Researchers at Northwestern University have developed a garment designed to confuse digital surveillance algorithms into thinking you don’t exist.


Reason has done a great video and article on AI facial recognition, surveillance, etc, and combined it with fashion ideas. It’s created by Zach Weissmueller and Justin Monticello. My interview (as well as others) show up throughout the 11 min video. This is really important watching for the coming future:
Privacy activists say we should be alarmed by the rise of automated facial recognition surveillance. Transhumanist Zoltan Istvan says it’s time to embrace the end of privacy as we know it.

Lockheed Martin’s Advanced Development Programs, known as Skunk Works, has demonstrated an artificial intelligence-powered intelligence, surveillance and reconnaissance (ISR) pod autonomously searching out and confirming a target.
The demonstration was conducted at Edwards Air Force Base in California using an ISR pod mounted on a Lockheed Martin F-16 fighter, says the company on 8 May. The demonstration was conducted in Air Force Test Pilot School.

WASHINGTON — SpaceX on May 6 was awarded an $8.9 million contract modification that gives the U.S. Space Force direct insight into the inner workings of the company’s commercial and civil space missions.
The contract for “non-National Security Space fleet surveillance” gives the Space Force access to SpaceX missions until November.
“This contract provides for non-NSS fleet surveillance efforts across the SpaceX family of launch vehicles for non-NSS missions,” said the contract announcement. The $8.9 million is an addition to an existing $297 million contract awarded to SpaceX in February 2019 for three national security launches.

The debate is focused on a subset of gain-of-function studies that manipulate deadly viruses to increase their transmissibility or virulence. “This is what happens to viruses in the wild”, explains Carrie Wolinetz, head of the NIH Office of Science Policy. “Gain-of-function experiments allow us to understand how pandemic viruses evolve, so that we can make predictions, develop countermeasures, and do disease surveillance”. Although none of the widely publicised mishaps of 2014 involved such work, the NIH decided to suspend funding for gain-of-function studies involving influenza, MERS-CoV, and SARS-CoV.
The US moratorium on gain-of-function experiments has been rescinded, but scientists are split over the benefits—and risks—of such studies. Talha Burki reports.
On Dec 19, 2017, the US National Institutes of Health (NIH) announced that they would resume funding gain-of-function experiments involving influenza, Middle East respiratory syndrome coronavirus, and severe acute respiratory syndrome coronavirus. A moratorium had been in place since October, 2014. At the time, the NIH had stated that the moratorium “will be effective until a robust and broad deliberative process is completed that results in the adoption of a new US Government gain-of-function research policy”. This process has now concluded. It was spearheaded by the National Science Advisory Board for Biosecurity (NSABB) and led to the development of a new framework for assessing funding decisions for research involving pathogens with enhanced pandemic potential. The release of the framework by the Department of Health and Human Services (HHS), of which NIH is part, signalled the end of the funding pause.
The situation has its roots in 2011, when the NSABB suppressed two studies involving H5N1 viruses that had been modified to allow airborne transmission from ferret to ferret. They worried that malign actors could replicate the work to deliberately cause an outbreak in human beings. After much debate, the studies were published in full in 2012. HHS subsequently issued guidelines for funding decisions on experiments likely to result in highly pathogenic H5N1 viruses transmissible from mammal to mammal via respiratory droplets. The guidelines were later expanded to include H7N9 viruses.
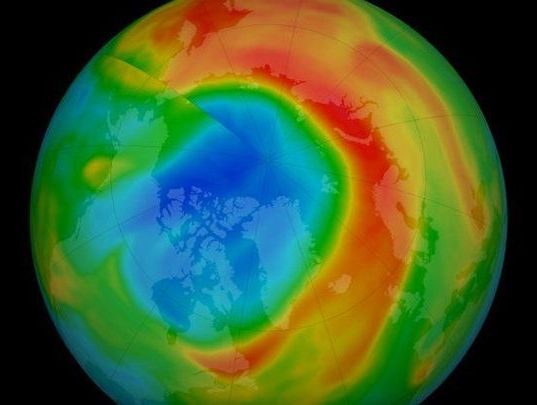
Earlier this year, the layer of ozone over the Arctic thinned out enough to be considered a serious sized hole. It wasn’t exactly impressive compared with its southern cousin, but it was certainly a lot bigger than we’d ever seen it before.
Now, according to surveillance by the Copernicus Atmosphere Monitoring Service (CAMS), we can breathe a sigh of relief. It’s healed up again.
That’s great news for ecosystems below, which rely on concentrations of ozone gas high up in the stratosphere to act as a planetary-scale sunscreen against damaging showers of UV radiation.
This robot is a drone and a generator that can go on surveillance missions. Is there anything it can’t do?

In partnership with the Australian Ministry of Defense, the U.S. Space Force’s (USSF) Space and Missile Systems Center’s (SMC) Space Surveillance Telescope (SST) Program recently achieved “first light” on March 5, 2020, reaching a key milestone after it was moved from White Sands Missile Range, New Mexico to Harold E. Holt Naval Communications Station in Western Australia.
“This key Space Domain Awareness, or SDA, partnership builds on the long history of close defense space cooperation between the United States and Australia and has been a cornerstone of our continued alliance,” said Gordon Kordyak, SMC Special Programs Directorate Space Domain Awareness Division chief.
Moving the SST to Australia satisfied a critical objective to improve the broader USSF Space Surveillance Network’s ground-based electro-optical coverage of the geosynchronous space regime. First light is a significant milestone in meeting this objective. It means that course alignment of the telescope optics with the wide field of view camera has been completed to allow the first images of objects in orbit to be seen by the telescope.

During World War II, an amazing amount of innovation, including radar, reliable torpedoes, and code-breaking, helped end the war faster. This will be the same with the pandemic. I break the innovation into five categories: treatments, vaccines, testing, contact tracing, and policies for opening up. Without some advances in each of these areas, we cannot return to the business as usual or stop the virus. Below, I go through each area in some detail.
The scientific advances we need to stop COVID-19.
By Bill Gates
Pew-pew-pew is coming soon-soon-soon.
The U.S. Navy plans to put a laser weapon on a warship by 2021. The High Energy Laser with Integrated Optical-dazzler and Surveillance (HELIOS) system, or HELIOS, is a defensive weapon system designed to burn boats and shoot down unmanned drones. The weapon will go to sea with a guided missile destroyer assigned to the Pacific Fleet in two years’ time, the Navy says.
The service placed an order for HELIOS in January 2019. The $150 million contract, awarded to Lockheed Martin, calls for the company to deliver two systems. According to a company press release, one will go to White Sands Missile Range in New Mexico for testing. USNI News says the Navy will install the other on a Arleigh Burke-class guided missile destroyer.