Nanotechnology is intimately intertwined with efforts to bring bottom-up synthetic cell research to the forefront, and only strengthening these bonds will expand the scope of what this might achieve.
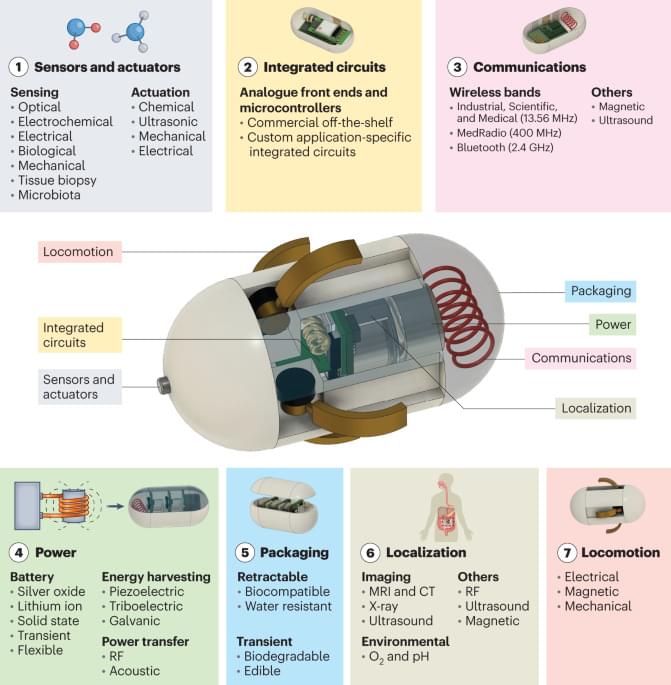
This Review explores the development of ingestible electronics and provides a step-by-step guide for the design of ingestible electronic capsules at the system level.
Sabine Hossenfelder and Bernardo Kastrup have a theolocution on superdeterminism and free variables.
Sponsors: https://brilliant.org/TOE for 20% off. For Algo’s podcast / @algopodcast and website https://www.algo.com/.
Patreon: / curtjaimungal.
Crypto: https://tinyurl.com/cryptoTOE
PayPal: https://tinyurl.com/paypalTOE
Twitter: / toewithcurt.
Discord Invite: / discord.
iTunes: https://podcasts.apple.com/ca/podcast…
Pandora: https://pdora.co/33b9lfP
Spotify: https://open.spotify.com/show/4gL14b9…
Subreddit r/TheoriesOfEverything: / theoriesofeverything.
Merch: https://tinyurl.com/TOEmerch.
LINKS MENTIONED:
–Sabine Hossefelder’s YouTube: / sabinehossenfelder.
–Testing Superdeterminism: https://arxiv.org/abs/1401.0286 / https://arxiv.org/abs/1105.4326
–Other Superdeterminism articles: https://arxiv.org/abs/2109.02676 / https://arxiv.org/abs/2010.01327
–Decoherence article: https://arxiv.org/abs/1911.06282
–Bernardo Kastrup’s website: https://www.bernardokastrup.com/
–No Go Theorem on Wigner: https://www.nature.com/articles/s4156…
–Making Sense of the Mental Universe\r by Kastrup: http://ispcjournal.org/journals/2017-…
LINKS NOT MENTIONED BUT PERTINENT:
NB Whilst claims of logical possibility intended to support reality claims (such as Swinburne’s proposal of disembodied existence) become subject to constraints of reality, those not intended to support any reality claim need not be subject to such constraints.
Selected Resources (see also part 1):
Churchland, P — Brain-Wise: Studies in Neurophilosophy (2002)
Swinburne, R — Evolution of the soul (1986)
It’s not easy to calculate the watts and joules that go into a single Balenciaga pope.
How many watts and joules does it actually take to generate a single Balenciaga pope?
When Lex Friedman visited our MIT AI Venture Studio class to talk about the future of AI, we got into some pretty interesting ideas about the near future.
At the top of Lex’s comments, he talked about disruption – predicting that two new trillion-dollar companies will emerge out of the AI era, and suggesting that Google, Meta and Microsoft will likely not be able to pivot quickly enough to maintain their dominance.
In terms of where we might see this innovation, one of his focus points was on language. Lex pointed out that in America, we take it for granted that everyone speaks English – but around the world, there is an enormous market for real, precise speech translation. People, he said, speak many languages in an “intimate” way – and that requires precision on the part of the technology.
According to a Chinese security expert, a significant number of attacks actually originate from countries in South Asia.
One India-based group of hackers, known as ‘Bitter’, has used various methods to target government, military and nuclear sectors.
SpaceX relocates incorporation to Texas amid legal challenges, reflecting Elon Musk’s strategic vision for growth and innovation.
Elon Musk’s SpaceX moves to Texas, signaling a strategic shift in corporate strategy amidst legal battles.
The AI chipmaker is the fourth most valuable company in the world.
Chip giant Nvidia is worth more than Google owner Alphabet, a day after surpassing Amazon in value.
The fourth group is Curium, an Iranian group that has used LLMs to generate phishing emails and code to evade antivirus detection. Chinese state-affiliated hackers have also used LLMs for research, scripting, translations, and refining their tools.
Fight AI with AI
Microsoft and OpenAI say they have not detected any significant attacks using LLMs yet, but they have been shutting down all accounts and assets associated with these groups. “At the same time, we feel this is important research to publish to expose early-stage, incremental moves that we observe well-known threat actors attempting, and share information on how we are blocking and countering them with the defender community,” says Microsoft.