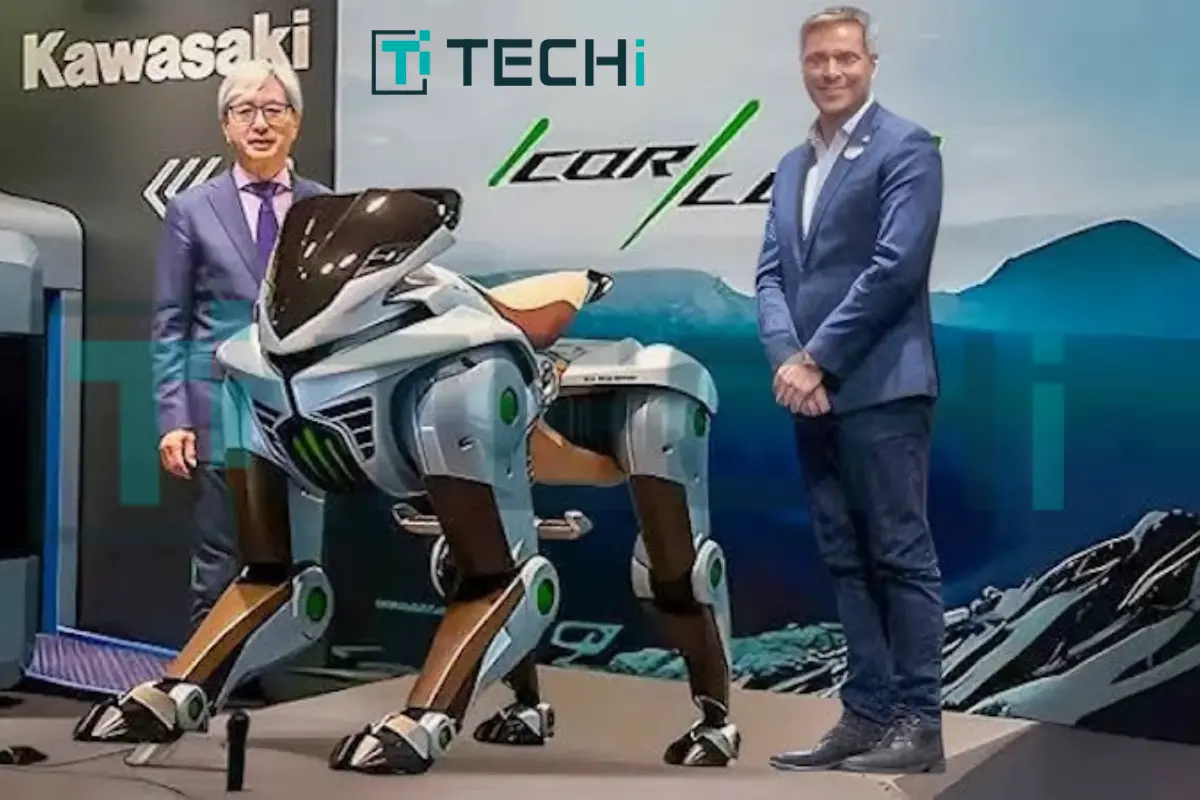
In a bold showcase of futuristic design and green innovation, Kawasaki Heavy Industries has unveiled the Kawasaki Corleo robot—a hydrogen-powered, four-legged robotic ride—at the Osaka-Kansai Expo 2025. This revolutionary concept reimagines mobility by blending clean energy, robotics, and artificial intelligence into a rider-ready machine that can walk, adapt, and navigate across rugged terrains.
The Kawasaki Corleo robot walks on four independently powered legs, offering impressive stability and terrain agility that wheels often can’t match. Built with carbon fiber and metal, Corleo echoes the iconic DNA of Kawasaki’s motorcycle lineage—featuring sleek contours, aerodynamic symmetry, and a headlight faceplate that resembles a mechanical creature ready to roam.
At the heart of Corleo lies a 150cc hydrogen engine that generates electricity to drive its limbs—making it a clean energy alternative to gas-powered off-roaders. Ditching the conventional handlebars, the robot interprets a rider’s body movement to move forward, turn, or stop. A built-in heads-up display (HUD) provides live feedback on hydrogen levels, motion stability, and terrain tracking. This unique interface between biomechanics and artificial intelligence makes the Kawasaki Corleo robot one of the most immersive robotic riding experiences developed to date.


Proteostasis in the lifespan of hematopoietic stem cells.
The hematopoietic system represents an excellent model to study how proteostasis (protein homeostasis) influences different cell types within the same tissue. This review focuses on mechanisms of proteostasis that preserve the lifespan of rare hematopoietic stem cells (HSCs).
Although most proteostasis network components are expressed in all cells, their activation and utilization are cell type-specific. HSCs maintain low translation rates and a preference for autophagy over proteasomal degradation to minimize protein stress.
To protect the integrity of the stem cell pool, HSCs are thought to respond to damage by clearing defective organelles and proteins or by eliminating compromised cells through differentiation or apoptosis.
A stressed proteome accelerates HSC aging, and the immune system derived from aged HSCs is suspected to contribute to the decline of other tissues. This highlights the importance of maintaining healthy HSCs to preserve organismal wellbeing.
Several experimental treatments in mouse models have been shown to boost HSC activity in older organisms by enhancing proteostasis.
This promising research opens up new possibilities for interventions that could improve aging through regenerative medicine. sciencenewshighlights ScienceMission https://sciencemission.com/longevity-from-blood-stem-cells