Storm-2657 exploits phishing and weak MFA to hijack HR SaaS accounts and redirect payroll funds.


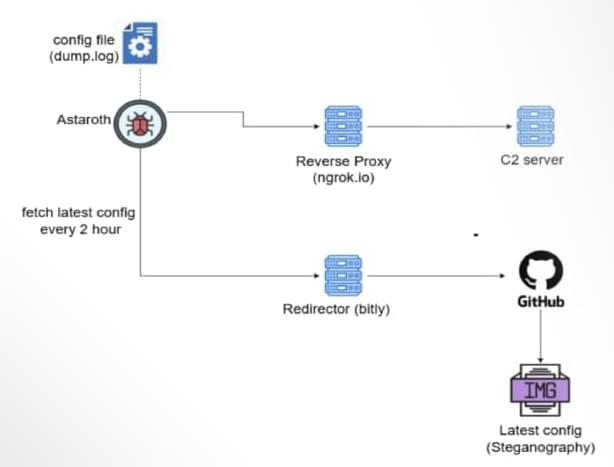
Cybersecurity researchers are calling attention to a new campaign that delivers the Astaroth banking trojan that employs GitHub as a backbone for its operations to stay resilient in the face of infrastructure takedowns.
“Instead of relying solely on traditional command-and-control (C2) servers that can be taken down, these attackers are leveraging GitHub repositories to host malware configurations,” McAfee Labs researchers Harshil Patel and Prabudh Chakravorty said in a report.
“When law enforcement or security researchers shut down their C2 infrastructure, Astaroth simply pulls fresh configurations from GitHub and keeps running.”



A large-scale botnet is targeting Remote Desktop Protocol (RDP) services in the United States from more than 100,000 IP addresses.
The campaign started on October 8 and based on the source of the IPs, researchers believe the attacks are launched by a multi-country botnet.
RDP is a network protocol that enables remote connection and control of Windows systems. It is typically used by administrators, helpdesk staff, and remote workers.

Widely available artificial intelligence systems can be used to deliberately insert hard-to-detect security vulnerabilities into the code that defines computer chips, according to new research from the NYU Tandon School of Engineering, a warning about the potential weaponization of AI in hardware design.
In a study published by IEEE Security & Privacy, an NYU Tandon research team showed that large language models like ChatGPT could help both novices and experts create “hardware Trojans,” malicious modifications hidden within chip designs that can leak sensitive information, disable systems or grant unauthorized access to attackers.
To test whether AI could facilitate malicious hardware modifications, the researchers organized a competition over two years called the AI Hardware Attack Challenge as part of CSAW, an annual student-run cybersecurity event held by the NYU Center for Cybersecurity.


A new Android spyware called ClayRat is luring potential victims by posing as popular apps and services like WhatsApp, Google Photos, TikTok, and YouTube.
The malware is targeting Russian users through Telegram channels and malicious websites that appear legitimate. It can steal SMS meessages call logs, notifications, take pictures, and even make phone calls.
Malware researchers at mobile security company Zimperium say that they documented more than 600 samples and 50 distinct droppers over the past three months, indicating an active effort from the attacker to amplify the operation.

A cybercrime gang tracked as Storm-2657 has been targeting university employees in the United States to hijack salary payments in “pirate payroll” attacks since March 2025.
Microsoft Threat Intelligence analysts who spotted this campaign found that the threat actors are targeting Workday accounts; however, other third-party human resources (HR) software-as-a-service (SaaS) platforms could also be at risk.
“We’ve observed 11 successfully compromised accounts at three universities that were used to send phishing emails to nearly 6,000 email accounts across 25 universities,” Microsoft said in a Thursday report.