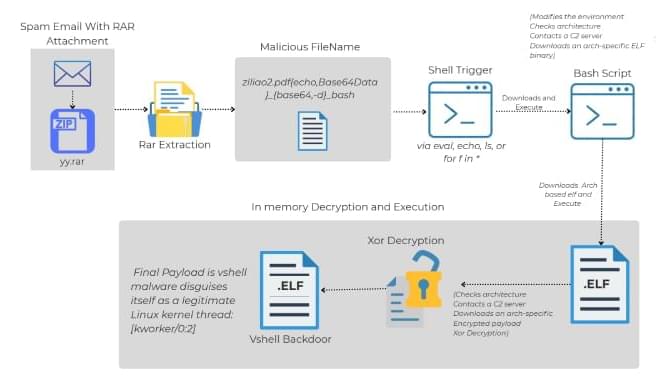
Cybersecurity researchers have shed light on a novel attack chain that employs phishing emails to deliver an open-source backdoor called VShell.
The “Linux-specific malware infection chain that starts with a spam email with a malicious RAR archive file,” Trellix researcher Sagar Bade said in a technical write-up.
“The payload isn’t hidden inside the file content or a macro, it’s encoded directly in the filename itself. Through clever use of shell command injection and Base64-encoded Bash payloads, the attacker turns a simple file listing operation into an automatic malware execution trigger.”