Scientists beamed particles from a satellite to two locations on Earth 750 miles apart — and the particles were still mysteriously connected.


Chinese researchers report that they’ve set a new distance record for quantum teleportation through space, the phenomenon that Albert Einstein once scoffed at as “spooky action at a distance.”
The technology isn’t yet ready for prime time, but eventually it could open the way for a new type of unbreakable encryption scheme based on the weirdness of quantum physics.

“For example, Hasan says, “we can test theoretical ideas in the early universe,” simulating how particles may have behaved just after the Big Bang, when Lorentz symmetry may not have been obeyed.”
It’s interesting how often I hear condensed matter physicists justify their work by saying “might be important for something with quantum gravity” while condensed matter physics by itself is much more likely than quantum gravity to be good for something.
We have a highly respected Theoretical Physicist and a pioneer of Quantum Computing, along with the Founder of one of the leading quantum computer companies, D-Wave (whose clients include Google and NASA), talking about parallel universes. Here is a key that I discovered. They are not talking about parallel universes as a theory but as something factual that exists.
An amazing article on the ability of a Quantum Computer to exploit parallel universes. This article is a MUST READ!
A cluster of 64 superfluid helium atoms mimic properties similar to a Black hole. Could this lead to the formation of a unified Quantum Gravity theory?
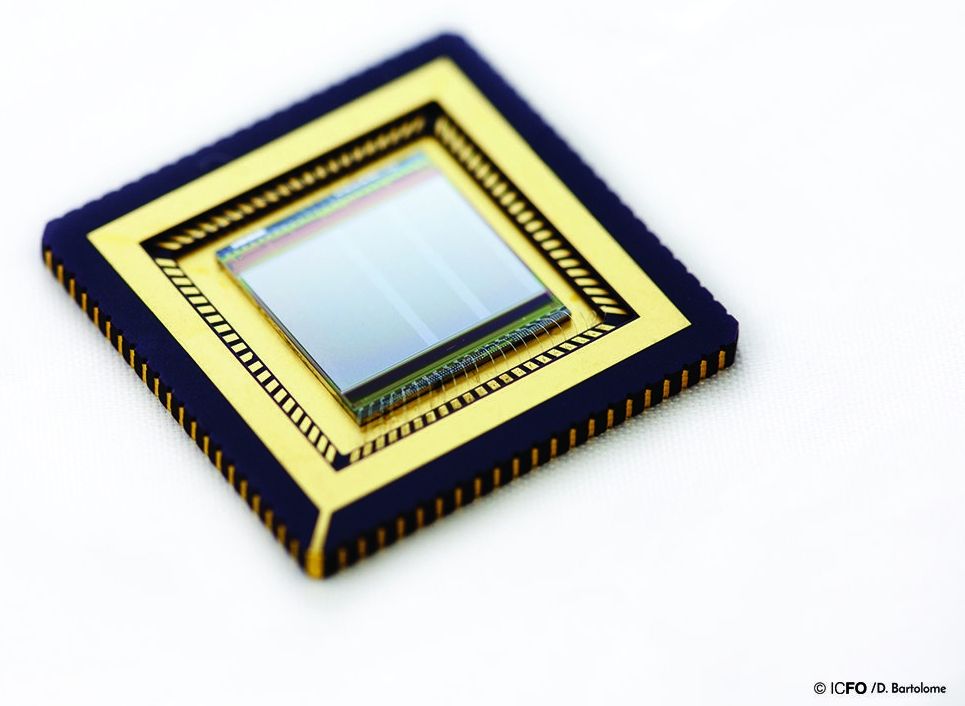
Over the past 40 years, microelectronics have advanced by leaps and bounds thanks to silicon and complementary metal-oxide semiconductor (CMOS) technology, enabling computing, smartphones, compact and low-cost digital cameras, as well as most of the electronic gadgets we rely on today.
However, the diversification of this platform into applications other than microcircuits and visible light cameras has been impeded by the difficulty of combining non-silicon semiconductors with CMOS.
IFCO researchers have now overcome this obstacle, showing for the first time the monolithic integration of a CMOS integrated circuit with graphene, resulting in a high-resolution image sensor consisting of hundreds of thousands of photodetectors based on graphene and quantum dots (QD). They incorporated it into a digital camera that is highly sensitive to UV, visible and infrared light simultaneously. This has never before been achieved with existing imaging sensors. In general, this demonstration of monolithic integration of graphene with CMOS enables a wide range of optoelectronic applications, such as low-power optical data communications and compact and ultra sensitive sensing systems.

The new work addresses not only what dark energy is but why the rate of universal expansion has the value it does.
“Everybody wants to know what dark energy is,” Wang told Live Science. “I reconsidered this question more carefully,” from the perspective of the universe’s energy density.
Wang and his colleagues assumed that modern quantum field theory was correct about the energy density being very large, but that the vacuum fluctuations, or the movements of empty space, were very large on tiny scales, near what is called the Planck length, or 1.62 × 10 ^ minus 35 meters. That’s so small that a proton is 100 million trillion times bigger.

Of the many ‘white whales’ that theoretical physicists are pursuing, the elusive magnetic monopole — a magnetic with only one pole — is one of the most confounding.
Compared to the Higgs boson in terms of its potential impact on modern physics, the magnetic monopole has been on scientists’ minds for even longer. And now our best shot at finding it just got weird — two phenomena that resemble the magnetic monopole have become one.
If you’re unfamiliar with the magnetic monopole, it’s a hypothetical particle that’s long been predicted by quantum physics, but no one has ever been able to prove that it exists.

Quantum computing and the blockchain both get plenty of attention in 2017, and now researchers in Russia have combined the two to create what they claim is an unhackable distributed-ledger platform.
The new technology, described as the “first quantum-safe blockchain,” promises to make it secure for organizations to transfer data without the fear of hacking from even the most powerful computers, in this case, the emerging field of quantum computing. Quantum computers make use of the quantum states of subatomic particles to store information, with the potential to do some calculations far faster than current computers. There’s some dispute whether we have actually reached that point yet, but companies such as Google Inc. are promising that true quantum computing is just around the corner.
“Quantum computers pose a major threat to data security today and could even be used to hack blockchains, destroying everything from cryptocurrencies like bitcoin to secure government communications,” a spokesperson for the Russian Quantum Center told SiliconANGLE. “Because quantum computers can test a large number of combinations at once, they will be able to destroy these digital signatures, leaving the blockchain vulnerable.”