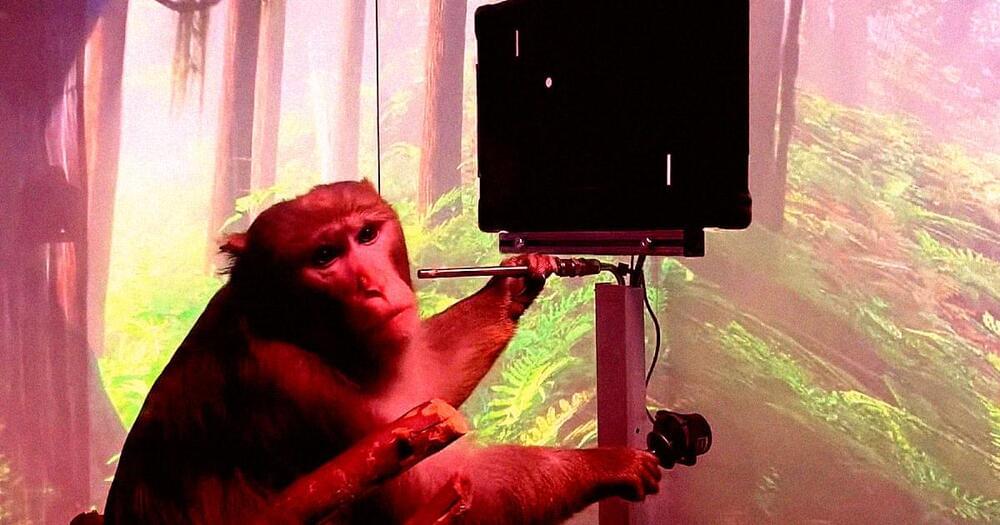
Jacopo Pantaleoni joined Nvidia in 2001 when the company had less than 500 employees. He worked on what was then a small research project to improve Nvidia’s graphics processing units so they could better render images on computers and gaming consoles.
More than two decades later, Nvidia has more than 26,000 employees and its GPUs are at the center of the generative AI explosion. Pantaleoni had climbed the ranks to become a principal engineer and research scientist, one of the highest ranking positions for an individual contributor, he says. Then, in July, as Nvidia boomed like no other company, Pantaleoni says he resigned, giving up a substantial amount of unvested stock units, after coming to a realization.
“This market of machine learning, artificial intelligence” is “almost entirely driven by the big players— Googles, Amazons, Metas”—that have the “enormous amounts of data and enormous amounts of capital” to develop AI at scale. Those companies are also Nvidia’s biggest customers. “This was not the world I wanted to help build,” he said.