In today’s AI news, Meta, the parent company of Facebook, and other leading social media platforms, is looking to raise as much as $35 Billion to build data centers in the US. Apollo Global Management Inc., an alternative asset manager has discussed providing a major part of the financing, said the people, who asked not to be identified. KKR & Co. is also a part of the investor group.
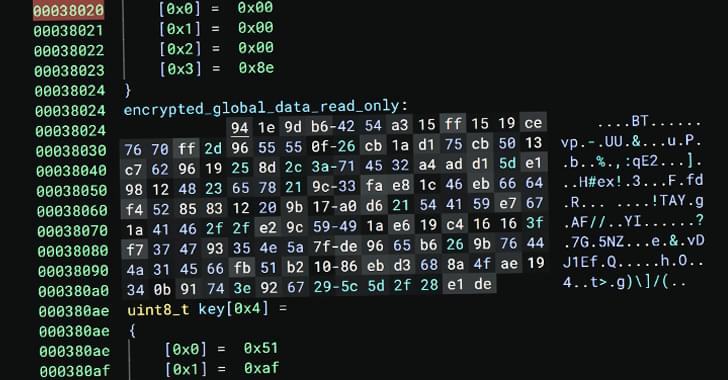
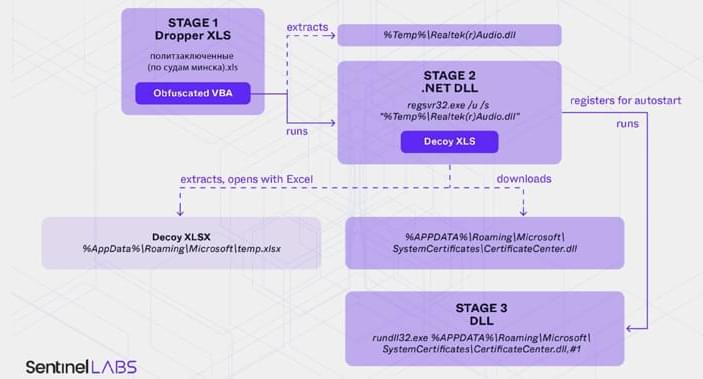
In other advancements, With so much software now getting written by AI, having a window into its security can be a challenge. That’s the premise of Archipelo, a San Francisco-based cybersecurity startup that is today emerging from stealth with $12 Million in funding. Archipelo’s pitch is that it has a platform for “Developer Security Posture Management” (DevSPM).
S integration with Suno, you can turn simple, creative requests into songs. ‘ + And, In its annual letter, payments giant Stripe declared that it was “seeing an AI boom” with its data, revealing that artificial intelligence startups are growing more rapidly than traditional SaaS companies have historically. In a chart, Stripe showed that the top 100 AI companies were able to achieve $5 million in annualized revenue in 24 months in 2024 compared to the top 100 SaaS companies taking 37 months.
In videos, ever wondered how to enhance your AI performance? IBM’s Susan Eickhoff shows how to boost AI performance using an ensemble of models, combining traditional AI and large language models. Learn structured data analysis and dynamic prediction methods.
And, since its launch in 2020, Project Aria has propelled research across the world to advance the state of the art in machine perception and AI, through access to cutting-edge research hardware and open-source datasets, models, and tooling. Today, Meta is excited to announce the next step in this journey: the introduction of Aria Gen 2 glasses.
Then, join Dr. Ben Armstrong Executive Director, MIT Industrial Performance Center at the 2025 MIT Bangkok Symposium for an insightful session entitled Positive-Sum Automation & Artificial Intelligence. MIT’s working group on Generative AI and the Work of the Future is studying how dozens of large companies are adopting generative AI to improve productivity…
S largest model to date. Chen speaks about what the new model says about the AI scaling wall, how scaling traditional GPT models compares to reasoning models. + Thats all for today, but AI is moving fast — like, comment, follow, and subscribe for more AI news!