Attackers exploit Milesight router flaw to send smishing SMS in Europe, targeting banks and telecoms.

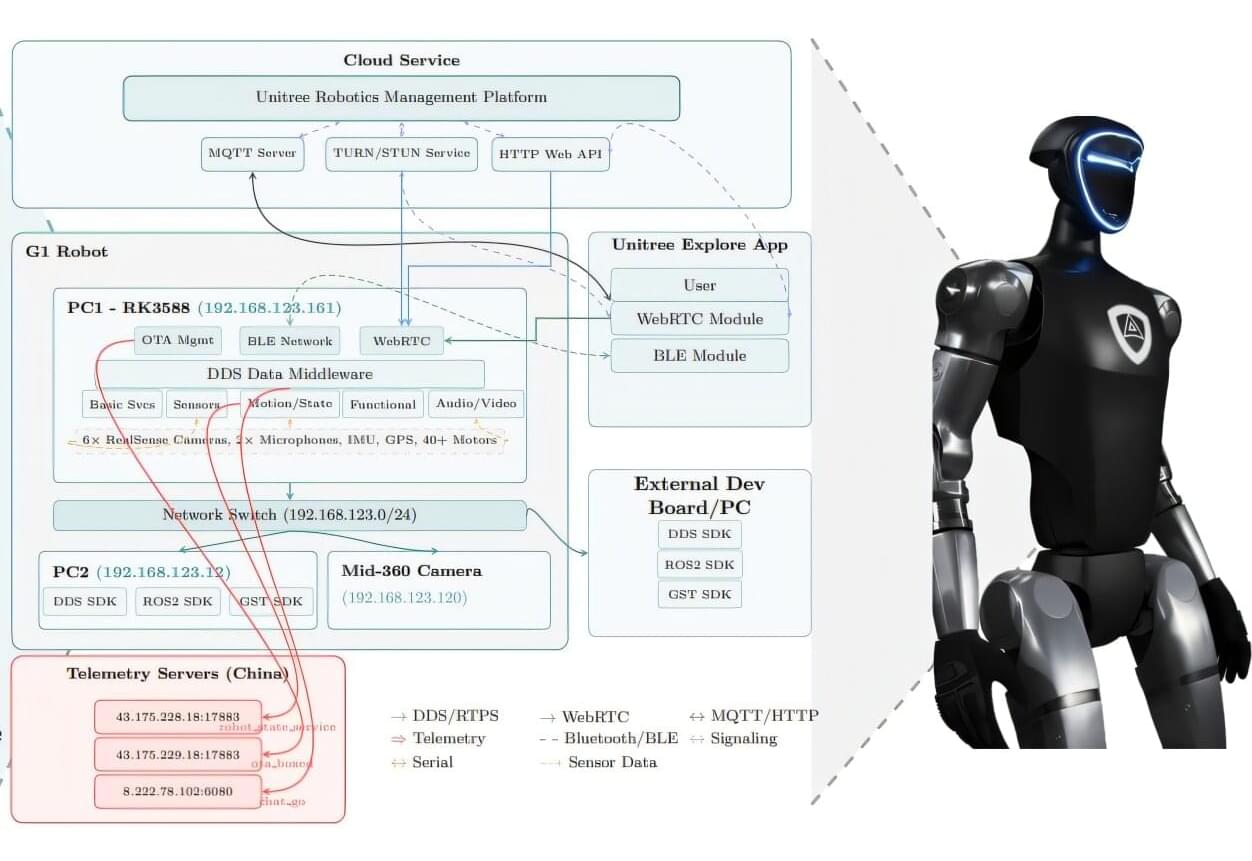
Researchers have uncovered serious security flaws with the Unitree G1 humanoid robot, a machine that is already being used in laboratories and some police departments. They discovered that G1 can be used for covert surveillance and could potentially launch a full-scale cyberattack on networks.
It sounds like the stuff of science fiction nightmares, robots that are secretly spying on you and could be controlled by remote hackers. However, the concern is real, as these types of robots are becoming increasingly common in homes, businesses, critical infrastructure and public spaces.

“The group takes an interest in diplomatic communications, defense-related intelligence and the operations of critical governmental ministries,” the company said. “The timing and scope of the group’s operations frequently coincide with major global events and regional security affairs.”
This aspect is particularly revealing, not least because other Chinese hacking groups have also embraced a similar approach. For instance, a new adversary tracked by Recorded Future as RedNovember is assessed to have targeted entities in Taiwan and Panama in close proximity to “geopolitical and military events of key strategic interest to China.”
Phantom Taurus’ modus operandi also stands out due to the use of custom-developed tools and techniques rarely observed in the threat landscape. This includes a never-before-seen bespoke malware suite dubbed NET-STAR. Developed in. NET, the program is designed to target Internet Information Services (IIS) web servers.


Hackers are actively exploiting a critical vulnerability (CVE-2025–32463) in the sudo package that enables the execution of commands with root-level privileges on Linux operating systems.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added this vulnerability to its Known Exploited Vulnerabilities (KEV) catalog, describing it as “an inclusion of functionality from untrusted control sphere.”
CISA has given federal agencies until October 20 to apply the official mitigations or discontinue the use of sudo.

A new phishing and malware distribution toolkit called MatrixPDF allows attackers to convert ordinary PDF files into interactive lures that bypass email security and redirect victims to credential theft or malware downloads.
The new tool was spotted by Varonis researchers, who told BleepingComputer that MatrixPDF was first spotted on a cybercrime forum. The seller also uses Telegram as an additional means of interacting with buyers.
The developer of MatrixPDF promotes the tool as a phishing simulation and blackteaming tool. However, Varonis researcher Daniel Kelley told BleepingComputer that it was first seen being offered on cybercrime forums.

Explore how malicious images and pixel manipulation can hack AI agents, hijack systems, and bypass security. Learn risks, real-world cases, and protection strategies. AI hacking, malicious images, pixel manipulation attack, AI security, Trojan images, adversarial AI attacks, AI vulnerabilities, AI cybersecurity, image-based hacking, hijacking AI agents


The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added a critical security flaw impacting the Sudo command-line utility for Linux and Unix-like operating systems to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation in the wild.
The vulnerability in question is CVE-2025–32463 (CVSS score: 9.3), which affects Sudo versions prior to 1.9.17p1. It was disclosed by Stratascale researcher Rich Mirch back in July 2025.
“Sudo contains an inclusion of functionality from an untrusted control sphere vulnerability,” CISA said. “This vulnerability could allow a local attacker to leverage sudo’s-R (—chroot) option to run arbitrary commands as root, even if they are not listed in the sudoers file.”