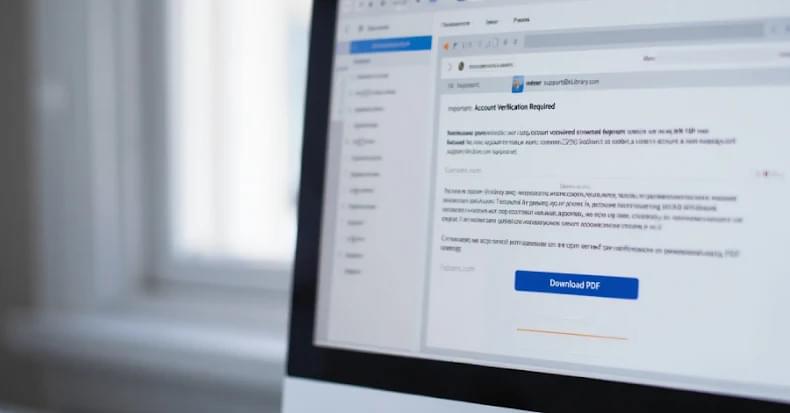
GhostPoster malware hid inside 17 Firefox add-ons, abusing logo files to hijack links, inject tracking code, and run ad fraud.



French authorities arrested a 22-year-old suspect on Tuesday for a cyberattack that targeted France’s Ministry of the Interior earlier this month.
In a statement issued by Public Prosecutor Laure Beccuau, officials said the suspected hacker was arrested on December 17, 2025, as part of an investigation into the attack.
“A person was arrested on December 17, 2025, as part of the investigation opened by the cybercrime unit of the Paris public prosecutor’s office, on charges including unauthorized access to an automated personal data processing system implemented by the State, committed by an organized group, following the cyberattack against the Ministry of the Interior,” reads the statement translated into English.

Amazon’s AWS GuardDuty security team is warning of an ongoing crypto-mining campaign that targets its Elastic Compute Cloud (EC2) and Elastic Container Service (ECS) using compromised credentials for Identity and Access Management (IAM).
The operation started on November 2nd and employed a persistence mechanism that extended mining operations and hindered incident responders.
The threat actor used a Docker Hub image that was created at the end of October and had more than 100,000 pulls.


Ransomware groups are targeting hypervisors to maximize impact, allowing a single breach to encrypt dozens of virtual machines at once. Drawing on real-world incident data, Huntress explains how attackers exploit visibility gaps at the hypervisor layer and outlines steps orgs can take to harden virtualization infrastructure.


A new Android malware-as-a-service (MaaS) named Cellik is being advertised on underground cybercrime forums offering a robust set of capabilities that include the option to embed it in any app available on the Google Play Store.
Specifically, attackers can select apps from Android’s official app store and create trojanized versions that appear trustworthy and keep the real app’s interface and functionality.
By providing the expected capabilities, Cellik infections can go unnoticed for a longer time. Additionally, the seller claims that bundling the malware this way may help bypass Play Protect, although this is unconfirmed.

