Dallas, Los Angeles, and now an Australian city.




Russia’s beleaguered space science program is hoping for a rare triumph this month. Spektr-RG, an x-ray satellite to be launched on 21 June from Kazakhstan, aims to map all of the estimated 100,000 galaxy clusters that can be seen across the universe. Containing as many as 1000 galaxies and the mass of 1 million billion suns, the clusters are the largest structures bound by gravity in the universe. Surveying them should shed light on the evolution of the universe and the nature of the dark energy that is accelerating its expansion.
Spektr-RG x-ray mission will be nation’s only space observatory.

Kyle Reese: The Terminator’s an infiltration unit, part man, part machine. Underneath, it’s a hyperalloy combat chassis — micro processor-controlled, fully armored. Very tough. But outside, it’s living human tissue — flesh, skin, hair, blood, grown for the cyborgs…
3D bioprinting is the automated fabrication of multicellular tissue via spatially defined deposition of cells. The ability to spatially control deposition in the x, y and z axes allows for creation of tissue-specific patterns or compartments, with in vivo-like architecture that mimics key aspects of native biology.
3D bioprinted tissues exhibit a microenvironment more suited to in vivo-like cellular function in comparison to traditional 2D monoculture (or monolayer co-cultures), as well as maintenance of a more defined architecture than is observed in self-aggregated co-culture models.

Neuroscientist Sara Lazar, of Mass General and Harvard Medical School, started studying meditation by accident. She sustained running injuries training for the Boston Marathon, and her physical therapist told her to stretch. So Lazar took up yoga.
“The yoga teacher made all sorts of claims, that yoga would increase your compassion and open your heart,” said Lazar. “And I’d think, ‘Yeah, yeah, yeah, I’m here to stretch.’ But I started noticing that I was calmer. I was better able to handle more difficult situations. I was more compassionate and open hearted, and able to see things from others’ points of view.”
Eventually, she looked up the scientific literature on mindfulness meditation (a category into which yoga can fall). She found the ever-increasing body of evidence that shows that meditation decreases stress, depression, and anxiety, reduces pain and insomnia, and increases quality of life.
A non-compact real form of the E8 Lie algebra has G2 and F4 subalgebras which break down to strong su, electroweak su x u, gravitational so(3,1), the frame-Higgs, and three generations of fermions related by triality. The interactions and dynamics of these 1-form and Grassmann valued parts of an E8 superconnection are described by the curvature and action over a four dimensional base manifold.
https://www.researchgate.net/…/2217412_An_Exceptionally_Sim…
ð½ ð¯

Elizabeth Parris, the CEO of Bioviva USA Inc, has become the very first human being to successfully, from a biological standpoint, reverse the age of her white blood cells, thanks to her own company’s experimental therapies. Bioviva utilizes intramural and extramural peer-reviewed research to create therapies for age-related diseases (Parkinson’s, Alzheimer’s, cancer, heart-disease), and now, they have reversed 20 years of ‘telomere shortening’ in a human for the first time.
Telomeres are short segments of DNA that cap the ends of every chromosome and act as a protective feature against wear and tear, which occurs naturally as the human body ages. As we age, these telomeres become shorter and shorter as our cells continue to divide more and more. Eventually they become too short to protect the chromosome, which is what causes our cells to malfunction and age related diseases to start setting in.
In September of last year, the 44 year old volunteered to partake in two of her own company’s experimental gene therapies; one intended to battle stem cell depletion, which happens when we age and leads to various age related diseases, and the other intended to protect against loss of muscle mass with age.
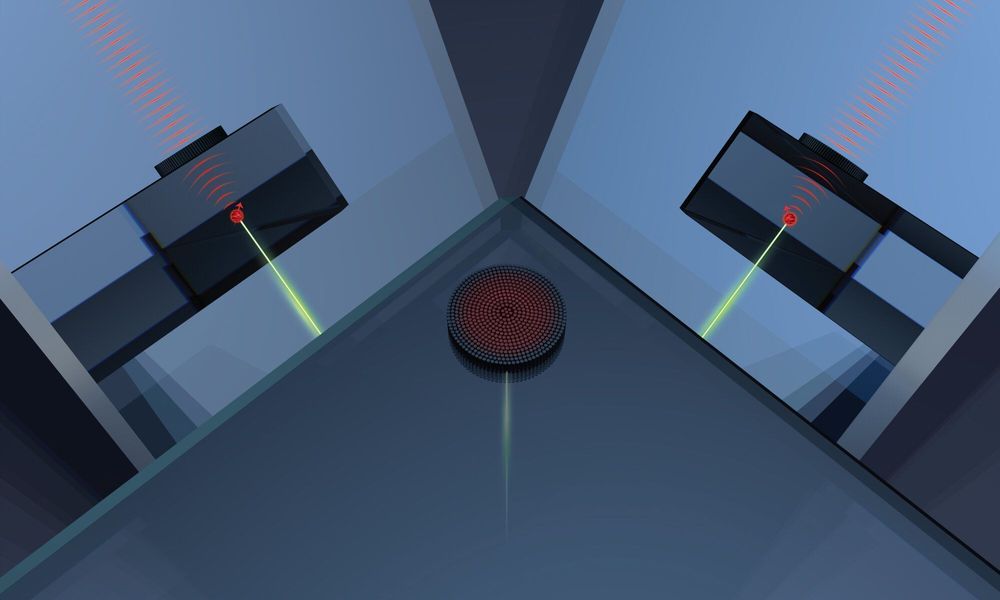
At the chemical level, diamonds are no more than carbon atoms aligned in a precise, three-dimensional (3D) crystal lattice. However, even a seemingly flawless diamond contains defects: spots in that lattice where a carbon atom is missing or has been replaced by something else. Some of these defects are highly desirable; they trap individual electrons that can absorb or emit light, causing the various colors found in diamond gemstones and, more importantly, creating a platform for diverse quantum technologies for advanced computing, secure communication and precision sensing.
Quantum technologies are based on units of quantum information known as “qubits.” The spin of electrons are prime candidates to serve as qubits; unlike binary computing systems where data takes the form of only 0s or 1s, electron spin can represent information as 0, 1, or both simultaneously in a quantum superposition. Qubits from diamonds are of particular interest to quantum scientists because their quantum-mechanical properties, including superposition, exist at room temperature, unlike many other potential quantum resources.
The practical challenge of collecting information from a single atom deep inside a crystal is a daunting one, however. Penn Engineers addressed this problem in a recent study in which they devised a way to pattern the surface of a diamond that makes it easier to collect light from the defects inside. Called a metalens, this surface structure contains nanoscale features that bend and focus the light emitted by the defects, despite being effectively flat.
