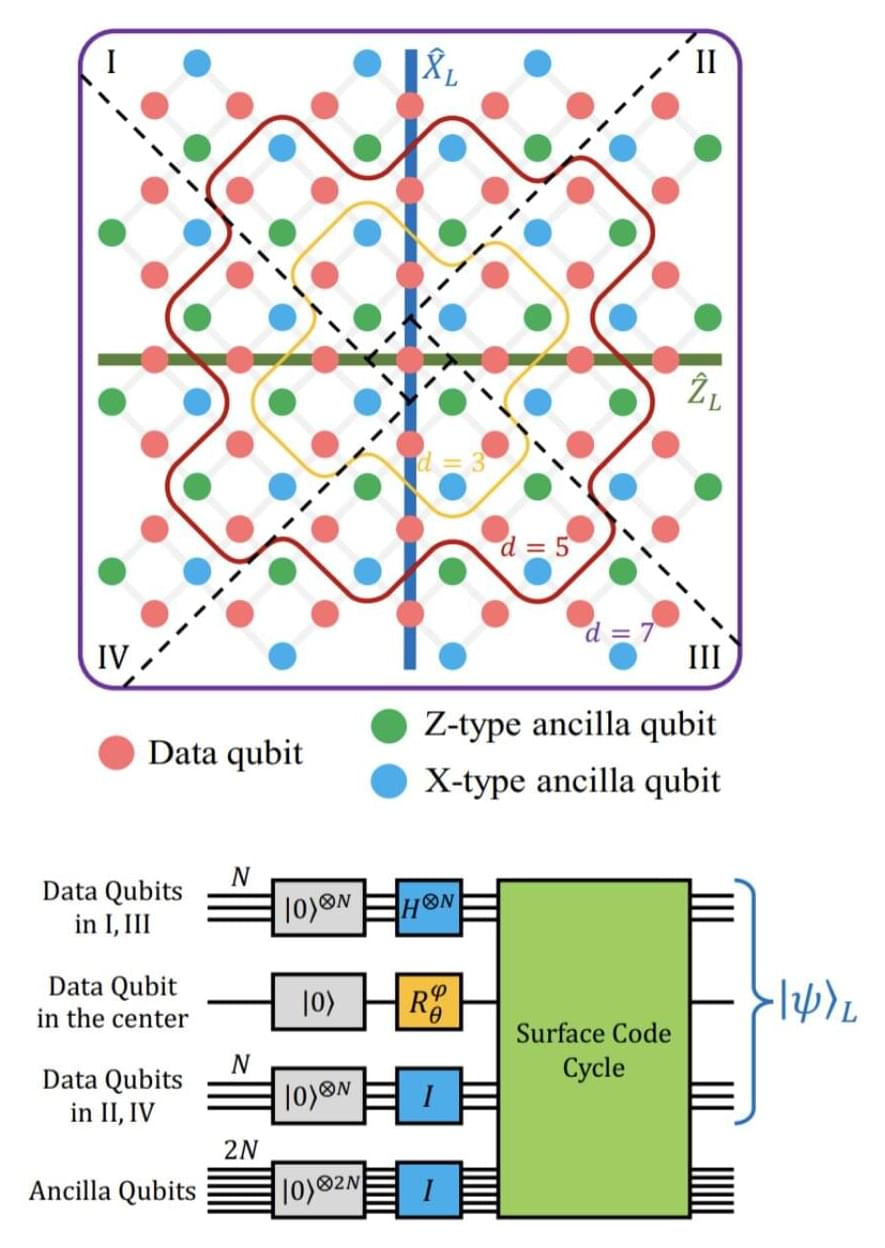
When the theoretical physicist Leonard Susskind encountered a head-scratching paradox about black holes, he turned to an unexpected place: computer science. In nature, most self-contained systems eventually reach thermodynamic equilibrium… but not black holes. The interior volume of a black hole appears to forever expand without limit. But why? Susskind had a suspicion that a concept called computational complexity, which underpins everything from cryptography to quantum computing to the blockchain and AI, might provide an explanation.
He and his colleagues believe that the complexity of quantum entanglement continues to evolve inside a black hole long past the point of what’s called “heat death.” Now Susskind and his collaborator, Adam Brown, have used this insight to propose a new law of physics: the second law of quantum complexity, a quantum analogue of the second law of thermodynamics.
Also appearing in the video: Xie Chen of CalTech, Adam Bouland of Stanford and Umesh Vazirani of UC Berkeley.
00:00 Intro to a second law of quantum complexity.
01:16 Entropy drives most closed systems to thermal equilibrium. Why are black holes different?
03:34 History of the concept of “entropy” and “heat death“
05:01 Quantum complexity and entanglement might explain black holes.
07:32 A turn to computational circuit complexity to describe black holes.
08:47 Using a block cipher and cryptography to test the theory.
10:16 A new law of physics is proposed.
11:23 Embracing a quantum universe leads to new insights.
12:20 When quantum complexity reaches an end…the universe begins again.
Thumbnail / title card image designed by Olena Shmahalo.
- VISIT our Website: https://www.quantamagazine.org.