Page 11329
Feb 29, 2016
Sharing secrets with light
Posted by Karen Hurst in categories: finance, quantum physics
More great news on Quantum Networks; some banks in Europe are leveraging the technology to communicate among themselves.
Light is everywhere. Even the darkest of rooms in our homes contain a handful of blinking LEDs. But what is light? Few of us ever stop to think about this question. Around a hundred years ago scientists discovered that light comes in granules, much like the sand on a beach, which we now call photons.
These are truly bizarre objects that obey the rules of the quantum world. The rules allow some pairs of photons to share a property called entanglement. After being entangled, two photons behave as one object. Changing one photon will affect the other at exactly the same time, no matter how far apart they are.
Feb 29, 2016
Quarks To Quasars Photo
Posted by Shailesh Prasad in categories: particle physics, space travel
Feb 29, 2016
Kaspersky Labs rolls out targeted threat detection platform for enterprises
Posted by Karen Hurst in category: cybercrime/malcode
“Kaspersky admits that targeted attacks represent less than one percent of the entire threat landscape”;
Hmmm (wonder how much it cost to develop and deploy?) At least it’s a start.
Continue reading “Kaspersky Labs rolls out targeted threat detection platform for enterprises” »
This has been around for a really, really long time. I remember many years ago one could go online without too much hassel and locate software code that the hacking network shared to teach folks their trade. I actually tested some of it for a firm to help test their infrastructure security; and it worked really well. However, now days it’s about the trade of id’s, credit card information, etc.
Beyond the regular Web, there is the Dark Web. You’ve probably heard something about it but probably just enough to know you didn’t want to know too much more about it. Well, here are some answers to some common questions about the Dark Web.
Feb 29, 2016
Google opens applications for free DDoS blocker to prevent hackers taking out the Web
Posted by Karen Hurst in categories: cybercrime/malcode, internet
The DDoS prevention tool is part of Google Ideas, renamed Jigsaw, whose stated mission is to “build products to help people investigate corruption.”
Feb 29, 2016
Graphene Patterned After Moth Eyes Could Give Us ‘Smart Wallpaper’
Posted by Shailesh Prasad in category: materials
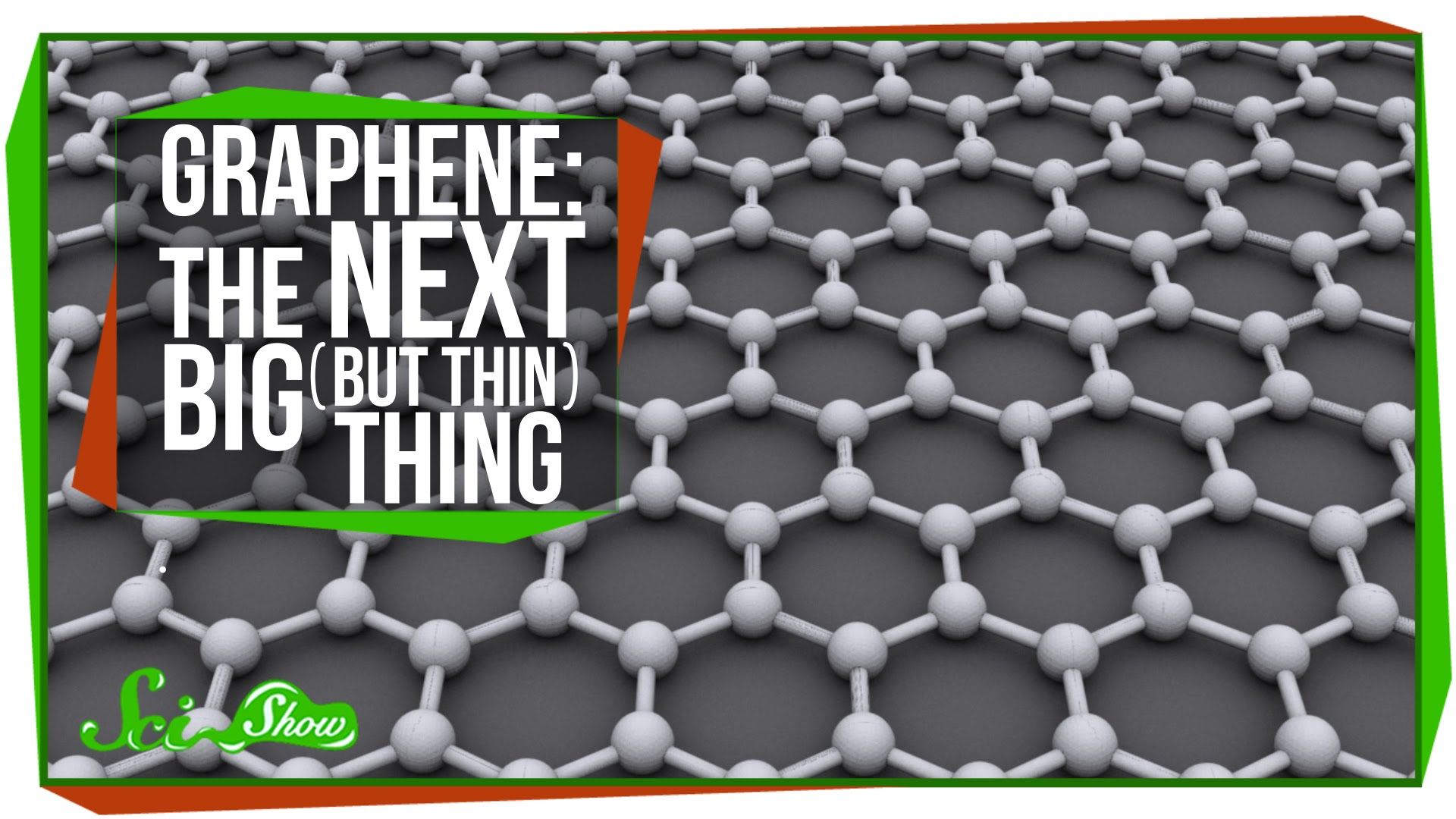
Tweaking the structure of graphene so that it matches patterns found in the eyes of moths could one day give us “smart wallpaper,” among a host of other useful technologies.
Using a novel technique called “nano texturing,” scientists at the University of Surrey in England have successfully modified ultra-thin graphene sheets to create the most efficient light-absorbent material to date, which is capable of generating electricity from both captured light and waste heat. They described their work in a new paper in Science Advances.
Continue reading “Graphene Patterned After Moth Eyes Could Give Us ‘Smart Wallpaper’” »
Feb 29, 2016
Want to avoid breaches Think like a hacker
Posted by Karen Hurst in category: cybercrime/malcode
One philosophy that I have often practice and encourage my team to do is to think like a hacker. It has served me and my teams well. At times; I have shared areas where risks exist in the emerging technologies; and hope that I don’t make folks too nervous. However, we all have to start thinking like hackers or pay the cost some day.
C-level executives from giant corporations and officials from the smallest companies all must think like hackers and test their cyber defenses regularly if they expect to avoid breaches of their systems.
That’s according to a panel of cybersecurity experts who recently spoke to a crowd gathered at the Donald Danforth Plant Science Center.
Continue reading “Want to avoid breaches Think like a hacker” »
Feb 29, 2016
Imaging algorithm gathers information about how cells move
Posted by Shailesh Prasad in categories: biotech/medical, information science
Brown University engineers have developed a new technique to help researchers understand how cells move through complex tissues in the body. They hope the tool will be useful in understanding all kinds of cell movements, from how cancer cells migrate to how immune cells make their way to infection sites.
The technique is described in a paper published in the Proceedings of the National Academy of Sciences.
The traditional method for studying cell movement is called traction force microscopy (TFM). Scientists take images of cells as they move along 2-D surfaces or through 3-D gels that are designed as stand-ins for actual body tissue. By measuring the extent to which cells displace the 2-D surface or the 3-D gel as they move, researchers can calculate the forces generated by the cell. The problem is that in order to do the calculations, the stiffness and other mechanical properties of artificial tissue environment must be known.