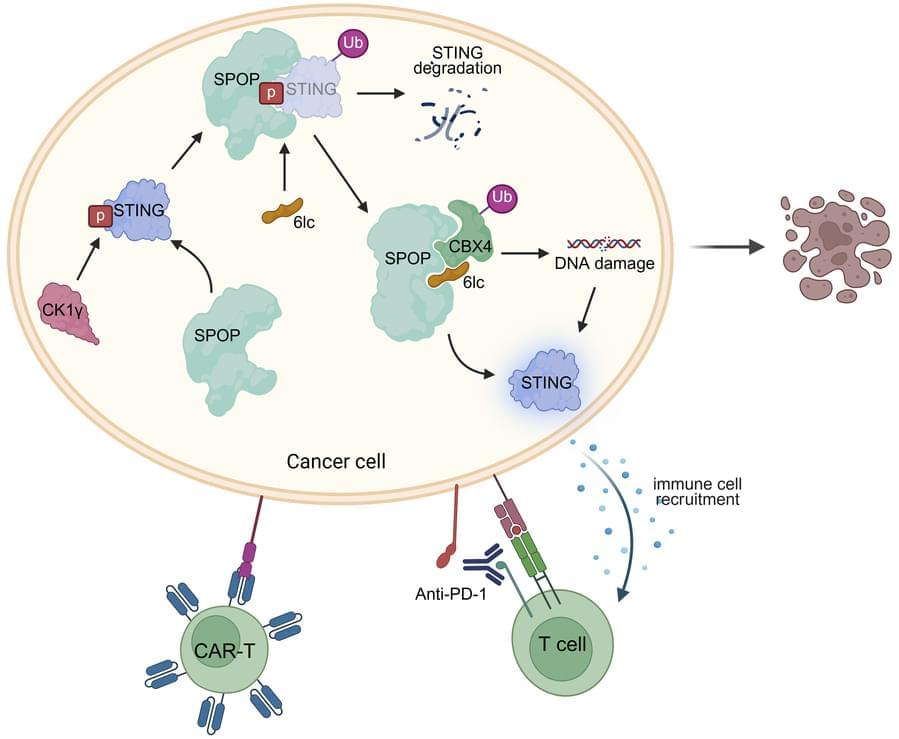
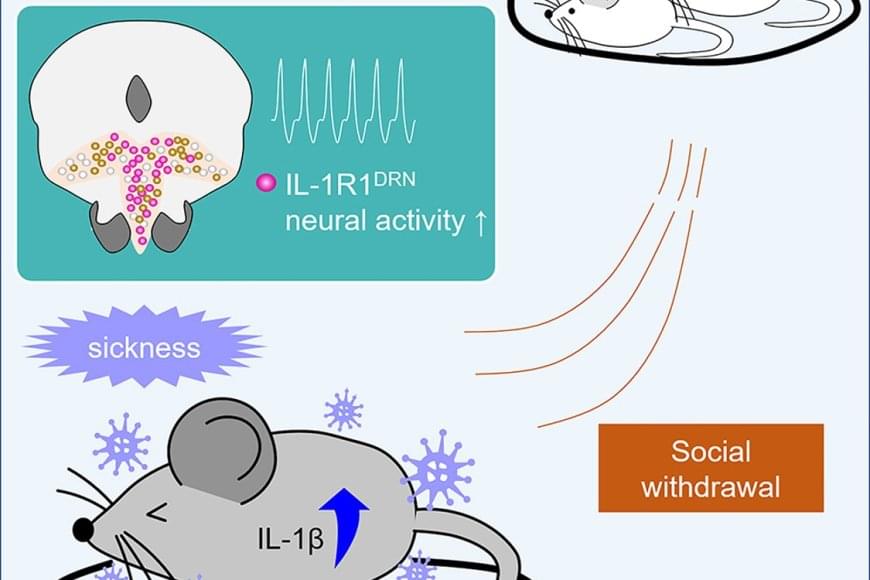
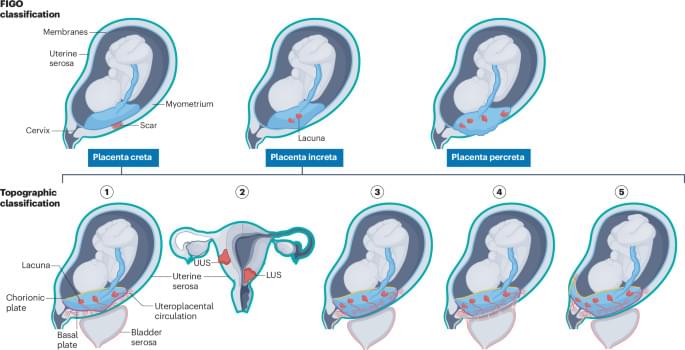
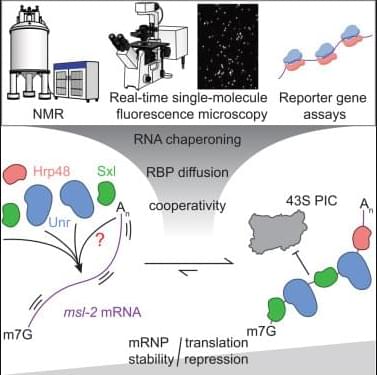
Free unofficial patches are available for a new Windows zero-day vulnerability that allows attackers to crash the Remote Access Connection Manager (RasMan) service.
RasMan is a critical Windows system service that starts automatically, runs in the background with SYSTEM-level privileges, and manages VPN, Point-to-Point Protocol over Ethernet (PPoE), and other remote network connections.
ACROS Security (which manages the 0patch micropatching platform) discovered a new denial-of-service (DoS) flaw while looking into CVE-2025–59230, a Windows RasMan privilege escalation vulnerability exploited in attacks that was patched in October.