The Micius satellite has enabled messages with unbreakable encryption to be sent 1,200km.



Now, the same researchers have achieved their goal of entanglement-based quantum cryptography using the Micius satellite. The scientists, who detailed their findings online in the 15 June edition of the journal Nature, say they again connected two observatories separated by 1,120 kilometers. But this time, the collection efficiency of the links was improved by up to four-fold, which resulted in data rates of about 0.12 bits per second.
A space-based, virtually unhackable quantum Internet may be one step closer to reality due to satellite experiments that linked ground stations more than 1,000 kilometers apart, a new study finds.
Quantum physics makes a strange effect known as entanglement possible. Essentially, two or more particles such as photons that get linked or “entangled” can influence each other simultaneously no matter how far apart they are.
Entanglement is an essential factor in the operations of quantum computers, the networks that would connect them, and the most sophisticated kinds of quantum cryptography, a theoretically unhackable means of securing information exchange.

Quantum key distribution (QKD)1,2,3 is a theoretically secure way of sharing secret keys between remote users. It has been demonstrated in a laboratory over a coiled optical fibre up to 404 kilometres long4,5,6,7. In the field, point-to-point QKD has been achieved from a satellite to a ground station up to 1,200 kilometres away8,9,10. However, real-world QKD-based cryptography targets physically separated users on the Earth, for which the maximum distance has been about 100 kilometres11,12. The use of trusted relays can extend these distances from across a typical metropolitan area13,14,15,16 to intercity17 and even intercontinental distances18. However, relays pose security risks, which can be avoided by using entanglement-based QKD, which has inherent source-independent security19,20. Long-distance entanglement distribution can be realized using quantum repeaters21, but the related technology is still immature for practical implementations22. The obvious alternative for extending the range of quantum communication without compromising its security is satellite-based QKD, but so far satellite-based entanglement distribution has not been efficient23 enough to support QKD. Here we demonstrate entanglement-based QKD between two ground stations separated by 1,120 kilometres at a finite secret-key rate of 0.12 bits per second, without the need for trusted relays. Entangled photon pairs were distributed via two bidirectional downlinks from the Micius satellite to two ground observatories in Delingha and Nanshan in China. The development of a high-efficiency telescope and follow-up optics crucially improved the link efficiency. The generated keys are secure for realistic devices, because our ground receivers were carefully designed to guarantee fair sampling and immunity to all known side channels24,25. Our method not only increases the secure distance on the ground tenfold but also increases the practical security of QKD to an unprecedented level.

Physicists set a new record by linking together a hot soup of 15 trillion atoms in a bizarre phenomenon called quantum entanglement. The finding could be a major breakthrough for creating more accurate sensors to detect ripples in space-time called gravitational waves or even the elusive dark matter thought to pervade the universe.
Entanglement, a quantum phenomena Albert Einstein famously described as “spooky action at a distance,” is a process in which two or more particles become linked and any action performed on one instantaneously affects the others regardless of how far apart they are. Entanglement lies at the heart of many emerging technologies, such as quantum computing and cryptography.

The fast and efficient generation of random numbers has long been an important challenge. For centuries, games of chance have relied on the roll of a die, the flip of a coin, or the shuffling of cards to bring some randomness into the proceedings. In the second half of the 20th century, computers started taking over that role, for applications in cryptography, statistics, and artificial intelligence, as well as for various simulations—climatic, epidemiological, financial, and so forth.

As far back as 2015, the National Institute of Standards and Technology (NIST) began asking encryption experts to submit their candidate algorithms for testing against quantum computing’s expected capabilities — so this is an issue that has already been front of mind for security professionals and organizations. But even with an organization like NIST leading the way, working through all those algorithms to judge their suitability to the task will take time. Thankfully, others within the scientific community have also risen to the challenge and joined in the research.
It will take years for a consensus to coalesce around the most suitable algorithms. That’s similar to the amount of time it took ECC encryption to gain mainstream acceptance, which seems like a fair comparison. The good news is that such a timeframe still should leave the opportunity to arrive at — and widely deploy — quantum-resistant cryptography before quantum computers capable of sustaining the number of qubits necessary to seriously threaten RSA and ECC encryption become available to potential attackers.
The ongoing development of quantum-resistant encryption will be fascinating to watch, and security professionals will be sure to keep a close eye on which algorithms and encryption strategies ultimately prove most effective. The world of encryption is changing more quickly than ever, and it has never been more important for the organizations dependent on that encryption to ensure that their partners are staying ahead of the curve.
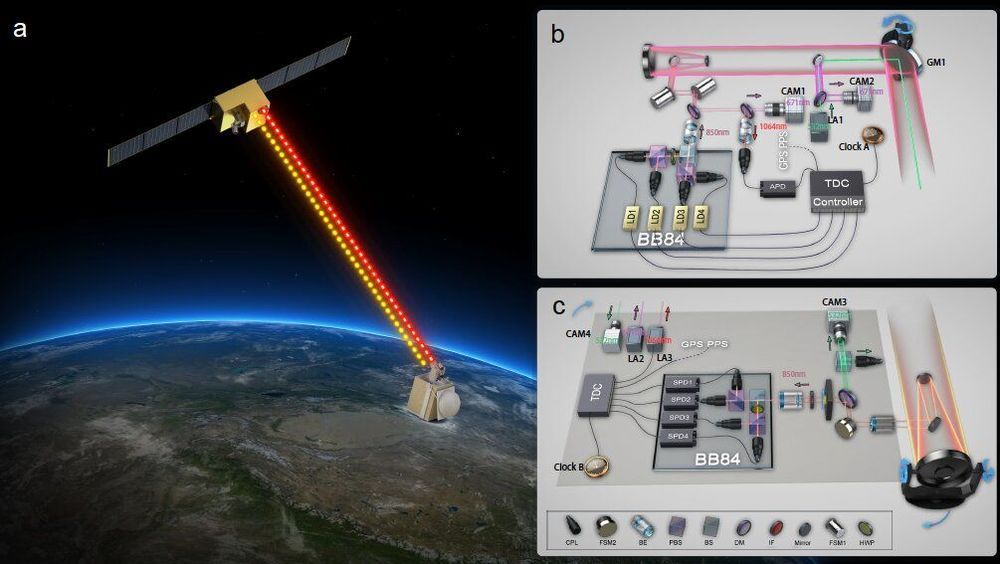
Researchers at the University of Science and Technology of China have recently introduced a new satellite-based quantum-secure time transfer (QSTT) protocol that could enable more secure communications between different satellites or other technology in space. Their protocol, presented in a paper published in Nature Physics, is based on two-way quantum key distribution in free space, a technique to encrypt communications between different devices.
“Our main idea was to realize quantum-secure time transfer in order to resolve the security issues in practical time–frequency transfer,” Feihu Xu, one of the researchers who carried out the study, told Phys.org.
Quantum key distribution (QKD) is a technique to achieve secure communication that utilize cryptographic protocols based on the laws of quantum mechanics. Quantum key distribution protocols can generate secret security keys based on quantum physics, enabling more secure data transfer between different devices by spotting attackers who are trying to intercept communications.
Essentially a quantum radar teleportation device could entangle objects anywhere in the universe.
Last year, a Long March 2D rocket took off from the Jiuquan Satellite Launch Centre in the Gobi Desert carrying a satellite called Micius, named after an ancient Chinese philosopher who died in 391 B.C. The rocket placed Micius in a Sun-synchronous orbit so that it passes over the same point on Earth at the same time each day.
Micius is a highly sensitive photon receiver that can detect the quantum states of single photons fired from the ground. That’s important because it should allow scientists to test the technological building blocks for various quantum feats such as entanglement, cryptography, and teleportation.
April 2020
Field programmable gate arrays, FPGAs for short, are flexibly programmable computer chips that are considered very secure components in many applications. In a joint research project, scientists from the Horst Görtz Institute for IT Security at Ruhr-Universität Bochum and from Max Planck Institute for Security and Privacy have now discovered that a critical vulnerability is hidden in these chips. They called the security bug “Starbleed.” Attackers can gain complete control over the chips and their functionalities via the vulnerability. Since the bug is integrated into the hardware, the security risk can only be removed by replacing the chips. The manufacturer of the FPGAs has been informed by the researchers and has already reacted.
The security researchers will present the results of their work at the 29th Usenix Security Symposium to be held in August 2020 in Boston, Massachusetts, U.S… The scientific paper has been available for download on the Usenix website since April 15, 2020.
Focus on the bitstream
FPGA chips can be found in many safety-critical applications today, from cloud data centers and mobile phone base stations to encrypted USB-sticks and industrial control systems. Their decisive advantage lies in their reprogrammability compared to conventional hardware chips with their fixed functionalities.

Samsung has a hardened version of the Galaxy S20, but don’t reach for your credit card — it’s not what you were expecting, and you probably can’t get one. The company has introduced a Galaxy S20 Tactical Edition that, as the name suggests, is designed to meet the needs of the US military and federal government. It touts two layers of encryption strong enough to handle top secret data and connects to tactical radios and mission systems out of the box.
There are combat-related conveniences, too. One mode can turn the display on and off while you’re wearing night vision goggles, while a stealth mode turns off LTE and and mutes all RF broadcasts to eliminate even the slightest chance of eavesdropping. It’s also easy to unlock the phone in landscape mode so that you can quickly launch an app while the device is mounted to your chest.
This is otherwise a run-of-the-mill Galaxy S20 with a 6.2-inch, 1440p display, a Snapdragon 865 processor, 12GB of RAM, 128GB of expandable storage, a 4,000mAh battery and the usual arrays of front and rear cameras. Although Samsung shows the Tactical Edition in a rugged casing, there’s no mention of the phone itself being rugged.