INTERPOL arrests 8 cybercriminals in West Africa linked to phishing scams and romance fraud, defrauding victims globally.




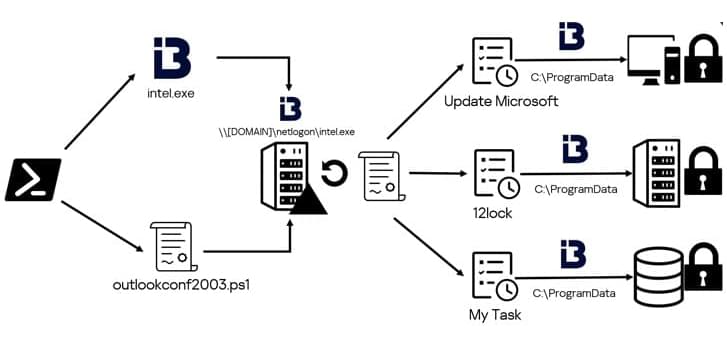
“When a new user logs into the server, it immediately stops all ‘noisy’ activities, lying dormant until the server is idle again. After execution, it deletes its binary and continues to run quietly in the background as a service.”
It’s worth noting that some aspects of the campaign were disclosed last month by Cado Security, which detailed an activity cluster that targets internet-exposed Selenium Grid instances with both cryptocurrency mining and proxyjacking software.
Specifically, the fileless perfctl malware has been found to exploit a security flaw in Polkit (CVE-2021–4043, aka PwnKit) to escalate privileges to root and drop a miner called perfcc.