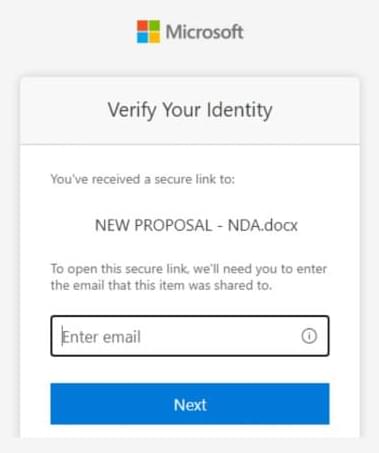
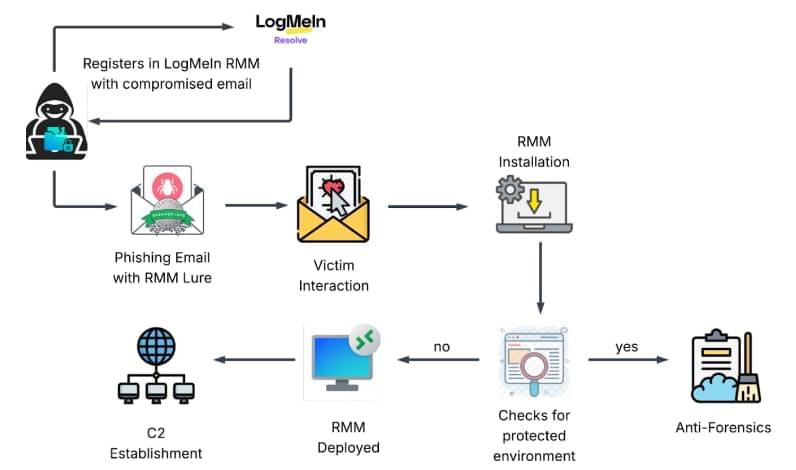
Microsoft reports a multi-stage AitM phishing and BEC campaign abusing SharePoint, inbox rules, and stolen session cookies to target energy orgs.





Yann LeCun’s new venture, AMI Labs, has drawn intense attention since the AI scientist left Meta to found it. This week, the startup finally confirmed what it’s building — and several key details have been hiding in plain sight.
On its newly launched website, the startup disclosed its plans to develop “world models” in order to “build intelligent systems that understand the real world.” The focus on world models was already hinted at by AMI’s name, which stands for Advanced Machine Intelligence, but it has now officially joined the ranks of the hottest AI research startups.
Building foundational models that bridge AI and the real world has become one of the field’s most exciting pursuits, attracting top scientists and deep-pocketed investors alike — product or no product.


A novel lithium-ion battery that uses silicon in its anodes may have the highest energy density of any battery currently commercially available. Its manufacturer, Enovix, says it has shipped the new battery to a leading smartphone company for a debut in mobile phones later this year.
Many of the lithium-ion batteries that power everything from mobile devices to electric cars use graphite in their anodes. However, for decades, researchers have investigated silicon as a replacement for this graphite. In theory, silicon offers roughly 10 times the energy density of graphite in lithium-ion batteries.
“Basically, graphite holds on to lithium using holes in its structure,” says Raj Talluri, CEO of Enovix. “In contrast, with silicon in the anodes—usually a silicon oxide or a silicon carbide—lithium actually chemically combines with the silicon to form a new material. This lets a silicon-based anode hold on to much more lithium than graphite during charging. When the battery discharges, the silicon material goes back to its original state.”

The rising incidence of cancer worldwide has led to an increasing number of surgeries that involve the removal of lymph nodes. Although these procedures play a major role in cancer staging and preventing the spread of malignancies, they sometimes come with severe long-term consequences.
Since lymph nodes do not naturally regenerate once removed, their absence can lead to a condition known as secondary lymphedema. It manifests as chronic swelling, discomfort, and reduced mobility in affected limbs or regions, severely affecting a patient’s quality of life.