This case report describes a man presenting with amnestic seizure events manifesting with a wind swirl pattern on density spectral array, resulting in a diagnosis of anti–γ-aminobutyric acid B (GABAB) receptor antibody–associated encephalitis.


Malaria continues to place a substantial burden on many emerging economies, contributing to significant loss of life, long-term disability, and economic disruption. According to the World Health Organization, the disease accounts for about 600,000 deaths each year, with the highest impact in low- and middle-income regions where access to prompt diagnosis and treatment remains limited.
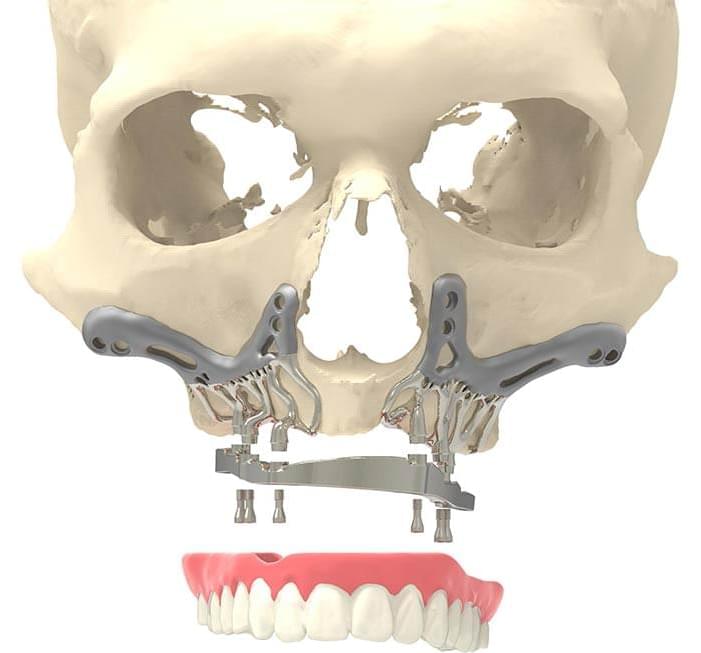
CADskills is a medical device startup based in Ghent, Belgium. Their expertise lies in patient-specific implants, with a focus on CMF and neurosurgery patients. What is putting them in Materialise’s spotlight however, is their AMSJI: a revolutionary 3D-printed titanium jaw implant that will make life better for extreme maxillary atrophy sufferers. Now there’s something to […]
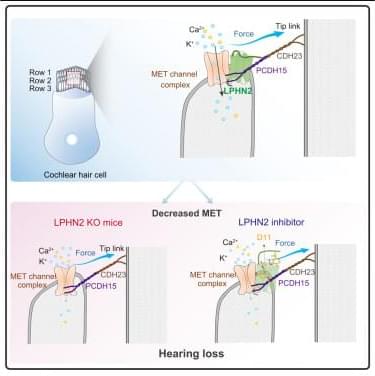
The mechanosensitive LPHN2 expressed at the tips of stereocilia in cochlear hair cells is identified as a modulator in the auditory process by interacting with MET channel components, which contributes to the Ca2+ response and neurotransmitter release in cochlear hair cells in response to mechanical stimulation.
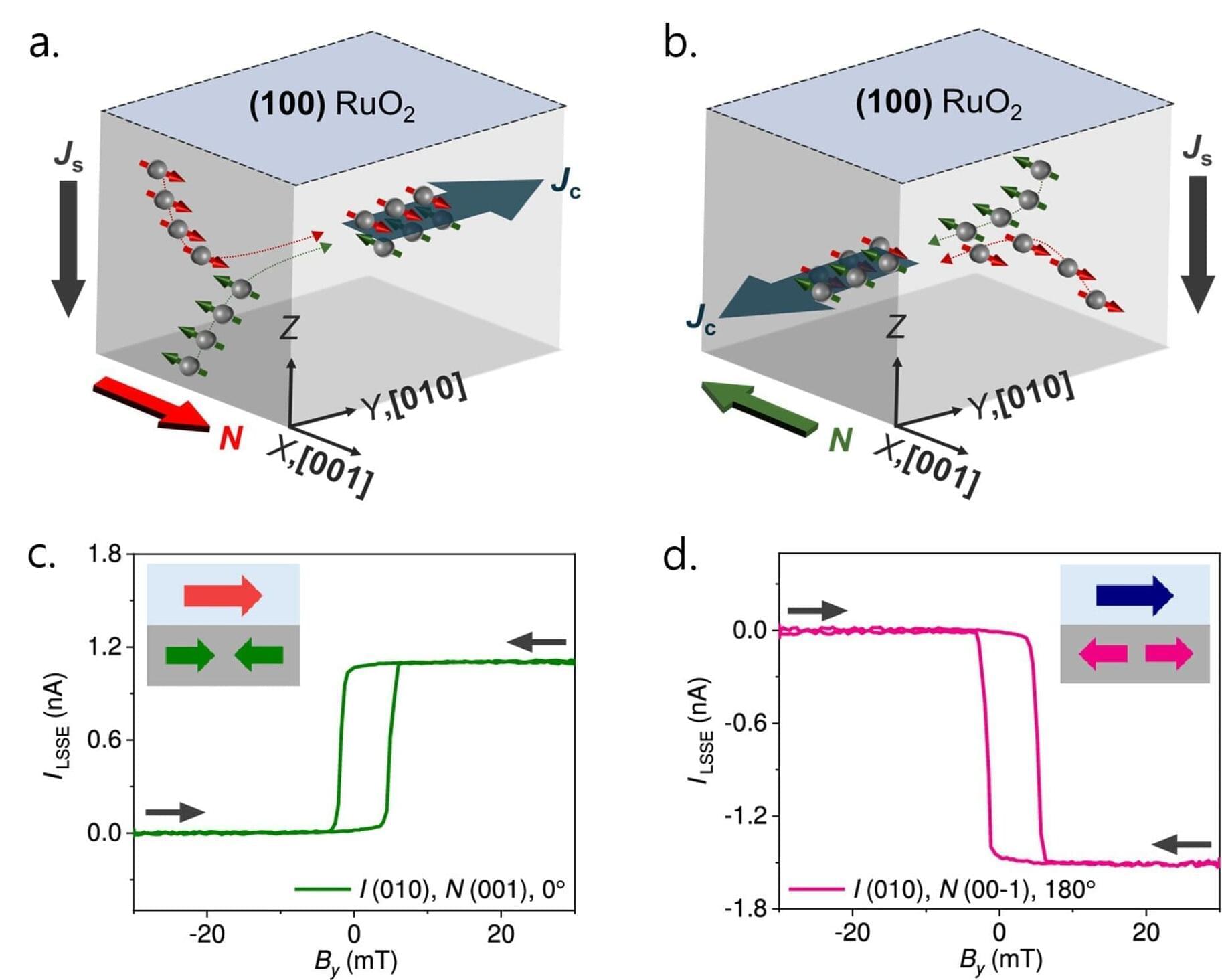
A research team affiliated with UNIST has made a advancement in controlling spin-based signals within a new magnetic material, paving the way for next-generation electronic devices. Their work demonstrates a method to reversibly switch the direction of spin-to-charge conversion, a key step toward ultra-fast, energy-efficient spintronic semiconductors that do not require complex setups or strong magnetic fields.
Led by Professor Jung-Woo Yoo from the Department of Materials Science and Engineering and Professor Changhee Sohn from the Department of Physics at UNIST, the team has experimentally shown that within the altermagnetic material ruthenium oxide (RuO₂), the process of converting spin currents into electrical signals can be precisely controlled and flipped at will.
This breakthrough is expected to accelerate the development of low-power devices capable of processing information more efficiently than current technologies. The study is published in the journal Nano Letters.

Diamonds aren’t quite forever… but they’re damn close.

Lung cancer cells metastasizing to the brain can form real electrical synapses with neurons, not just hijack brain space — a discovery that may open new therapeutic targets. Researchers found that neuronal activity actually spurs tumor growth and that drugs reducing neuron signaling could slow cancer proliferation.
Two teams discover how small cell lung cancer hijacks neural pathways to proliferate faster, especially to the brain. Common neuro drugs could be the answer.
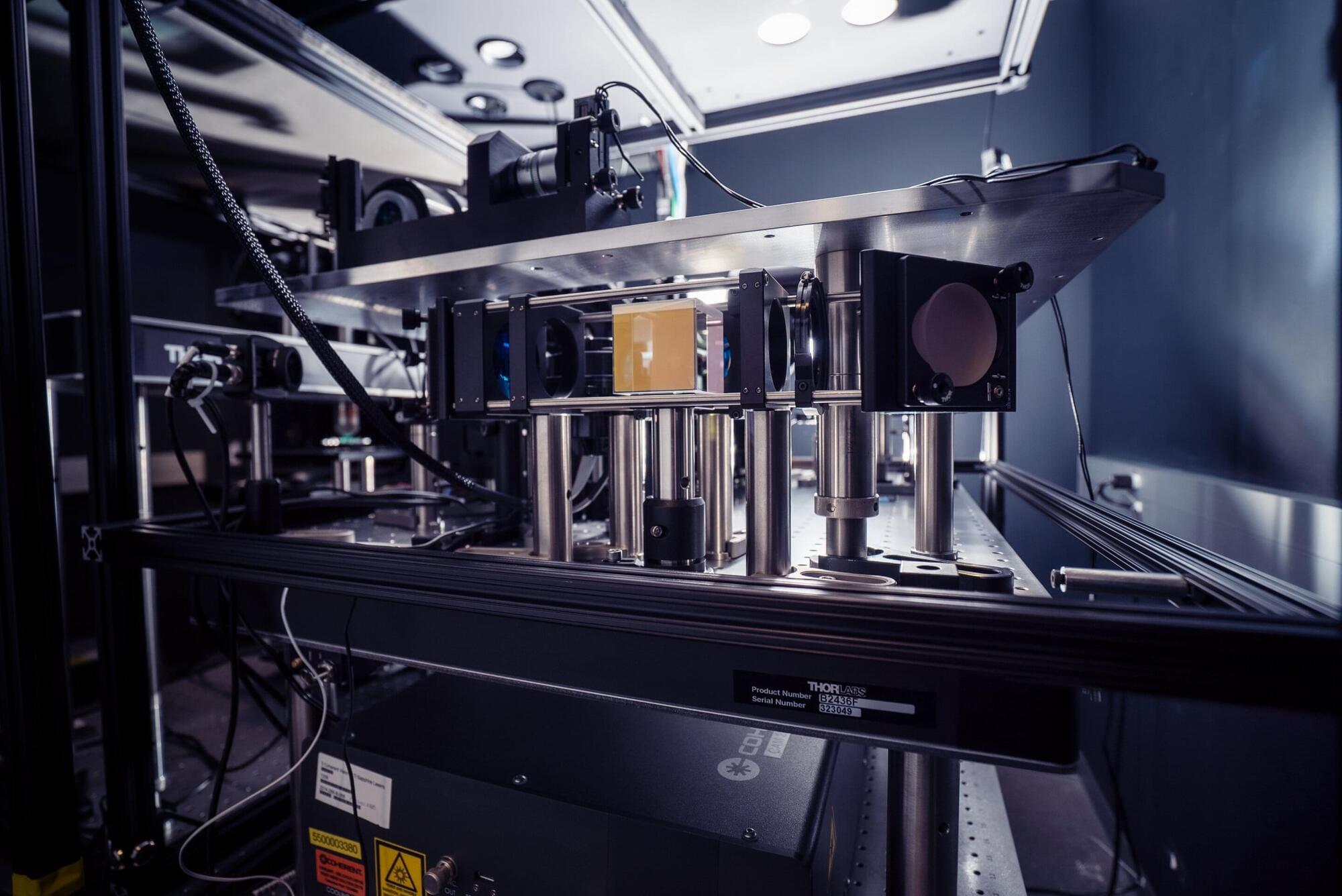
Scientists have engineered a protein able to record the incoming chemical signals of brain cells (as opposed to just their outgoing signals). These whisper-quiet incoming messages are the release of the neurotransmitter glutamate, which plays a critical role in how brain cells communicate with one another but until now has been extremely difficult to capture.
The findings are published in Nature Methods and could transform how neuroscience research is done as it pertains to measuring and analyzing neural activity.
The special protein that researchers at the Allen Institute and HHMI’s Janelia Research Campus have engineered is a molecular “glutamate indicator” called iGluSnFR4 (pronounced ‘glue sniffer’). It’s sensitive enough to detect the faintest incoming signals between neurons in the brain, offering a new way to decipher and interpret their complex cascade of electrical activity that underpins learning, memory, and emotion. iGluSnFR4 could help decode the hidden language of the brain and deepen our understanding of how its complex circuitry works. This discovery allows researchers to watch neurons in the brain communicate in real time.