Autonomous machine expected to pick more than 25,000 raspberries a day, outpacing human workers.


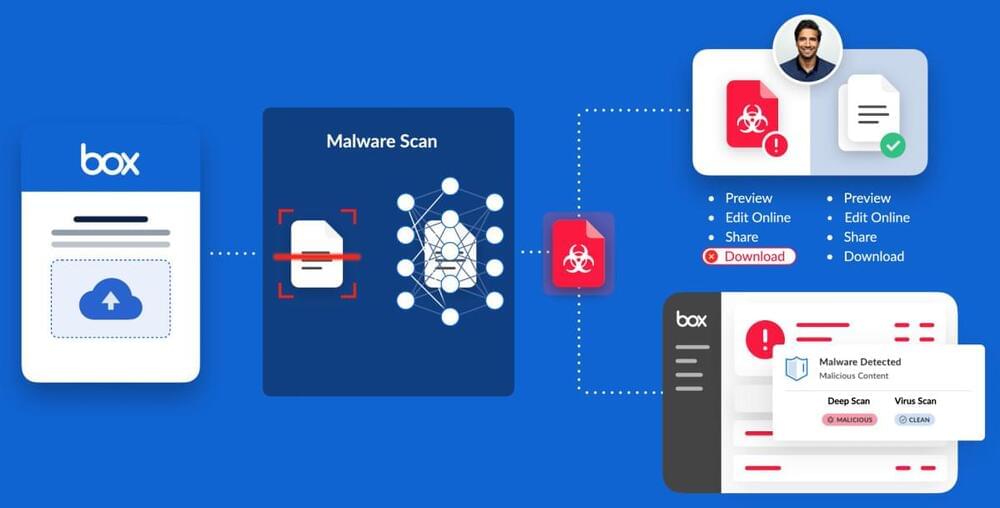
Cloud-based content management provider Box has announced a new “deep scan” functionality that checks files as they are uploaded to identify sophisticated malware and avert attacks.
The new capabilities constitute part of Box Shield, which uses machine learning to prevent data leaks, detect threats, and spot any kind of abnormal behavior. In April of last year, Box added a slew of automated malware detection features to the mix, allowing Box Shield customers to spot malicious content that may already have been uploaded to a Box account. However, so far this has leaned heavily on “known” threats from external intelligence databases. Moving forward, Box said it will mesh deep learning technology with external threat intelligence capabilities to analyze files for malicious scripts, macros, and executables to protect companies from zero-day (unknown) vulnerabilities.
When a user uploads an infected file, Box will quarantine it for inspection but will still allow the user to view a preview of the file and continue working.

These attacks were perpetrated by a newly discovered Iranian state sponsored threat group — dubbed MalKamak — that has been operating under the radar since at least 2018.
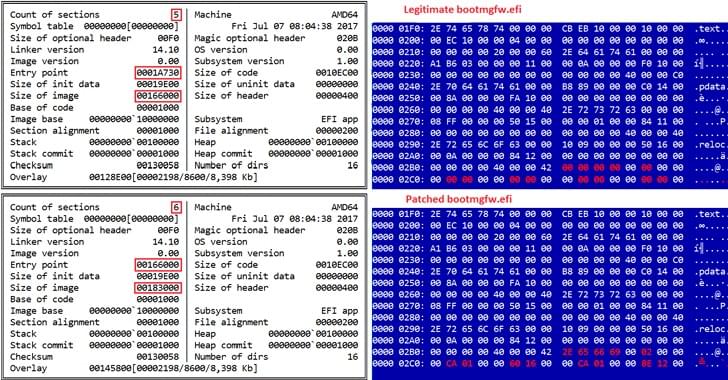
This operation has been ongoing for years, continuously evolving its malware year after year, while successfully evading most security tools. The authors of ShellClient invested a lot of effort into making it stealthy to evade detection by antivirus and other security tools by leveraging multiple obfuscation techniques and recently implementing a Dropbox client for command and control (C2), making it very hard to detect. By studying the ShellClient development cycles, Cybereason researchers were able to observe how ShellClient has morphed over time from a rather simple reverse shell to a sophisticated RAT used to facilitate cyber espionage operations.
The most recent ShellClient versions observed in Operation GhostShell follow the trend of abusing cloud-based storage services — in this case, the popular Dropbox service. The ShellClient authors used Dropbox to exfiltrate the stolen data and send commands to the malware. Threat actors have increasingly adopted this tactic due to its simplicity and the ability to effectively blend in with legitimate network traffic. Ultimately, this discovery tells researchers a lot about the tactics that advanced attackers are using to defeat security solutions.


The cybersecurity world is evolving rapidly — perhaps more quickly than at any other time in its history. It would be easy to attribute the cyber hiccups that many businesses face to the fact that they are simply unable to keep up with bad actors.
The facts are more complicated. While it’s true that new threats are emerging every day, more often than not, breaches result from long-standing organizational issues, not a sudden upturn in the ingenuity of cybercriminals.
Full Story:
The transaction-based communications system ensures robot teams achieve their goal even if some robots are hacked.
Imagine a team of autonomous drones equipped with advanced sensing equipment, searching for smoke as they fly high above the Sierra Nevada mountains. Once they spot a wildfire, these leader robots relay directions to a swarm of firefighting drones that speed to the site of the blaze.
But what would happen if one or more leader robots was hacked by a malicious agent and began sending incorrect directions? As follower robots are led farther from the fire, how would they know they had been duped?
The use of blockchain technology as a communication tool for a team of robots could provide security and safeguard against deception, according to a study by researchers at MIT and Polytechnic University of Madrid, which was published today in IEEE Transactions on Robotics. The research may also have applications in cities where multirobot systems of self-driving cars are delivering goods and moving people across town.


“Right now, organizations see a twofold gain from consolidating around a platform player in cybersecurity,” Nichols said. The first is, “to increase efficiency” but the other, he pointed out, is legislation. With more regulatory oversight in how companies are handling their cybersecurity challenges, the pressure is on them to make their systems more resilient, and having too many components becomes a challenge to manage for that reason, too.
“Joining One Identity provides us with the ability to further accelerate our growth and provide additional value for both of our customers,” added Brad Brooks, CEO of OneLogin, in a statement. “With OneLogin’s robust unified platform for both workforce and CIAM, combining forces with One Identity’s suite of products including their PAM solution will allow new and existing customers, on a global scale, to tap into the market’s only unified identity security platform.” consolidation is afoot in the world of cybersecurity, specifically around services to help organizations manage identity and access. Today, One Identity — which provides tools for managing “zero trust” access to systems, as well as running log management and other governance services for enterprises — announced that it has acquired OneLogin, a rival to companies like Okta, Ping and others in the area of secure sign-on services for end users.
Terms of the acquisition — which officially closed last week, on October 1 — are not being disclosed, but we are trying to find out.

Traditional networks are unable to keep up with the demands of modern computing, such as cutting-edge computation and bandwidth-demanding services like video analytics and cybersecurity. In recent years, there has been a major shift in the focus of network research towards software-defined networks (SDN) and network function virtualization (NFV), two concepts that could overcome the limitations of traditional networking. SDN is an approach to network architecture that allows the network to be controlled using software applications, whereas NFV seeks to move functions like firewalls and encryption to virtual servers. SDN and NFV can help enterprises perform more efficiently and reduce costs. Needless to say, a combination of the two would be far more powerful than either one alone.