New Airstalk malware hijacks AirWatch APIs in stealth supply chain attack, targeting enterprise browsers.



The activity targeted diplomatic organizations in Hungary, Belgium, Italy, and the Netherlands, as well as government agencies in Serbia, Arctic Wolf said in a technical report published Thursday.
“The attack chain begins with spear-phishing emails containing an embedded URL that is the first of several stages that lead to the delivery of malicious LNK files themed around European Commission meetings, NATO-related workshops, and multilateral diplomatic coordination events,” the cybersecurity company said.
The files are designed to exploit ZDI-CAN-25373 to trigger a multi-stage attack chain that culminates in the deployment of the PlugX malware using DLL side-loading. PlugX is a remote access trojan that’s also referred to as Destroy RAT, Kaba, Korplug, SOGU, and TIGERPLUG.

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) and National Security Agency (NSA), along with international partners from Australia and Canada, have released guidance to harden on-premise Microsoft Exchange Server instances from potential exploitation.
“By restricting administrative access, implementing multi-factor authentication, enforcing strict transport security configurations, and adopting zero trust (ZT) security model principles, organizations can significantly bolster their defenses against potential cyber attacks,” CISA said.
The agencies said malicious activity aimed at Microsoft Exchange Server continues to take place, with unprotected and misconfigured instances facing the brunt of the attacks. Organizations are advised to decommission end-of-life on-premises or hybrid Exchange servers after transitioning to Microsoft 365.

CISA confirmed on Thursday that a high-severity privilege escalation flaw in the Linux kernel is now being exploited in ransomware attacks.
While the vulnerability (tracked as CVE-2024–1086) was disclosed on January 31, 2024, as a use-after-free weakness in the netfilter: nf_tables kernel component and was fixed via a commit submitted in January 2024, it was first introduced by a decade-old commit in February 2014.
Successful exploitation enables attackers with local access to escalate privileges on the target system, potentially resulting in root-level access to compromised devices.

A 68-year-old woman with relapsed acute myeloid leukemia (AML) underwent what appears to be the first successful stem cell transplant using stem cells recovered from a deceased donor. The procedure was performed at Henry Ford Health in Detroit and is notable because it may expand access for people who cannot find a suitable living donor, a barrier that mainly affects people from racial and ethnic minorities.
First-in-world marrow transplant from a deceased donor and what trials mean for access and timelines.

Kolmogorov-Arnold Networks (KANs) have recently emerged as a promising alternative to traditional Multilayer Perceptrons (MLPs), inspired by the Kolmogorov-Arnold representation theorem. Unlike MLPs, which use fixed activation functions on nodes, KANs employ learnable univariate basis functions on edges, offering enhanced expressivity and interpretability. This review provides a systematic and comprehensive overview of the rapidly expanding KAN landscape, moving beyond simple performance comparisons to offer a structured synthesis of theoretical foundations, architectural variants, and practical implementation strategies. By collecting and categorizing a vast array of open-source implementations, we map the vibrant ecosystem supporting KAN development. We begin by bridging the conceptual gap between KANs and MLPs, establishing their formal equivalence and highlighting the superior parameter efficiency of the KAN formulation. A central theme of our review is the critical role of the basis function; we survey a wide array of choices, including B-splines, Chebyshev and Jacobi polynomials, ReLU compositions, Gaussian RBFs, and Fourier series, and analyze their respective trade-offs in terms of smoothness, locality, and computational cost. We then categorize recent advancements into a clear roadmap, covering techniques for improving accuracy, efficiency, and regularization. Key topics include physics-informed loss design, adaptive sampling, domain decomposition, hybrid architectures, and specialized methods for handling discontinuities. Finally, we provide a practical “Choose-Your-KAN” guide to help practitioners select appropriate architectures, and we conclude by identifying current research gaps. The associated GitHub repository https://github.com/AmirNoori68/kan-review complements this paper and serves as a structured reference for ongoing KAN research.
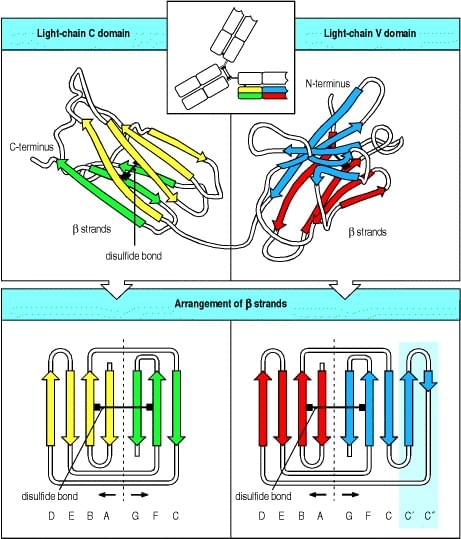
3.3). This produces a fragment, the F(ab′)2 fragment, in which the two antigen-binding arms of the antibody molecule remain linked. In this case the remaining part of the heavy chain is cut into several small fragments. The F(ab′)2 fragment has exactly the same antigen-binding characteristics as the original antibody but is unable to interact with any effector molecule. It is thus of potential value in therapeutic applications of antibodies as well as in research into the functional role of the Fc portion.
Genetic engineering techniques also now permit the construction of many different antibody-related molecules. One important type is a truncated Fab comprising only the V domain of a heavy chain linked by a stretch of synthetic peptide to a V domain of a light chain. This is called single-chain Fv, named from Fragment v ariable. Fv molecules may become valuable therapeutic agents because of their small size, which allows them to penetrate tissues readily. They can be coupled to protein toxins to yield immunotoxins with potential application, for example, in tumor therapy in the case of a Fv specific for a tumor antigen (see Chapter 14).

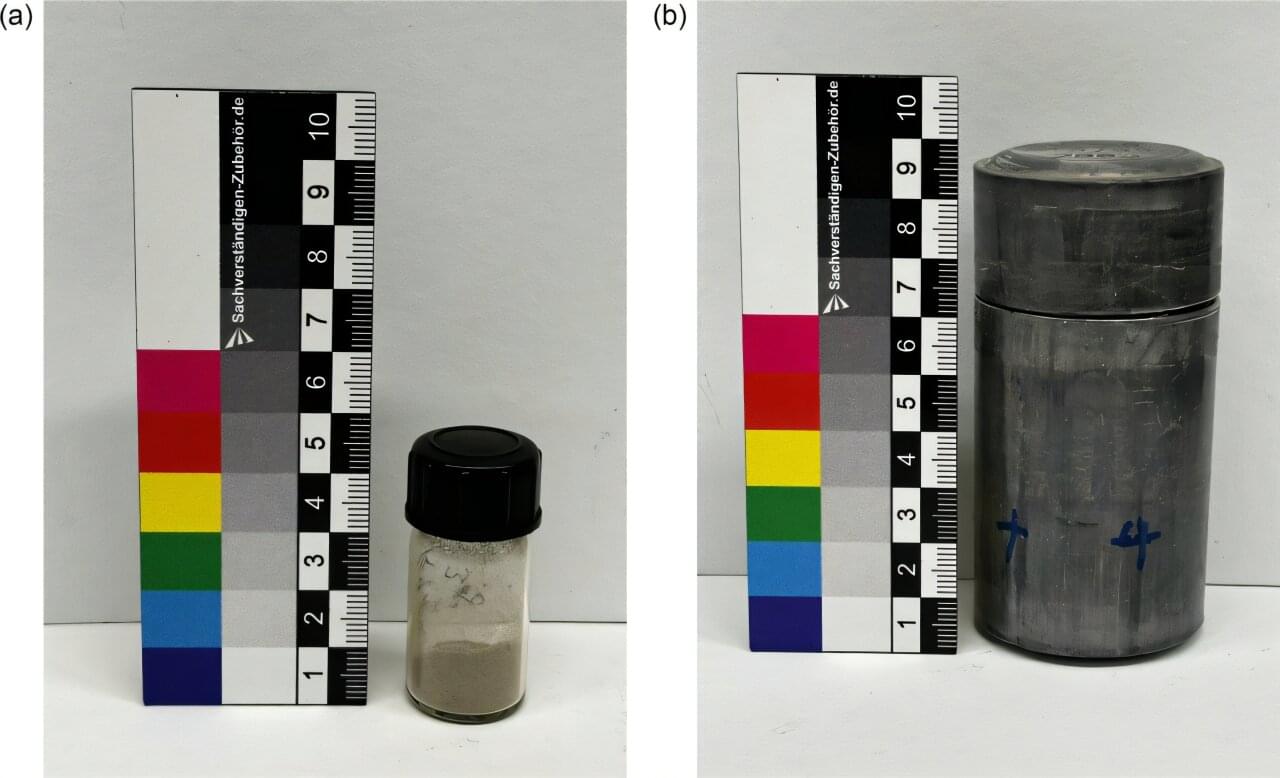
For the first time, a research team from the University of Cologne has observed the electron capture decay of technetium-98, an isotope of the chemical element technetium (Tc). Electron capture decay is a process in which an atomic nucleus “captures” an electron from its inner shell. The electron merges with a proton in the nucleus to form a neutron, turning the element into a different one. The working group from the Nuclear Chemistry department has thus confirmed a decades-old theoretical assumption.
The findings contribute to a more comprehensive understanding of technetium decay processes and extend the chart of nuclides—the “nuclear periodic table.” The study was published under the title “Electron-capture decay of 98 Tc” in the journal Physical Review C.
As early as the 1990s, researchers suspected that technetium-98 could also decay by capturing an electron, but no proof could be found, as the isotope only is available in extremely small quantities. For the current study, the Cologne research team used around three grams of technetium-99, which contains tiny traces of the rare isotope technetium-98 (around 0.06 micrograms).