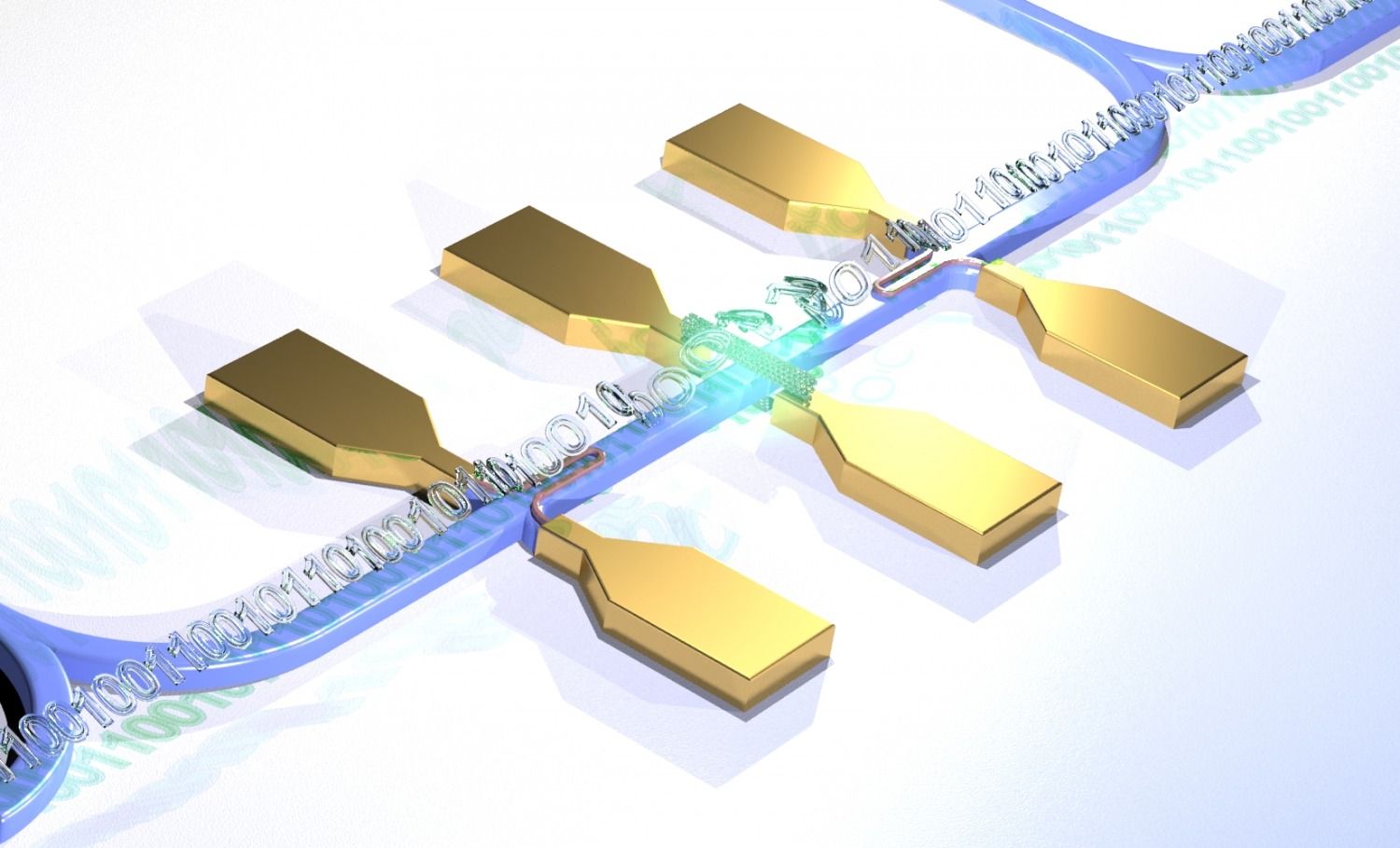
Whether for use in safe data encryption, ultrafast calculation of huge data volumes or so-called quantum simulation of highly complex systems: Optical quantum computers are a source of hope for tomorrow’s computer technology. For the first time, scientists now have succeeded in placing a complete quantum optical structure on a chip, as outlined Nature Photonics. This fulfills one condition for the use of photonic circuits in optical quantum computers.
“Experiments investigating the applicability of optical quantum technology so far have often claimed whole laboratory spaces,” explains Professor Ralph Krupke of the KIT. “However, if this technology is to be employed meaningfully, it must be accommodated on a minimum of space.” Participants in the study were scientists from Germany, Poland, and Russia under the leadership of Professors Wolfram Pernice of the Westphalian Wilhelm University of Münster (WWU) and Ralph Krupke, Manfred Kappes, and Carsten Rockstuhl of the Karlsruhe Institute of Technology (KIT).
The light source for the quantum photonic circuit used by the scientists for the first time were special nanotubes made of carbon. They have a diameter 100,000 times smaller than a human hair, and they emit single light particles when excited by laser light. Light particles (photons) are also referred to as light quanta. Hence the term “quantum photonics.”