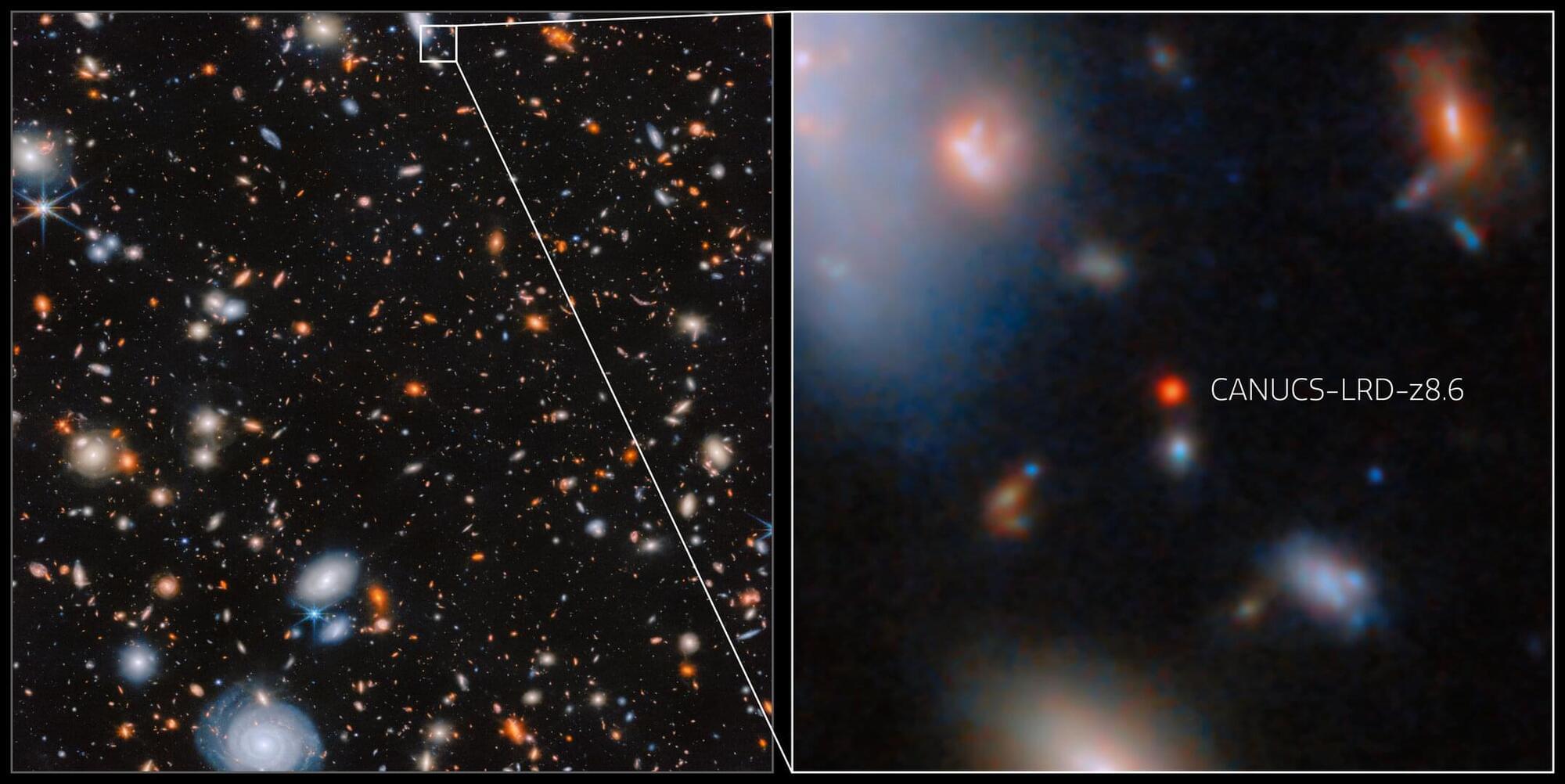
Researchers using the NASA/ESA/CSA James Webb Space Telescope have confirmed an actively growing supermassive black hole within a galaxy just 570 million years after the Big Bang. Part of a class of small, very distant galaxies that have mystified astronomers, CANUCS-LRD-z8.6 represents a vital piece of this puzzle and challenges existing theories about the formation of galaxies and black holes in the early Universe. The discovery connects early black holes with the luminous quasars we observe today.
Over its first three years, Webb’s surveys of the early Universe have turned up an increasing number of small, extremely distant, and strikingly red objects. These so-called Little Red Dots (LRDs) remain a tantalising mystery to astronomers, despite their unexpected abundance. The discovery in CANUCS-LRD-z8.6, made possible by Webb’s exceptional capabilities, has assisted in this hunt for answers. Webb’s Near-Infrared Spectrograph (NIRSpec) enabled researchers to observe the faint light from this distant galaxy and detect key spectral features that point to the presence of an accreting black hole.
Roberta Tripodi, lead author of the study and a researcher of the University of Ljubljana FMF, in Slovenia and INAF — Osservatorio Astronomico di Roma, in Italy, explained: “This discovery is truly remarkable. We’ve observed a galaxy from less than 600 million years after the Big Bang, and not only is it hosting a supermassive black hole, but the black hole is growing rapidly – far faster than we would expect in such a galaxy at this early time. This challenges our understanding of black hole and galaxy formation in the early Universe and opens up new avenues of research into how these objects came to be.”