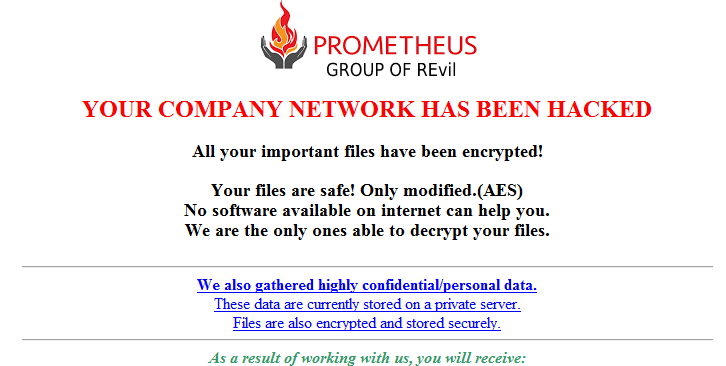
An emerging ransomware strain in the threat landscape claims to have breached 30 organizations in just four months since it went operational, riding on the coattails of a notorious ransomware syndicate.
First observed in February 2021, “Prometheus” is an offshoot of another well-known ransomware variant called Thanos, which was previously deployed against state-run organizations in the Middle East and North Africa last year.
The affected entities are believed to be government, financial services, manufacturing, logistics, consulting, agriculture, healthcare services, insurance agencies, energy and law firms in the U.S., U.K., and a dozen more countries in Asia, Europe, the Middle East, and South America, according to new research published by Palo Alto Networks’ Unit 42 threat intelligence team.