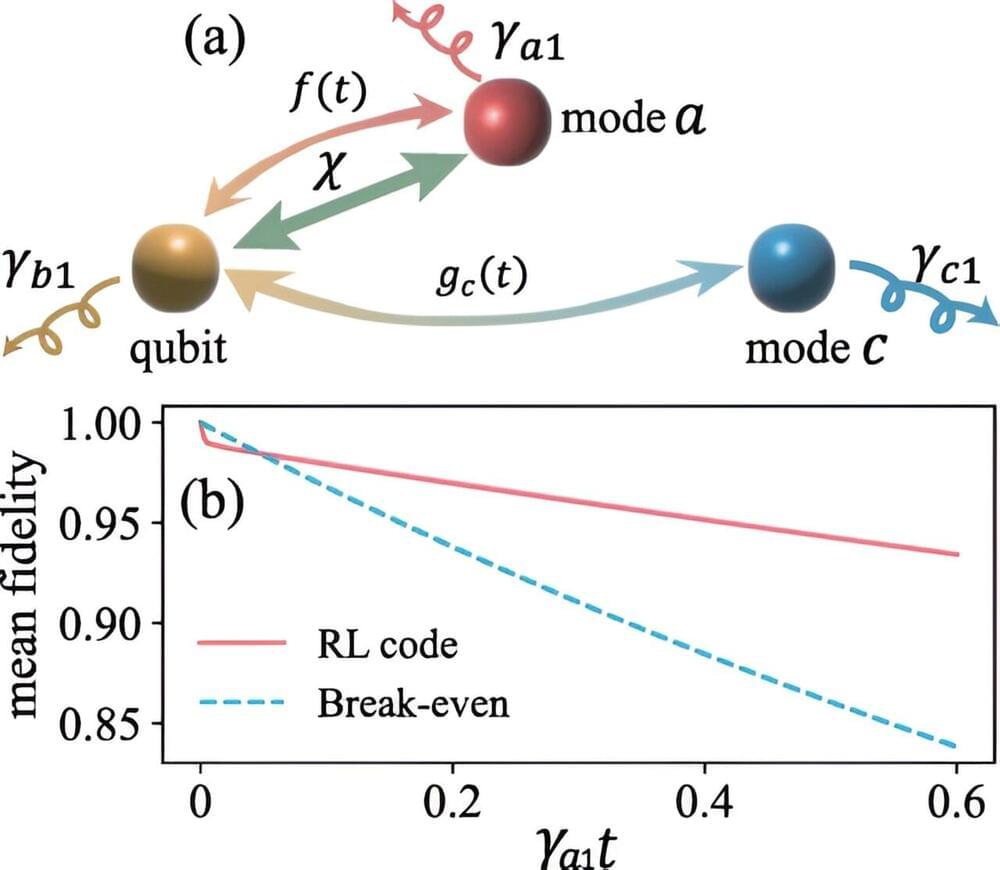
Its Outline VPN can now be built directly into apps—making it harder for governments to block internet access, particularly during protests.
Google is launching new anti-censorship technology created in response to actions by Iran’s government during the 2022 protests there, hoping that it will increase access for internet users living under authoritarian regimes all over the world.
Jigsaw, a unit of Google that operates sort of like an internet freedom think tank and that creates related products, already offers a suite of anti-censorship tools including Outline, which provides free, open, and encrypted access to the internet through a VPN. Outline uses a protocol that makes it hard to… More.