Attackers are exploiting two CVSS 9.8 FortiGate SSO authentication bypass flaws days after disclosure; Fortinet urges immediate patching.



The Texas Attorney General sued five major television manufacturers, accusing them of illegally collecting their users’ data by secretly recording what they watch using Automated Content Recognition (ACR) technology.
The lawsuits target Sony, Samsung, LG, and China-based companies Hisense and TCL Technology Group Corporation. Attorney General Ken Paxton’s office also highlighted “serious concerns” about the two Chinese companies being required to follow China’s National Security Law, which could give the Chinese government access to U.S. consumers’ data.
According to complaints filed this Monday in Texas state courts, the TV makers can allegedly use ACR technology to capture screenshots of television displays every 500 milliseconds, monitor the users’ viewing activity in real time, and send this information back to the companies’ servers without the users’ knowledge or consent.

Microsoft says that recent Windows 11 security updates are causing VPN networking failures for enterprise users running Windows Subsystem for Linux.
This known issue affects users who installed the KB5067036 October 2025 non-security update, released October 28th, or any subsequent updates, including the KB5072033 cumulative update released during this month’s Patch Tuesday.
On impacted systems, users are experiencing connectivity issues with some third-party VPN applications when mirrored mode networking is enabled, preventing access to corporate resources.

University of Iowa scientists have identified a new way to “purify” photons, a development that could improve both the efficiency and security of optical quantum technologies.
The team focused on two persistent problems that stand in the way of producing a reliable stream of single photons, which are essential for photonic quantum computers and secure communication systems. The first issue, known as laser scatter, arises when a laser is aimed at an atom to trigger the release of a photon, the basic unit of light. Although this method successfully generates photons, it can also produce extra, unwanted ones. These additional photons reduce the efficiency of the optical system, similar to how stray electrical currents interfere with electronic circuits.
A second complication comes from the way atoms occasionally respond to laser light. In uncommon cases, an atom releases more than one photon at the same time. When this happens, the precision of the optical circuit suffers because the extra photons disrupt the intended orderly flow of single photons.

Audio streaming platform SoundCloud has confirmed that outages and VPN connection issues over the past few days were caused by a security breach in which threat actors stole a database exposing users’ email addresses and profile information.
The disclosure follows widespread reports over the past four days from users who were unable to access SoundCloud when connecting via VPN, with attempts resulting in the site displaying 403 “forbidden” errors.
In a statement shared with BleepingComputer, SoundCloud said it recently detected unauthorized activity involving an ancillary service dashboard and activated its incident response procedures.
Free unofficial patches are available for a new Windows zero-day vulnerability that allows attackers to crash the Remote Access Connection Manager (RasMan) service.
RasMan is a critical Windows system service that starts automatically, runs in the background with SYSTEM-level privileges, and manages VPN, Point-to-Point Protocol over Ethernet (PPoE), and other remote network connections.
ACROS Security (which manages the 0patch micropatching platform) discovered a new denial-of-service (DoS) flaw while looking into CVE-2025–59230, a Windows RasMan privilege escalation vulnerability exploited in attacks that was patched in October.

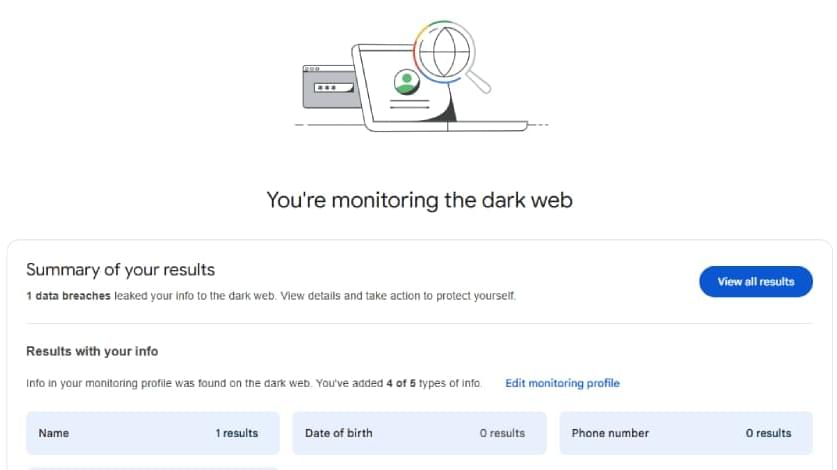
Google is discontinuing its “dark web report” security tool, stating that it wants to focus on other tools it believes are more helpful.
Google’s dark web report tool is a security feature that notifies users if their email address or other personal information was found on the dark web.
After Google scans the dark web and identifies your personal information, it will notify you where the data was found and what type of data was exposed, encouraging users to take action to protect their data.

