Digital security depends on the difficulty of factoring large numbers. A new proof shows why one method for breaking digital encryption won’t work.



“We’re sorry this happened,” Tomer Bar, engineering director at Facebook, wrote in a blog post about the flaw.
The flaw allowed apps that users accessed through the social network’s “Facebook Login” system to see photos that had been uploaded but not published on Facebook, as well as photos published to Facebook’s “Marketplace” and to its Stories feature.
“The bug also impacted photos that people uploaded to Facebook but chose not to post,” Bar wrote.
We’ve discovered water on the asteroid Bennu! Our OSIRIS-REx mission has revealed water locked inside the clays that make up Bennu.
Recently analyzed data from NASA’s Origins, Spectral Interpretation, Resource Identification, Security-Regolith Explorer (OSIRIS-REx) mission has revealed water locked inside the clays that make up its scientific target, the asteroid Bennu.
During the mission’s approach phase, between mid-August and early December, the spacecraft traveled 1.4 million miles (2.2 million km) on its journey from Earth to arrive at a location 12 miles (19 km) from Bennu on Dec. 3. During this time, the science team on Earth aimed three of the spacecraft’s instruments towards Bennu and began making the mission’s first scientific observations of the asteroid. OSIRIS-REx is NASA’s first asteroid sample return mission.
Data obtained from the spacecraft’s two spectrometers, the OSIRIS-REx Visible and Infrared Spectrometer (OVIRS) and the OSIRIS-REx Thermal Emission Spectrometer (OTES), reveal the presence of molecules that contain oxygen and hydrogen atoms bonded together, known as “hydroxyls.” The team suspects that these hydroxyl groups exist globally across the asteroid in water-bearing clay minerals, meaning that at some point, Bennu’s rocky material interacted with water. While Bennu itself is too small to have ever hosted liquid water, the finding does indicate that liquid water was present at some time on Bennu’s parent body, a much larger asteroid.
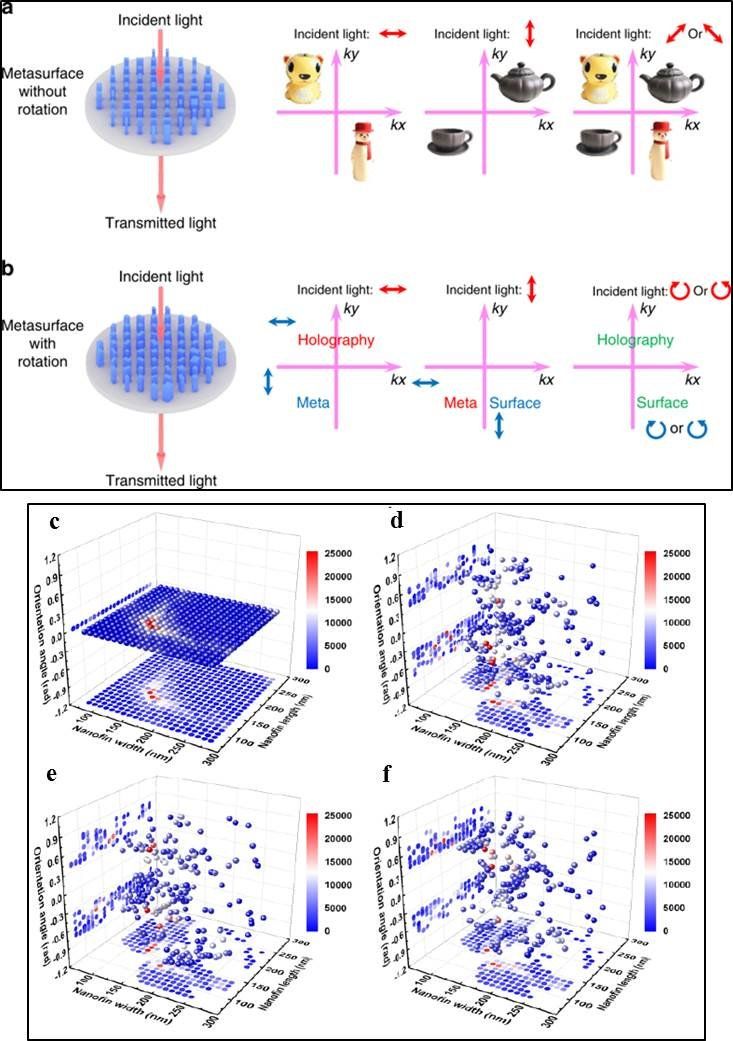
Holography is a powerful tool that can reconstruct wavefronts of light and combine the fundamental wave properties of amplitude, phase, polarization, wave vector and frequency. Smart multiplexing techniques (multiple signal integration) together with metasurface designs are currently in high demand to explore the capacity to engineer information storage systems and enhance optical encryption security using such metasurface holograms.
Holography based on metasurfaces is a promising candidate for applications in optical displays/storage with enormous information bearing capacity alongside a large field of view compared to traditional methods. To practically realize metasurface holograms, holographic profiles should be encoded on ultrathin nanostructures that possess strong light-matter interactions (plasmonic interactions) in an ultrashort distance. Metasurfaces can control light and acoustic waves in a manner not seen in nature to provide a flexible and compact platform and realize a variety of vectorial holograms, with high dimensional information that surpass the limits of liquid crystals or optical photoresists.
Among the existing techniques employed to achieve highly desired optical properties, polarization multiplexing (multiple signal integration) is an attractive method. The strong cross-talk associated with such platforms can, however, be prevented with birefringent metasurfaces (two-dimensional surfaces with two different refractive indices) composed of a single meta-atom per unit-cell for optimized polarization multiplexing.

Tesla launched a new ‘Enhanced Anti-theft’ system as an aftermarket product last month and we now take a first look at one of the very first installations on a Model X.
There have been strings of Tesla thefts earlier this year that prompt the automaker to offer several new security features.
We reported on several Tesla vehicle thefts through relay attacks in Europe earlier this year.
The longer-term answer is to develop and scale up the quantum communication network and, subsequently, the quantum internet. This will take major investments from governments. However, countries will benefit from the greater security offered13. For example, Canada keeps its census data secret for 92 years, a term that only quantum cryptography can assure. Government agencies could use quantum-secured blockchain platforms to protect citizens’ personal financial and health data. Countries leading major research efforts in quantum technologies, such as China, the United States and members of the European Union, will be among the early adopters. They should invest immediately in research. Blockchains should be a case study for Europe’s Quantum Key Distribution Testbed programme, for example.
Bitcoin and other cryptocurrencies will founder unless they integrate quantum technologies, warn Aleksey K. Fedorov, Evgeniy O. Kiktenko and Alexander I. Lvovsky. Bitcoin and other cryptocurrencies will founder unless they integrate quantum technologies, warn Aleksey K. Fedorov, Evgeniy O. Kiktenko and Alexander I. Lvovsky.

As an international relations scholar who studies space law and policy, I have come to realize what most people do not fully appreciate: Dealing with space debris is as much a national security issue as it is a technical one.
Considering the debris circling the Earth as just an obstacle in the path of human missions is naive. As outer space activities are deeply rooted in the geopolitics down on Earth, the hidden challenge posed by the debris is the militarization of space technologies meant to clean it up.
To be clear, space debris poses considerable risks; however, to understand those risks, I should explain what it is and how it is formed. The term “space debris” refers to defunct human-made objects, relics left over from activities dating back to the early days of the space age. Over time that definition has expanded to include big and small things like discarded boosters, retired satellites, leftover bits and pieces from spacecraft, screwdrivers, tools, nuts and bolts, shards, lost gloves, and even flecks of paint.

Location data beamed from GPS satellites are used by smartphones, car navigation systems, the microchip in your dog’s neck and guided missiles — and all those satellites are controlled by the U.S. Air Force. That makes the Chinese government uncomfortable, so it’s developing an alternative that a U.S. security analyst calls one of the largest space programs the country has undertaken.
The Beidou Navigation System will be accessible worldwide by 2020.

Following recent trends in state-of-the-art developments, from cryptocurrencies and universal basic income to biohacking and the surveillance state, transhumanism has been moved into the limelight of political discourse to reshape humanity’s future.
Andrew Vladimirov, Information security specialist, biohacker and one of the original members of the Transhumanist Party UK, spoke in-depth with Sputnik about the rise of transhumanism and its implications.
Scientists are planning to create a network in the Chicago area tapping the principles of quantum physics. The idea is to prove that quantum physics could provide the basis for an unhackable internet.
This, they say, could have wide-ranging impact on communications, computing and national security.
The quantum network development, supported by the US Department of Energy (DOE), will stretch between the DOE’s Argonne National Laboratory and Fermi National Acceleratory Laboratory, a connection that is said will be the longest in the world to send secure information using quantum physics.