Cisco Talos links China-based UAT-8099 to IIS server attacks using BadIIS malware for regional SEO fraud, targeting Thailand and Vietnam.



IPIDEA, one of the largest residential proxy networks used by threat actors, was disrupted earlier this week by Google Threat Intelligence Group (GTIG) in collaboration with industry partners.
The action included taking down domains associated with IPIDEA services, infected device management, proxy traffic routing. Additionally, intelligence has been shared on the IPIDEA software development kits (SDK) that distributed the proxying tool.
The operators of IPIDEA advertised it as a VPN service that “encrypts your online traffic and hides your real IP address,” used by 6.7 million users worldwide.

A new Android malware campaign is using the Hugging Face platform as a repository for thousands of variations of an APK payload that collects credentials for popular financial and payment services.
Hugging Face is a popular platform that hosts and distributes artificial intelligence (AI), natural language processing (NLP), and machine learning (ML) models, datasets, and applications.
It is considered a trusted platform unlikely to trigger security warnings, but bad actors have abused it in the past to host malicious AI models.


The Aisuru/Kimwolf botnet launched a new massive distributed denial of service (DDoS) attack that peaked at 31.4 Tbps and 200 million requests per second, setting a new record.
The attack was part of a campaign targeting multiple companies, most of them in the telecommunications sector, and was detected and mitigated by Cloudflare last year on December 19.
Aisuru is responsible for the previous DDoS record that reached 29.7 Tbps. Another attack that Microsoft attributed to the botnet peaked at 15.72 Tbps and originated from 500,000 IP addresses.


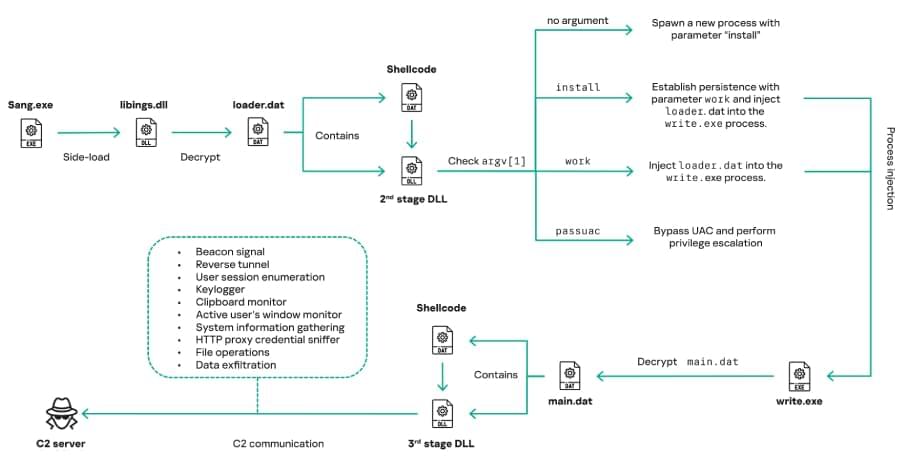

A prolific initial access broker tracked as TA584 has been observed using the Tsundere Bot alongside XWorm remote access trojan to gain network access that could lead to ransomware attacks.
Proofpoint researchers have been tracking TA584’s activity since 2020 and say that the threat actor has significantly increased its operations recently, introducing a continuous attack chain that undermines static detection.
Tsundere Bot was first documented by Kaspersky last year and attributed to a Russian-speaking operator with links to the 123 Stealer malware.