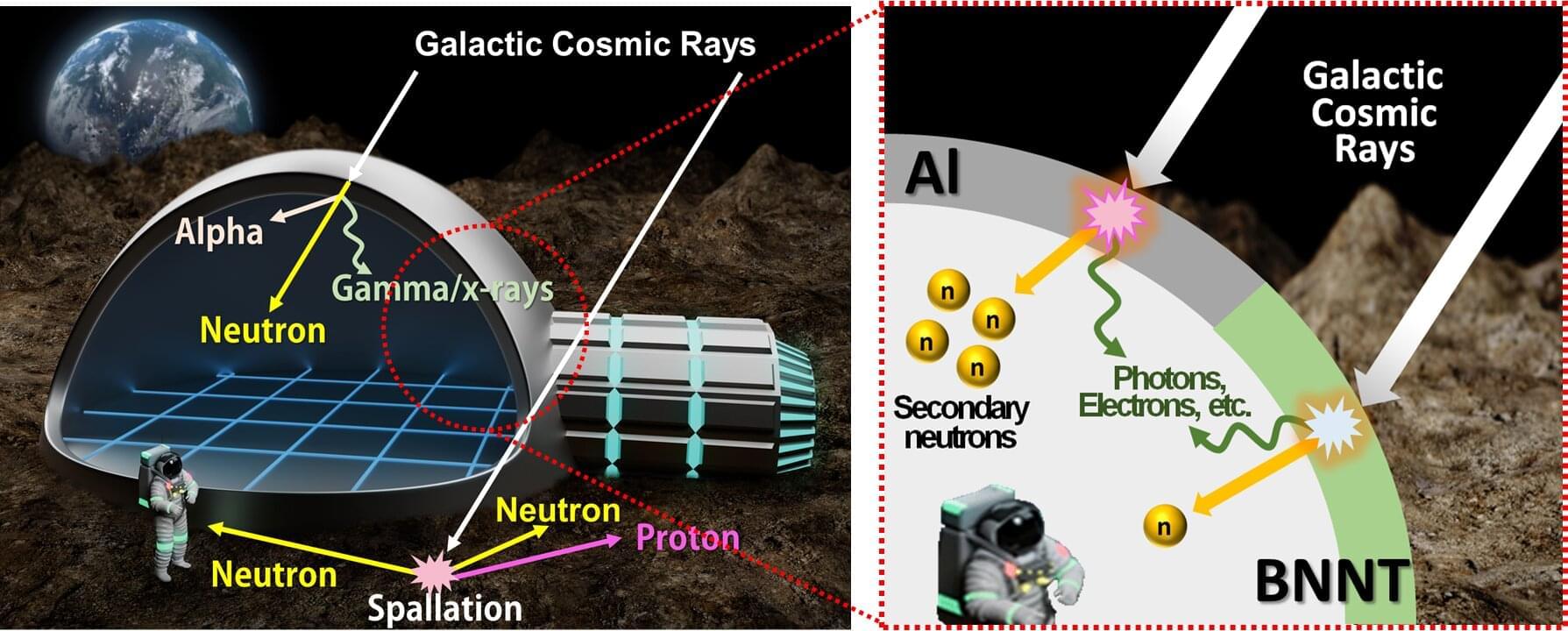
High-energy cosmic radiation damages cells and DNA, causing cancer, and secondary neutrons—generated especially from the planetary surfaces—can be up to 20 times more harmful than other radiations. Aluminum, the most widely used shielding material, has the drawback of generating additional secondary neutrons when below a certain thickness.
Consequently, boron nitride nanotubes (BNNTs), which are lightweight, strong, and possess excellent neutron shielding capabilities, are emerging as a promising alternative.
BNNTs are ultrafine tubular only about 5 nanometers in diameter—roughly 1/20,000 the thickness of a human hair—making them extremely light and strong, with excellent thermal neutron absorption capability. However, due to limitations in fabrication technology, they have so far only been produced into thin and brittle sheet, restricting their practical applications.