The AI tools were complemented by quantum biology and bioengineering approaches.
Philip Gray/ORNL, U.S. Dept. of Energy.
Combining several advances.

“Regardless of the size of a city, well planned urban land patterns can reduce population exposures to weather extremes.”
Urban planning and design are crucial for creating resilient cities that can withstand and adapt to the impacts of climate change.
Now, University of Delaware researcher Jing Gao, assistant professor in the College of Earth, Ocean and Environment and a resident faculty member in the Data Science Institute, and colleague Melissa Bukovsky, associate professor in the Haub School of Environment and Natural Resources at the University of Wyoming, are exploring how future populations’ exposure to weather extremes under climatic circumstances present at the end of the twenty-first century will be impacted by changes in urban design.

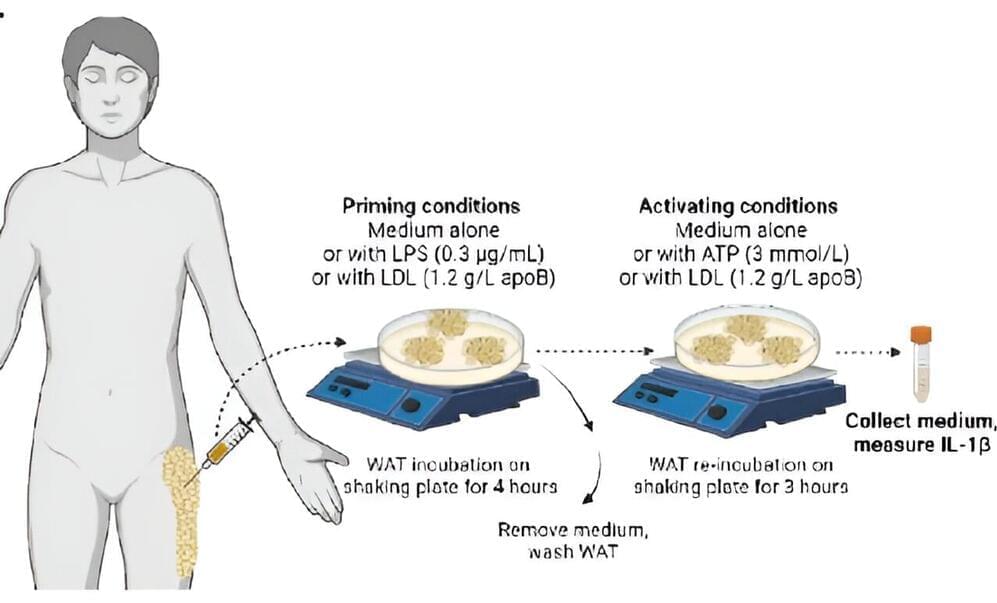
Canadian scientists have established for the first time a new mechanism and role for LDL in the development of type 2 diabetes, beyond its traditional role in the development of cardiovascular disease in humans.
Announced today for World Diabetes Day, the work was carried out by Université de Montréal professor May Faraj, director of the nutrition, lipoproteins and cardiometabolic diseases research unit at the Montreal Clinical Research Institute.
Her study, titled “Native low-density lipoproteins are priming signals of the NLRP3 inflammasome/interleukin1β pathway in human adipose tissue and macrophages,” is published in Scientific Reports.
Absolutely empty—that is how most of us envision the vacuum. Yet, in reality, it is filled with an energetic flickering: the quantum fluctuations.
Experts are currently preparing a laser experiment intended to verify these vacuum fluctuations in a novel way, which could potentially provide clues to new laws in physics. A research team from the Helmholtz-Zentrum Dresden-Rossendorf (HZDR) has developed a series of proposals designed to help conduct the experiment more effectively—thus increasing the chances of success. The team presents its findings in Physical Review D.
The physics world has long been aware that the vacuum is not entirely void but is filled with vacuum fluctuations—an ominous quantum flickering in time and space. Although it cannot be captured directly, its influence can be indirectly observed, for example, through changes in the electromagnetic fields of tiny particles.
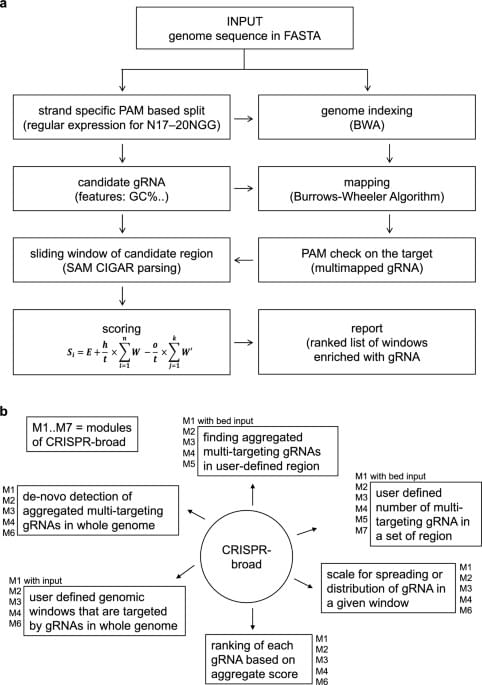
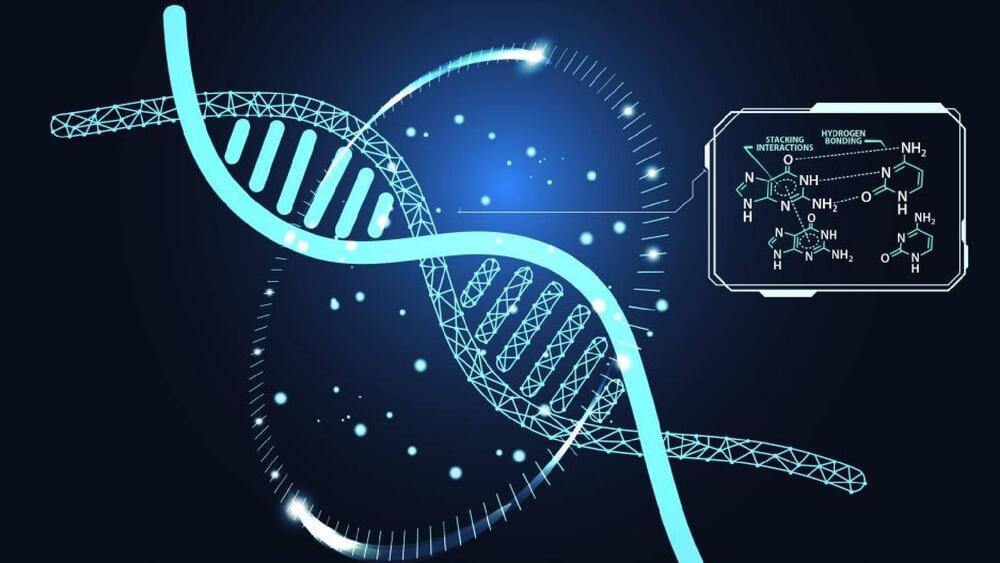
In CRISPR-Cas and related nuclease-mediated genome editing, target recognition is based on guide RNAs (gRNAs) that are complementary to selected DNA regions. While single site targeting is fundamental for localized genome editing, targeting to expanded and multiple chromosome elements is desirable for various biological applications such as genome mapping and epigenome editing that make use of different fusion proteins with enzymatically dead Cas9. The current gRNA design tools are not suitable for this task, as these are optimized for defining single gRNAs for unique loci. Here, we introduce CRISPR-broad, a standalone, open-source application that defines gRNAs with multiple but specific targets in large continuous or spread regions of the genome, as defined by the user.
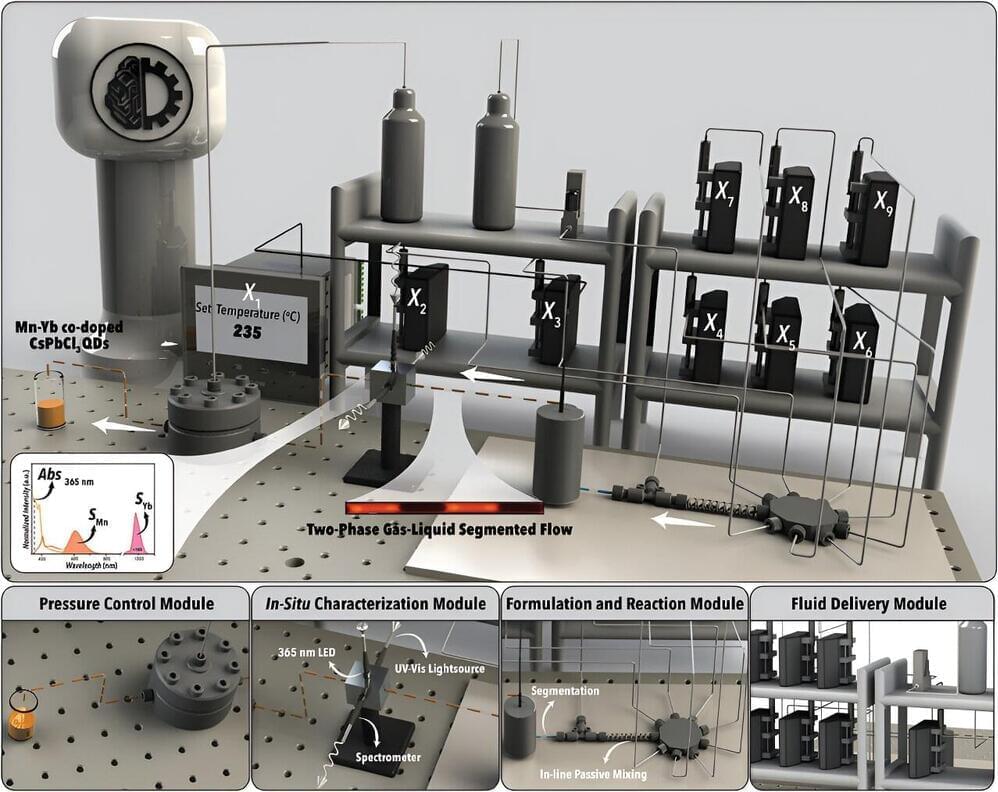
It can take years of focused laboratory work to determine how to make the highest quality materials for use in electronic and photonic devices. Researchers have now developed an autonomous system that can identify how to synthesize “best-in-class” materials for specific applications in hours or days.
The new system, called SmartDope, was developed to address a longstanding challenge regarding enhancing properties of materials called perovskite quantum dots via “doping.”
“These doped quantum dots are semiconductor nanocrystals that you have introduced specific impurities to in a targeted way, which alters their optical and physicochemical properties,” explains Milad Abolhasani, an associate professor of chemical engineering at North Carolina State University and corresponding author of the paper “Smart Dope: A Self-Driving Fluidic Lab for Accelerated Development of Doped Perovskite Quantum Dots,” published open access in the journal Advanced Energy Materials.


As the dawn of generative AI unfolds, a distinct separation will emerge among professionals and businesses: those who leverage this transformative technology to enhance productivity and innovation and those who lag behind.
Discover how adopting a generative AI mindset, blending adaptability, curiosity, and collaboration, is key to thriving in the rapidly evolving professional landscape,.