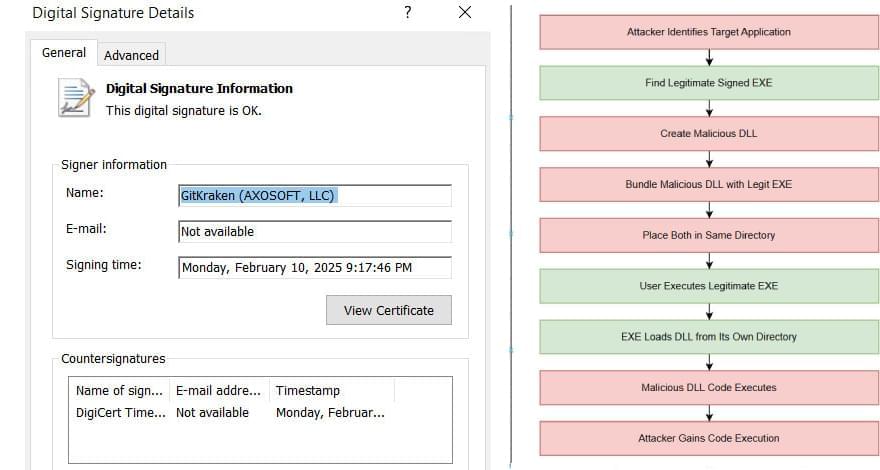
Security experts have disclosed details of an active malware campaign that’s exploiting a DLL side-loading vulnerability in a legitimate binary associated with the open-source c-ares library to bypass security controls and deliver a wide range of commodity trojans and stealers.
“Attackers achieve evasion by pairing a malicious libcares-2.dll with any signed version of the legitimate ahost.exe (which they often rename) to execute their code,” Trellix said in a report shared with The Hacker News. “This DLL side-loading technique allows the malware to bypass traditional signature-based security defenses.”
The campaign has been observed distributing a wide assortment of malware, such as Agent Tesla, CryptBot, Formbook, Lumma Stealer, Vidar Stealer, Remcos RAT, Quasar RAT, DCRat, and XWorm.