Recent developments in the field of Artificial Intelligence have led to solutions to a variety of use cases. Different text-to-image generative models have paved the way for an exciting new field where written words can be transformed into vibrant, engrossing visual representations. The capacity to conceptualize distinctive ideas inside fresh circumstances has been further expanded by the explosion of personalization techniques as a logical evolution. A number of algorithms have been developed that simulate creative behaviors or aim to enhance and augment human creative processes.
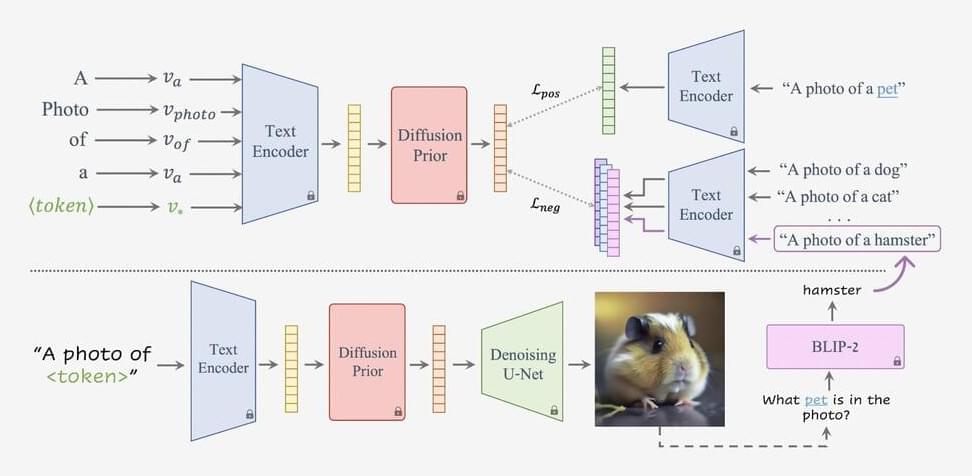
Researchers have been putting in efforts to find out how one can use these technologies to create wholly original and inventive notions. For that, in a recent research paper, a team of researchers introduced Concept Lab in the field of inventive text-to-image generation. The basic goal in this domain is to provide fresh examples that fall within a broad categorization. Considering the challenge of developing a new breed of pet that is radically different from all the breeds we are accustomed to, the domain of Diffusion Prior models is the main tool in this research.
This approach has drawn its inspiration from token-based personalization, which is a pre-trained generative model’s text encoder using a token to express a unique concept. Since there are no previous photographs of the intended subject, creating a new notion is more difficult than using a conventional inversion technique. The CLIP vision-language model has been used to direct the optimization process in order to address this. There are positive and negative sides to the limitations; while the negative limitations cover the existing members of the category from which the generation should deviate, the positive constraint promotes the development of images that are in line with the wide category.