DARPA is using Earth’s atmosphere as a powerful sensor, allowing the detection of events like rocket reentries and illicit detonations.


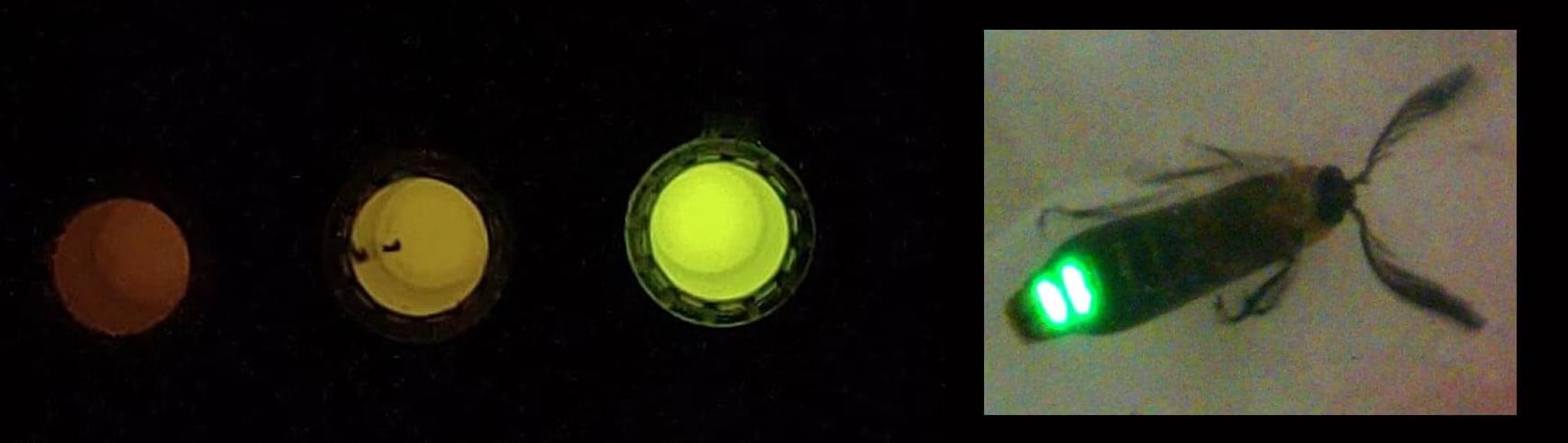
The gene encoding an enzyme from a firefly, discovered at the Sorocaba campus of the Federal University of São Carlos (UFSCar) in Brazil, has given rise to a biosensor capable of detecting pH changes in mammalian cells—which could be useful, for example, in studying diseases and assessing the toxicity of a drug candidate.
The luciferase from the species Amydetes vivianii changes color from bluish-green to yellow and red as acidity decreases in fibroblasts, the most common cell type in connective tissue. It does so with great intensity and stability, something that had not been achieved with other luciferases tested by the research group.
The work is published in the journal Biosensors.
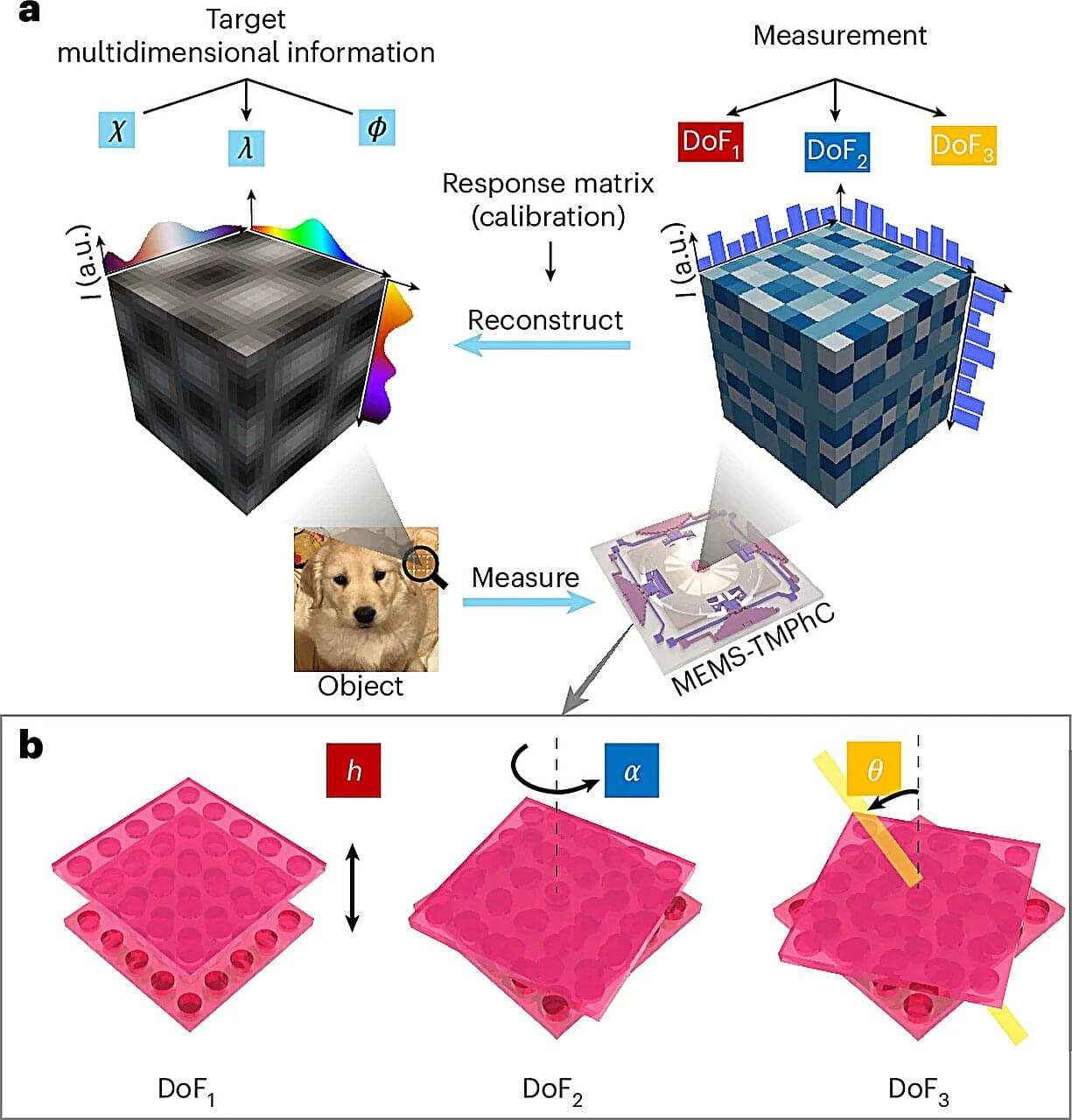
Twisted moiré photonic crystals—an advanced type of optical metamaterial—have shown enormous potential in the race to engineer smaller, more capable and more powerful optical systems. How do they work?
Imagine you have two pieces of fabric with regular patterns, like stripes or checkers. When you lay the two pieces of fabric directly on top of each other, you can see each pattern clearly. But if you slightly shift one piece of fabric or twist it, new patterns that weren’t in either of the original fabrics emerge.
In twisted moiré photonic crystals, how the layers twist and overlap can change how the material interacts with light. By changing the twist angle and the spacing between layers, these materials can be fine-tuned to control and manipulate different aspects of light simultaneously—meaning the multiple optical components typically needed to simultaneously measure light’s phase, polarization, and wavelength could be replaced with one device.

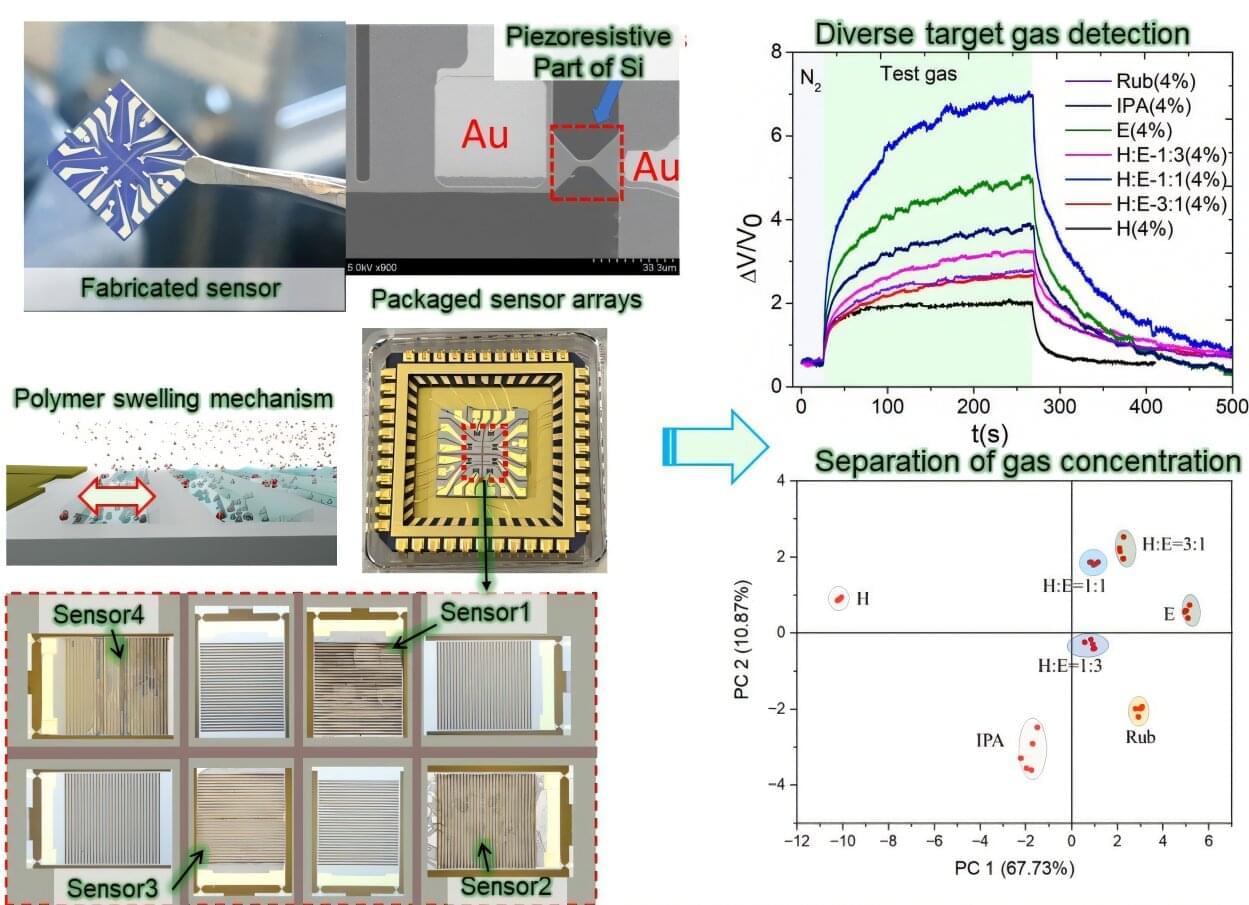
Imagine walking into your kitchen and instantly knowing if the fish you bought yesterday is still fresh—or entering an industrial site with sensors that immediately alert you to hazardous gas leaks. This isn’t science fiction—it’s the promise behind our newly developed nanomechanical sensor array, a powerful tool we’ve created to detect and analyze complex gases in real-time.
In our recent study published in Microsystems & Nanoengineering, we introduce a miniaturized array of silicon and polymer-based sensors capable of detecting various gases quickly and accurately.
This array utilizes a simple yet ingenious principle: when gas molecules enter the sensor, they diffuse into specific polymers, causing them to swell slightly. This swelling generates mechanical stress detected by tiny piezoresistive sensors embedded in silicon. It’s like watching a sponge expand as it absorbs water—but at a microscopic scale, with the expansion measured electrically to detect and identify gases.
The body’s cells respond to stress—toxins, mutations, starvation or other assaults—by pausing normal functions to focus on conserving energy, repairing damaged components and boosting defenses.
If the stress is manageable, cells resume normal activity; if not, they self-destruct.
Scientists have believed for decades this response happens as a linear chain of events: sensors in the cell “sound an alarm” and modify a key protein, which then changes a second protein that slows or shuts down the cell’s normal function.

Prototyping large structures with integrated electronics, like a chair that can monitor someone’s sitting posture, is typically a laborious and wasteful process.
One might need to fabricate multiple versions of the chair structure via 3D printing and laser cutting, generating a great deal of waste, before assembling the frame, grafting sensors and other fragile electronics onto it, and then wiring it up to create a working device.
If the prototype fails, the maker will likely have no choice but to discard it and go back to the drawing board.

