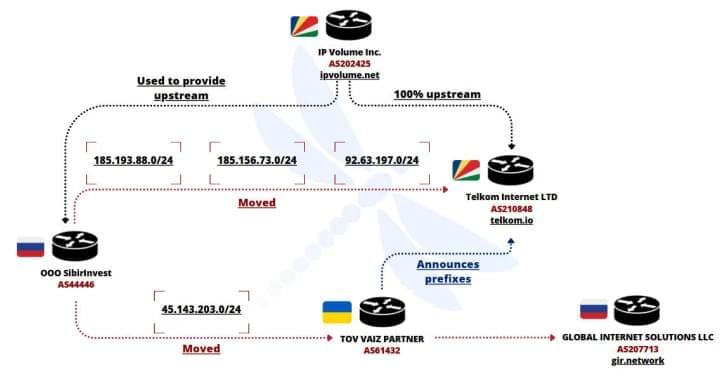
FDN3 brute-force attacks peaked July 6–8, 2025, tied to Seychelles bulletproof hosts enabling ransomware entry.



Researchers have disrupted an operation attributed to the Russian state-sponsored threat group Midnight Blizzard, which sought access to Microsoft 365 accounts and data.
Also known as APT29, the hacker group compromised websites in a watering hole campaign to redirect selected targets “to malicious infrastructure designed to trick users into authorizing attacker-controlled devices through Microsoft’s device code authentication flow.”
The Midnight Blizzard threat actor has been linked to Russia’s Foreign Intelligence Service (SVR) and is well-known for its clever phishing methods that recently impacted European embassies, Hewlett Packard Enterprise, and TeamViewer.


Cybersecurity researchers have discovered a malicious npm package that comes with stealthy features to inject malicious code into desktop apps for cryptocurrency wallets like Atomic and Exodus on Windows systems.
The package, named nodejs-smtp, impersonates the legitimate email library nodemailer with an identical tagline, page styling, and README descriptions, attracting a total of 347 downloads since it was uploaded to the npm registry in April 2025 by a user named “nikotimon.” It’s currently no longer available.
“On import, the package uses Electron tooling to unpack Atomic Wallet’s app.asar, replace a vendor bundle with a malicious payload, repackage the application, and remove traces by deleting its working directory,” Socket researcher Kirill Boychenko said.




The financially motivated threat actor known as Storm-0501 has been observed refining its tactics to conduct data exfiltration and extortion attacks targeting cloud environments.
“Unlike traditional on-premises ransomware, where the threat actor typically deploys malware to encrypt critical files across endpoints within the compromised network and then negotiates for a decryption key, cloud-based ransomware introduces a fundamental shift,” the Microsoft Threat Intelligence team said in a report shared with The Hacker News.
“Leveraging cloud-native capabilities, Storm-0501 rapidly exfiltrates large volumes of data, destroys data and backups within the victim environment, and demands ransom — all without relying on traditional malware deployment.”