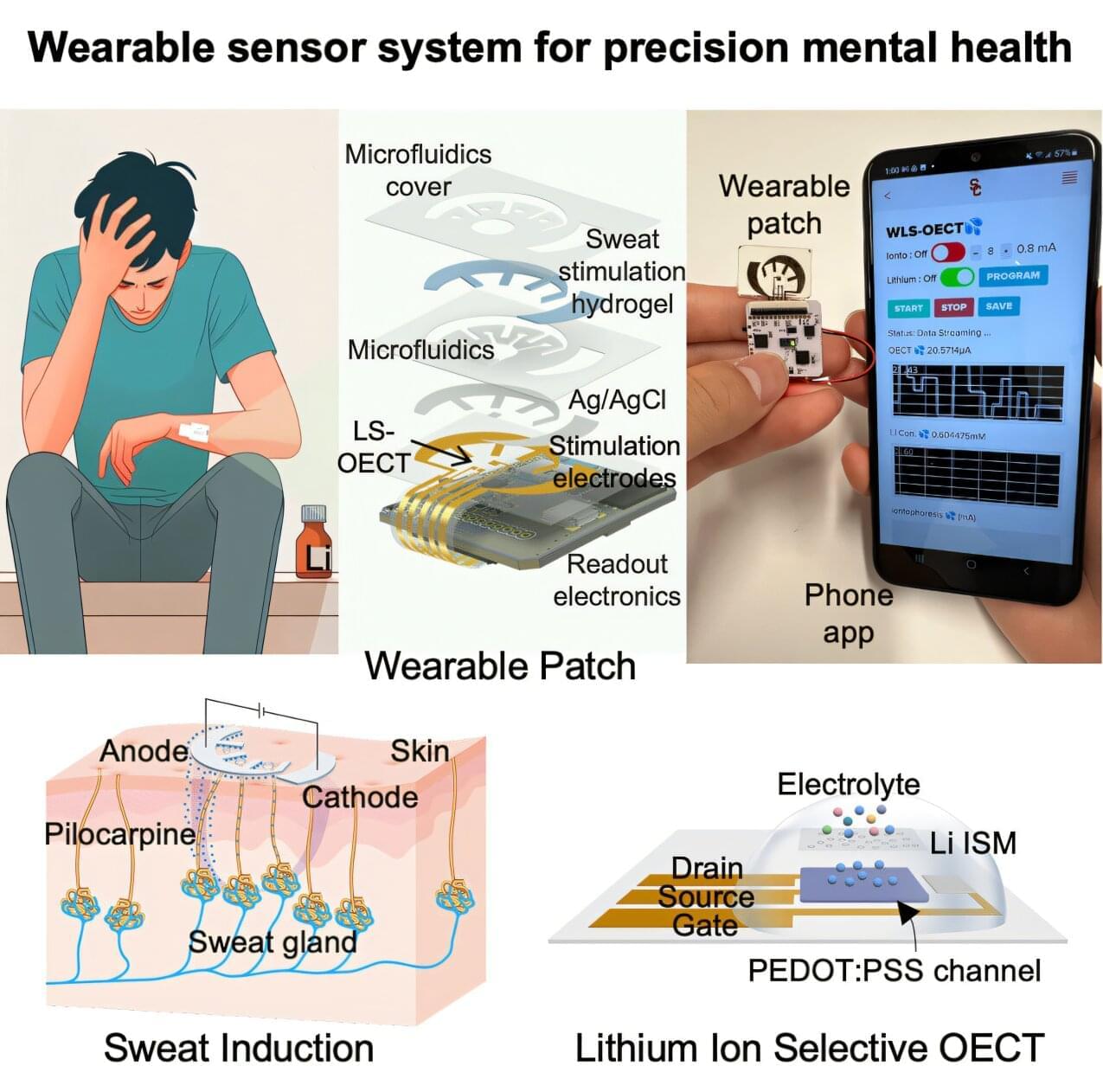
Although lithium is highly effective in treating bipolar disorder, the chemical has a narrow therapeutic window—too high a dose can be toxic to patients, causing kidney damage, thyroid damage, or even death, while too low a dose renders the treatment ineffective.
The dose of lithium varies between individuals based on body weight, diet, and other physiological factors, and requires regular measurement of lithium levels in the blood. Currently, this is only available through standard laboratory-based blood draws, which can be time-consuming, inconvenient, and painful. This makes personalized and easily-accessible lithium monitoring an important goal in the treatment for bipolar disorder.
“Our goal was to create an easy-to-use sensor that bypasses the need for blood draws entirely,” explained Yasser Khan, a USC Ming Hsieh Department of Electrical and Computer Engineering professor who leads the USC Khan Lab, and part of the USC Institute for Technology and Medical Systems (ITEMS), a joint initiative of USC Viterbi School of Engineering and Keck School of Medicine of USC focusing on innovative medical devices.