Patch Tuesday delivers fixes for 59 Microsoft flaws, six exploited zero-days, plus critical SAP and Intel TDX vulnerabilities.



Microsoft has fixed a “remote code execution” vulnerability in Windows 11 Notepad that allowed attackers to execute local or remote programs by tricking users into clicking specially crafted Markdown links, without displaying any Windows security warnings.
With the release of Windows 1.0, Microsoft introduced Notepad, a simple, easy-to-use text editor that, over the years, became popular for quickly jotting notes, reading text files, creating to-do lists, or acting as a code editor.
For those who needed a rich text format (RTF) editor that supported different fonts, sizes, and formatting tools like bold, italics, and lists, you could use Windows Write and later WordPad.

Found in everything from protein bars to energy drinks, erythritol has long been considered a safe alternative to sugar.
But research suggests this widely used sweetener may be quietly undermining one of the body’s most crucial protective barriers – with potentially serious consequences for heart health and stroke risk.
A study from the University of Colorado suggests erythritol may damage cells in the blood-brain barrier, the brain’s security system that keeps out harmful substances while letting in nutrients.
Elon Musk Announces MAJOR Company Changes as XAI/SpaceX ## Elon Musk is announcing significant changes and advancements across his companies, primarily focused on developing and integrating artificial intelligence (AI) to drive innovation, productivity, and growth ## ## Questions to inspire discussion.
Product Development & Market Position.
🚀 Q: How fast did xAI achieve market leadership compared to competitors?
A: xAI reached number one in voice, image, video generation, and forecasting with the Grok 4.20 model in just 2.5 years, outpacing competitors who are 5–20 years old with larger teams and more resources.
📱 Q: What scale did xAI’s everything app reach in one year?
A: In one year, xAI went from nothing to 2M Teslas using Grok, deployed a Grok voice agent API, and built an everything app handling legal questions, slide decks, and puzzles.
The unveiling by IBM of two new quantum supercomputers and Denmark’s plans to develop “the world’s most powerful commercial quantum computer” mark just two of the latest developments in quantum technology’s increasingly rapid transition from experimental breakthroughs to practical applications.
There is growing promise of quantum technology’s ability to solve problems that today’s systems struggle to overcome, or cannot even begin to tackle, with implications for industry, national security and everyday life.
So, what exactly is quantum technology? At its core, it harnesses the counterintuitive laws of quantum mechanics, the branch of physics describing how matter and energy behave at the smallest scales. In this strange realm, particles can exist in several states simultaneously (superposition) and can remain connected across vast distances (entanglement).

Microsoft has released the Windows 10 KB5075912 extended security update to fix February 2026 Patch Tuesday vulnerabilities, including six zero-days, and continue rolling out replacements for expiring Secure Boot certificates.
If you are running Windows 10 Enterprise LTSC or are enrolled in the ESU program, you can install this update like normal by going into Settings, clicking on Windows Update, and manually performing a ’Check for Updates.’
After installing this update, Windows 10 will be updated to build 19045.6937, and Windows 10 Enterprise LTSC 2021 will be updated to build 19044.6937.

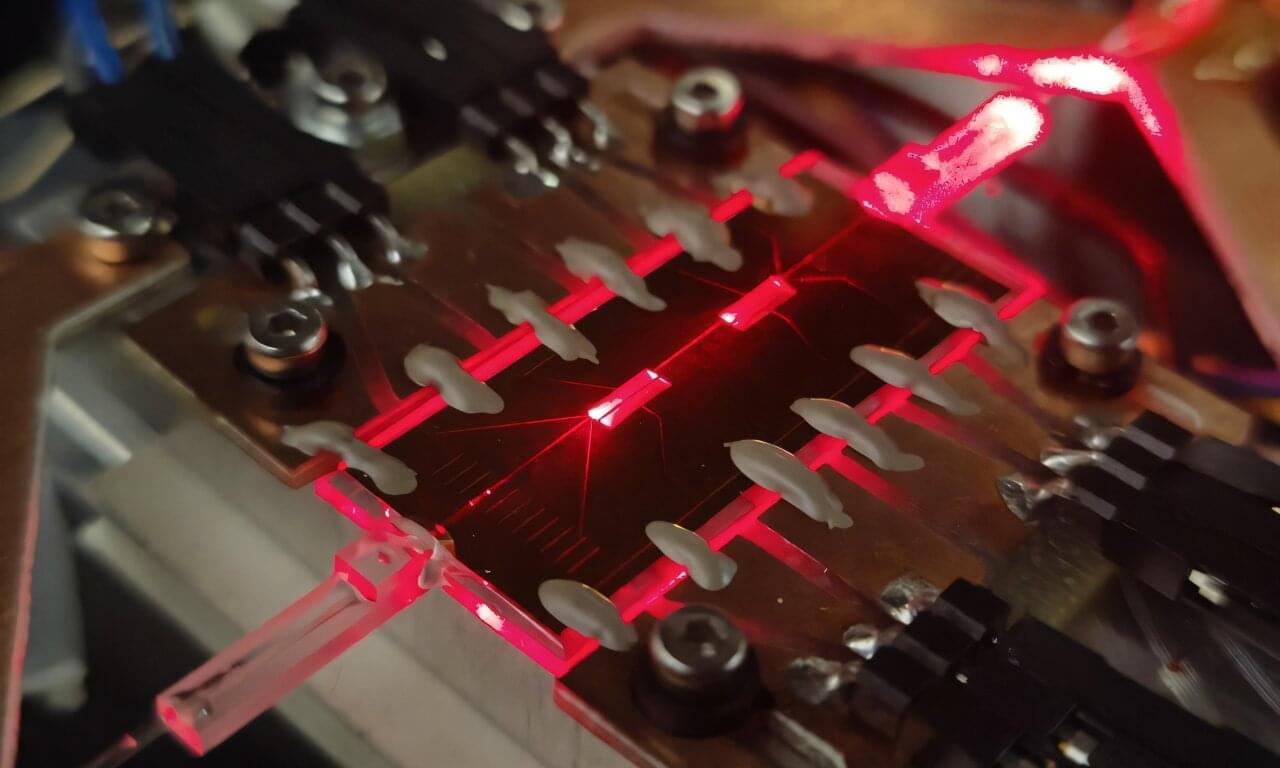
As quantum computers continue to advance, many of today’s encryption systems face the risk of becoming obsolete. A powerful alternative—quantum cryptography—offers security based on the laws of physics instead of computational difficulty. But to turn quantum communication into a practical technology, researchers need compact and reliable devices that can decode fragile quantum states carried by light.
A new study from teams at the University of Padua, Politecnico di Milano, and the CNR Institute for Photonics and Nanotechnologies shows how this goal can be approached using a simple material: borosilicate glass. As reported in Advanced Photonics, their work demonstrates a high-performance quantum coherent receiver fabricated directly inside glass using femtosecond laser writing. The approach provides low optical loss, stable operation, and broad compatibility with existing fiber-optic infrastructure—key factors for scaling quantum technologies beyond the laboratory.
Just after 9 a.m. on Friday, Feb. 6, 2026, final beams of oxygen ions—oxygen atoms stripped of their electrons—circulated through the twin 2.4-mile-circumference rings of the Relativistic Heavy Ion Collider (RHIC) and crashed into one another at nearly the speed of light inside the collider’s two house-sized particle detectors, STAR and sPHENIX. RHIC, a nuclear physics research facility at the U.S. Department of Energy’s (DOE) Brookhaven National Laboratory has been smashing atoms since the summer of 2000. The final collisions cap a quarter century of remarkable experiments using 10 different atomic species colliding over a wide range of energies in different configurations.
The RHIC program has produced groundbreaking discoveries about the building blocks of matter and the nature of proton spin and technological advances in accelerators, detectors, and computing that have far surpassed scientists’ expectations when this discovery machine first turned on.
“RHIC has been one of the most successful user facilities operated by the DOE Office of Science, serving thousands of scientists from across the nation and around the globe,” said DOE Under Secretary for Science Darío Gil. “Supporting these one-of-a-kind research facilities pushes the limits of technology and expands our understanding of our world through transformational science—central pillars of DOE’s mission to ensure America’s security and prosperity.”

PRESS RELEASE — Los Alamos National Laboratory has formed the Center for Quantum Computing, which will bring together the Lab’s diverse quantum computing research capabilities. Headquartered in downtown Los Alamos, the Center for Quantum Computing will consolidate the Laboratory’s expertise in national security applications, quantum algorithms, quantum computer science and workforce development in a shared research space.
“This new center of excellence will bring together the Laboratory’s quantum computing research capabilities that support Department of Energy, Defense and New Mexico state initiatives to achieve a critical mass of expertise greater than the individual parts,” said Mark Chadwick, associate Laboratory director for Simulation, Computing and Theory. “This development highlights our commitment to supporting the next generation of U.S. scientific and technological innovation in quantum computing, especially as the technology can support key Los Alamos missions.”
The center will bring together as many as three dozen quantum researchers from across the Lab. The center’s formation occurs at a pivotal time for the development of quantum computing, as Lab researchers partner with private industry and on a number of state and federal quantum computing initiatives to bring this high-priority technology closer to fruition. Laboratory researchers may include those working with the DARPA Quantum Benchmarking Initiative, the DOE’s Quantum Science Center, the National Nuclear Security Administration Advanced Simulation and Computing program’s Beyond Moore’s Law project, and multiple Laboratory Directed Research and Development projects.