Let’s Encrypt has warned that older Android phones won’t support many secure websites after they lose key certificates by September 2021.



Quantum computers are now a reality, although they are still too rudimentary to factor numbers of more than two digits. But it is only a matter of time until quantum computers threaten Internet encryption.
Nature caught up with Shor to ask him about the impact of his work — and where Internet security is heading.
Nature talks to Peter Shor 25 years after he showed how to make quantum computations feasible — and how they could endanger our data.


Chinese spies are different from those of most other wealthy and developed countries where the majority of spies are highly trained, with some serving under diplomatic cover and others operating under what the US Intelligence Community calls Non Official Cover (NOC).
Chinese intelligence operations are the first in modern times to use, as a foundation, the whole of society. Because of this, China’s espionage tactics are sometimes artless, operating with little in the way of standard spy-fare, (encrypted communication, dead drops, etc.) instead relying on an overwhelming volume of espionage operations conducted by all manner of citizen and a sort of impunity inherent in the lack of substantive penalty for when a Chinese agent is discovered, a study I recently published analyzing 595 cases of intelligence collection efforts sanctioned and abetted by the Chinese Communist Party.
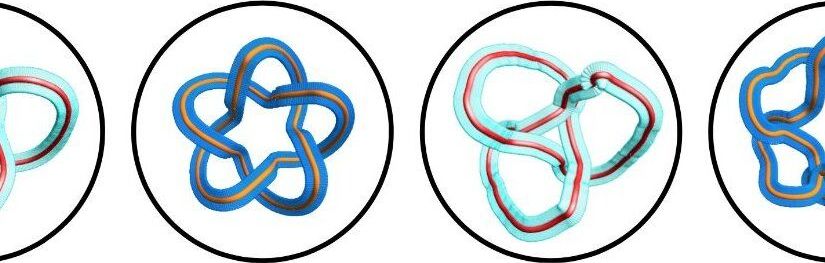
In a world first, researchers from the University of Ottawa in collaboration with Israeli scientists have been able to create optical framed knots in the laboratory that could potentially be applied in modern technologies. Their work opens the door to new methods of distributing secret cryptographic keys—used to encrypt and decrypt data, ensure secure communication and protect private information. The group recently published their findings in Nature Communications.
“This is fundamentally important, in particular from a topology-focused perspective, since framed knots provide a platform for topological quantum computations,” explained senior author, Professor Ebrahim Karimi, Canada Research Chair in Structured Light at the University of Ottawa.
“In addition, we used these non-trivial optical structures as information carriers and developed a security protocol for classical communication where information is encoded within these framed knots.”

 In the race to launch smallsats into low earth orbit quickly and cost-effectively, operators and manufacturers have compromised on security and left themselves vulnerable to cyber attacks. Let’s not make Newspace a paradise for hackers.
In the race to launch smallsats into low earth orbit quickly and cost-effectively, operators and manufacturers have compromised on security and left themselves vulnerable to cyber attacks. Let’s not make Newspace a paradise for hackers.
Smallsat operators and manufacturers need to consider why their smallsats are so vulnerable to cyber attacks, the harm attacks can cause, cyber security weaknesses, why basic encryption is not enough and what can be done about it now. These are the issues that this article addresses.
(Nanowerk News) Quantum technology holds great promise: Just a few years from now, quantum computers are expected to revolutionize database searches, AI systems, and computational simulations. Today already, quantum cryptography can guarantee absolutely secure data transfer, albeit with limitations. The greatest possible compatibility with our current silicon-based electronics will be a key advantage. And that is precisely where physicists from the Helmholtz-Zentrum Dresden-Rossendorf (HZDR) and TU Dresden have made remarkable progress: The team has designed a silicon-based light source to generate single photons that propagate well in glass fibers.
O,.o.
BT and Toshiba have deployed an ‘unhackable’ quantum network that uses streams of photons to encrypt sensitive communications.
A trial of the network, which is the first of its kind in the UK, will see data transmitted between two engineering facilities in Bristol using encryption keys streamed as ‘encoded’ particles of light.
The world is one step closer to having a totally secure internet and an answer to the growing threat of cyber-attacks, thanks to a team of international scientists who have created a unique prototype that could transform how we communicate online.
The invention led by the University of Bristol, revealed today in the journal Science Advances, has the potential to serve millions of users, is understood to be the largest-ever quantum network of its kind, and could be used to secure people’s online communication, particularly in these internet-led times accelerated by the COVID-19 pandemic.
DARPA announces a new type of cryptography to protect the Big Tech firm profits from the dawn of quantum computers and allow backdoor access into 3 trillion internet-connected devices.
by Raul Diego
The U.S. Military-Industrial complex is sprinting on a chariot to shore up the encryption space before the next era of computation upends the entire digital edifice built on semiconductors and transistors. But, the core of the effort is protecting markets for Big Tech and all of its tentacles, which stand to lose years or even decades of profits should the new tech be rolled out too quickly.