“As our technologies have gotten more advanced, [we have] more and more control over…deeper levels of biological life.” — Bradley Cantrell.
Why biometrics will need and form of id to properly perform security checks.
Impersonators in many cases apparently had used synthetic bandages bearing thumb impressions of actual candidates. “Traditionally, fingerprints were used as evidence in court cases and even in high-tech security systems. But revelations by those arrested for impersonation in Bihar are proving to the world of forensic sciences that creating forged, latent fingerprints is relatively easy,” claims Dr Anand Rai, whistle-blower in the MPPEB scam. In the past, Rai had requested STF officials to look into interrogation reports of 140 impersonators arrested by the Bihar police during a constable recruitment exam.
Source: http://timesofindia.indiatimes.com/city/bhopal/MP-scamsters-…311540.cms
Hmmm.
Amazon’s Prime Air drone delivery service, if it ever gets off the ground, could one day use the top of street lights, cell towers, and even church steeples as docking stations for its flying machine.
The stations would serve as charging points for the drones, enabling them to stop off at multiple points for a battery boost thereby giving them a much greater flying range. Such a system could, in theory, open up pretty much the whole of the country to the possibility of drone delivery, as a single drone could hop from point to point on its way to an address.
The docking stations could also shelter the drones from harsh weather conditions that may develop after they leave the distribution center to begin their delivery run.
Volcanic super-eruptions are bad. Like really bad. Scientists warn of such a potentially civilization-ending catastrophe in our future, but as a new study shows, we’ll only have a year to prepare once the signs of an impending eruption become visible.
A new microscopic analysis of quartz crystals taken from the site of a massive volcanic eruption that occurred 760,000 years ago in eastern California suggests we’ll only have about a year’s worth of advance warning before a devastating super-eruption. In a paper published in PLOS ONE, Guilherme Gualda from Vanderbilt University and Stephen Sutton from the University of Chicago show that super-eruptions don’t require much time to blow their tops, even though they’re tens of thousands of years in the making.
I wonder, if NASA and/or SpaceX goes to Mars in the 2030’s as planned, by the time the 2050’s roll around a manned attempt to Ceres or Jupiter trojans might be attempted or perhaps an unmanned vehicle made on Mars beats this sail.
Japan’s space agency has its sights on unexplored asteroids as far away as Jupiter, a project that at one level draws on centuries of sail science.
The Japan Aerospace Exploration Agency this month unveiled a huge prototype solar sail designed to power a JAXA probe as it explores asteroids that circle the sun on roughly the same orbit as Jupiter. The sail measures 2,500 sq. meters and is made up of thousands of ultraslim solar panels.
I do love biometrics for security; however, many know that we will not only leverage biometrics alone for certifying identification given how easy it is for folks to retrieve others DNA information, etc. from commercial DNA sites, etc.
In the world of security, there are many tools at the IT Staff’s disposal which can be used to fight Cybercrimes of all types and levels. Regarding Physical Access Entry, Smart Cards and FOB’s are available to help alleviate the probability of a Social Engineering attack. Regarding Logical Access Entry, Network Intrusion Devices, Firewalls, Routers, etc. are also all ready to be installed and used.
But, there is one problem with all of these tools above: To some degree or another, all of them can be hijacked, stolen, or even spoofed so that a real Cyber hacker can find their way into a corporation very quickly and easily. For instance, a Smart Card can be easily lost or stolen; or even malformed data packets can be sent to a router and tricking it that it is a legitimate employee trying to gain access.
But, there is one Security technology out there which, for the most part, cannot be spoofed or tricked. As a result, it can provide 100% proof positive of the identity of an end user. This technology is known as Biometrics.
Dirty water has a use.
New technology doesn’t always look great, but researchers at Binghamton University are aiming to prove that function and style don’t have to be at odds with a new bacteria-powered battery that takes its design cues from origami.
Seokheun “Sean” Choi, an assistant professor of computer and electrical engineering at Binghamton, and two of his students recently published in the journal Biosensors and Bioelectronics a report on their invention of a microbial fuel cell that runs on nothing more than the bacteria found in just a few drops of dirty water.
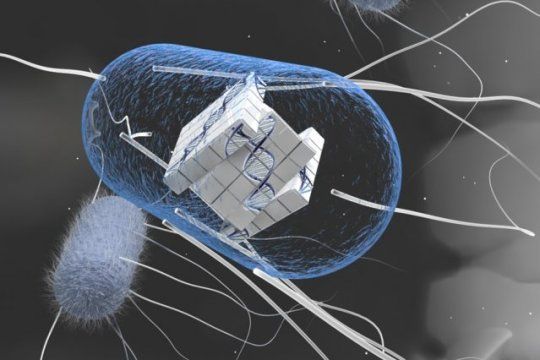
Like Botox; another bacteria found a new usage in healthcare.
Researchers at MIT and the University of California at San Diego (UCSD) have recruited some new soldiers in the fight against cancer—bacteria.
In a study appearing in the July 20 of Nature, the scientists programmed harmless strains of bacteria to deliver toxic payloads. When deployed together with a traditional cancer drug, the bacteria shrank aggressive liver tumors in mice much more effectively than either treatment alone.
The new approach exploits bacteria’s natural tendency to accumulate at disease sites. Certain strains of bacteria thrive in low-oxygen environments such as tumors, and suppression of the host’s immune system also creates favorable conditions for bacteria to flourish.