Microsoft’s new write-once storage medium is constructed from quartz glass, stores data using lasers, and uses machine learning algorithms for decoding.
Category: information science – Page 256

Malwarebytes detects leaked tools from FireEye breach
The security company FireEye was breached by a sophisticated attack that stole multiple red team assessment tools. Malwarebytes customers are safe.
Hello folks! If you have not heard yet, the security firm FireEye has had a breach of many red team assessment tools used for identification of vulnerabilities to help protect customers.
While it is not known exactly who was behind this attack, a big concern is the sharing and use of these stolen red team tools by both sophisticated and non-sophisticated actors, similar to what we saw in 2017 with the ShadowBrokers group breach of the NSA’s Equation Group.
Reversing Senescence Through The Skin — Dr. Carolina Reis, CEO & Co-Founder, OneSkin Technologies
Dr. Carolina Reis Oliveria, is the CEO and Co-Founder of OneSkin Technologies, a biotechnology platform dedicated to exploring longevity science.
Carolina holds her Ph.D. in Immunology at the Federal University of Minas Gerais, in collaboration with the Rutgers University, where she conducted research with pluripotent stem cells as a source of retinal pigmented epithelium (RPE) cells, as well as the potential of RPE-stem cells derived as toxicological models for screening of new drugs with intra-ocular applications.
She founded a company called CELLSEQ solutions in Brazil which develops tools to revolutionize the safety and toxicology assays performed by pharmaceutical, cosmetic, agro-chemical and food industries, with technology based on stem cells and big data analysis.
She is an alumnus of IndieBio, the world’s leading biotechnology accelerator.
In 2016, Carolina relocated to Silicon Valley from Latin America to co-found OneSkin, and to lead the development of the company’s technologies.


How banks use AI to catch criminals and detect bias
Imagine an algorithm that reviews thousands of financial transactions every second and flags the fraudulent ones. This is something that has become possible thanks to advances in artificial intelligence in recent years, and it is a very attractive value proposition for banks that are flooded with huge amounts of daily transactions and a growing challenge of fighting financial crime, money laundering, financing of terrorism, and corruption.
The benefits of artificial intelligence, however, are not completely free. Companies that use AI to detect and prevent crime also deal with new challenges, such as algorithmic bias, a problem that happens when an AI algorithm causes systemic disadvantage for a group of a specific gender, ethnicity, or religion. In past years, algorithmic bias that hasn’t been well-controlled has damaged the reputation of the companies using it. It’s incredibly important to always be alert to the existence of such bias.
For instance, in 2019, the algorithm running Apple’s credit card was found to be biased against women, which caused a PR backlash against the company. In 2018, Amazon had to shut down an AI-powered hiring tool that also showed bias against women.
RealAnt: A low-cost quadruped robot that can learn via reinforcement learning
Over the past decade or so, roboticists and computer scientists have tried to use reinforcement learning (RL) approaches to train robots to efficiently navigate their environment and complete a variety of basic tasks. Building affordable robots that can support and manage the exploratory controls associated with RL algorithms, however, has so far proved to be fairly challenging.
Researchers at Aalto University and Ote Robotics have recently created RealAnt, a low-cost, four-legged robot that can effectively be used to test and implement RL algorithms. The new robotics platform, presented in a paper pre-published on arXiv, is a minimalistic and affordable real-world version of the ‘Ant’ robot simulation environment, which is often used in RL research.
“The initial inspirations for our work were RL studies that successfully demonstrated learning to walk from scratch on ant-like quadruped and humanoid robot simulations,” Jussi Sainio, co-founder of Ote Robotics, told Tech Xplore. “The underlying premise with RL algorithms is that programming a robot to do tasks becomes much easier and more ‘natural’—one just needs to define the available sensor measurements, motor actions, then set a target goal and plug them all into a reinforcement learning algorithm, which figures out the rest.”

A.I. Algorithms Are Making Robotic Hands Unimaginably Agile
Remember when the idea of a robotic hand was a clunky mitt that could do little more than crush things in its iron grip? Well, such clichés should be banished for good based on some impressive work coming out of the WMG department at the U.K.’s University of Warwick.
If the research lives up to its potential, robot hands could pretty soon be every bit as nimble as their flesh-and-blood counterparts. And it’s all thanks to some impressive simulation-based training, new A.I. algorithms, and the Shadow Robot Dexterous Hand created by the U.K.-based Shadow Robot Company (which Digital Trends has covered in detail before.)
Researchers at WMG Warwick have developed algorithms that can imbue the Dexterous Hand with impressive manipulation capabilities, enabling two robot hands to throw objects to one another or spin a pen around between their fingers.
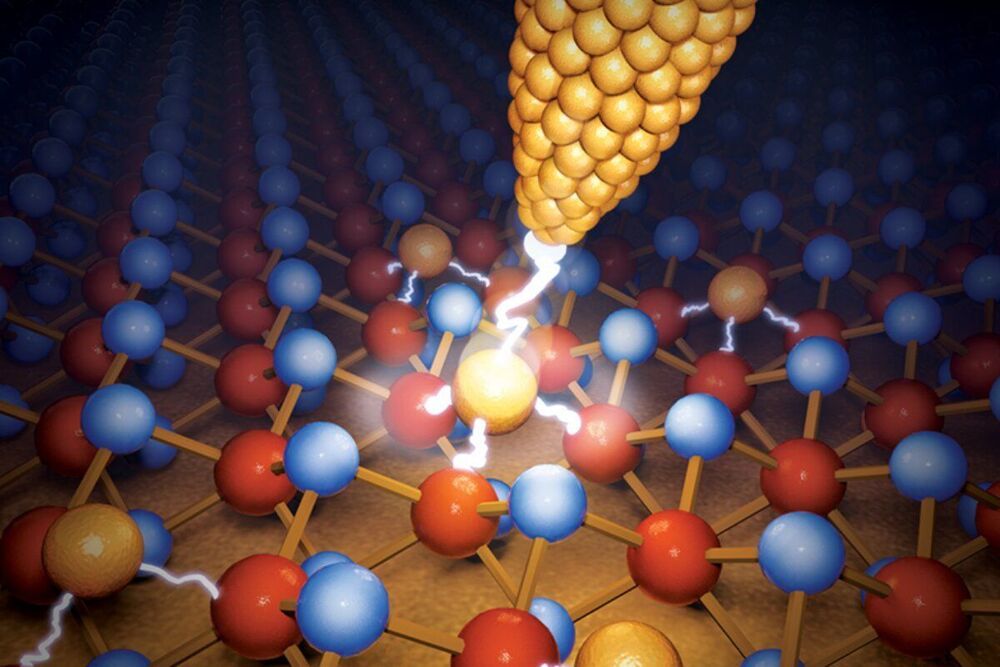
World’s smallest atom-memory unit created
Faster, smaller, smarter and more energy-efficient chips for everything from consumer electronics to big data to brain-inspired computing could soon be on the way after engineers at The University of Texas at Austin created the smallest memory device yet. And in the process, they figured out the physics dynamic that unlocks dense memory storage capabilities for these tiny devices.
The research published recently in Nature Nanotechnology builds on a discovery from two years ago, when the researchers created what was then the thinnest memory storage device. In this new work, the researchers reduced the size even further, shrinking the cross section area down to just a single square nanometer.
Getting a handle on the physics that pack dense memory storage capability into these devices enabled the ability to make them much smaller. Defects, or holes in the material, provide the key to unlocking the high-density memory storage capability.

JD unveils first phase of its smart city operating system
Since Xi put out the call to build up the new area, China’s tech giants have piled in. Alibaba Group Holding, Tencent Holdings, Baidu, Zhongguancun Science Park and Tsinghua University have all established projects in Xiongan. The projects include the use of sensors, 5G networks and facilities for supercomputing and big data in the pursuit of building up the smart city. Alibaba is the parent company of the Post.
JD Digits, the e-commerce giant’s big data arm, is building a smart city operating system that uses artificial intelligence for urban management.

Sorting Out Viruses With Machine Learning: AI-Powered Nanotechnology May Lead to New Rapid COVID-19 Tests
Scientists at Osaka University develop a label-free method for identifying respiratory viruses based on changes in electrical current when they pass through silicon nanopores, which may lead to new rapid COVID-19 tests.
The ongoing global pandemic has created an urgent need for rapid tests that can diagnose the presence of the SARS-CoV-2 virus, the pathogen that causes COVID-19, and distinguish it from other respiratory viruses. Now, researchers from Japan have demonstrated a new system for single-virion identification of common respiratory pathogens using a machine learning algorithm trained on changes in current across silicon nanopores. This work may lead to fast and accurate screening tests for diseases like COVID-19 and influenza.
In a study published this month in ACS Sensors scientists at Osaka University have introduced a new system using silicon nanopores sensitive enough to detect even a single virus particle when coupled with a machine learning algorithm.