Auto-Color Linux malware targets governments and universities, using stealth tactics and encryption to evade detection and maintain persistence.

Chinese researchers have allegedly made a major breakthrough in Quantum Secure Direct Communication (QSDC). According to reports, the team has developed a new communication protocol that allows secure data transmission using quantum mechanics principles, setting a world record for transmission speed and distance.
In case you are unaware, QSDC is a type of quantum communication that directly transmits information in quantum states (such as photons) without needing encryption keys like traditional methods (e.g., quantum key distribution or QKD).
Scientists in Switzerland have developed a new method to improve internet security against quantum computing attacks, using quantum-resistant encryption and a new type of hardware.
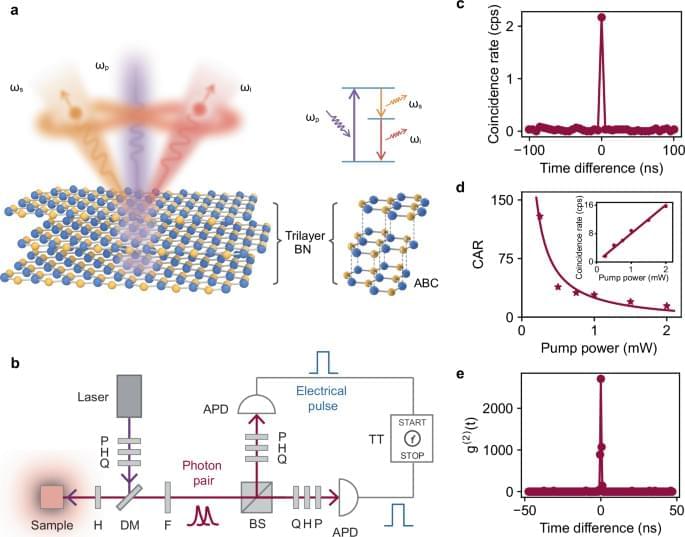


As quantum computers threaten traditional encryption, researchers are developing quantum networks to enable ultra-secure communication.
Scientists at Leibniz University Hannover have pioneered a new method using light frequencies to enhance quantum key distribution. This breakthrough reduces complexity, cuts costs, and paves the way for scalable, tap-proof quantum internet infrastructure.

Data security on the internet is under threat: in the future, quantum computers could decode even encrypted files sent over the internet in no time. Researchers worldwide are, therefore, experimenting with quantum networks that will enable a paradigm shift in the future when globally connected to form the quantum internet.
Such systems would be able to guarantee tap-proof communication through quantum mechanical phenomena such as superposition and entanglement, as well as cryptographic quantum protocols. However, the quantum internet is still in its infancy: high costs coupled with high energy consumption and a high level of complexity for the necessary technologies have prevented quantum networks from scaling easily.
Two researchers at the Institute of Photonics at the Leibniz University Hannover want to remedy this situation. Using frequency-bin coding, they have developed a novel method for entanglement-based quantum key distribution. This quantum mechanical encryption technique uses different light frequencies, i.e. colors, to encode the respective quantum states. The method increases security and resource efficiency.

Particle detectors play a crucial role in our understanding of the fundamental building blocks of the universe. They allow scientists to study the behavior and properties of the particles produced in high-energy collisions. Such particles are boosted to near the speed of light in large accelerators and then smashed into targets or other particles where they are then analyzed with detectors. Traditional detectors, however, lack the needed sensitivity and precision for certain types of research.
Researchers at the U.S. Department of Energy’s (DOE) Argonne National Laboratory have made a significant breakthrough in the field of high-energy particle detection in recent experiments conducted at the Test Beam Facility at DOE’s Fermi National Accelerator Laboratory (Fermilab).
They have found a new use for the superconducting nanowire photon detectors (SNSPDs) already employed for detecting photons, the fundamental particles of light. These incredibly sensitive and precise detectors work by absorbing individual photons. The absorption generates small electrical changes in the superconducting nanowires at very low temperatures, allowing for the detection and measurement of photons. Specialized devices able to detect individual photons are crucial for quantum cryptography (the science of keeping information secret and secure), advanced optical sensing (precision measurement using light) and quantum computing.