Cybercriminals used two point-of-sale malware strains (POS) to steal the details of more than 167,000 credit cards worth nearly $3.34 million.



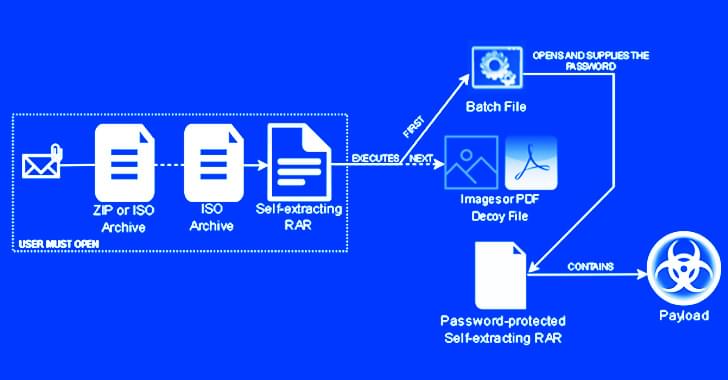
The notorious Emotet botnet has been linked to a new wave of malspam campaigns that take advantage of password-protected archive files to drop CoinMiner and Quasar RAT on compromised systems.
In an attack chain detected by Trustwave SpiderLabs researchers, an invoice-themed ZIP file lure was found to contain a nested self-extracting (SFX) archive, the first archive acting as a conduit to launch the second.
While phishing attacks like these traditionally require persuading the target into opening the attachment, the cybersecurity company said the campaign sidesteps this hurdle by making use of a batch file to automatically supply the password to unlock the payload.
A now-patched vulnerability in VMware Workspace ONE Access has been observed being exploited to deliver both cryptocurrency miners and ransomware on affected machines.
“The attacker intends to utilize a victim’s resources as much as possible, not only to install RAR1Ransom for extortion, but also to spread GuardMiner to collect cryptocurrency,” Fortinet FortiGuard Labs researcher Cara Lin said in a Thursday report.

Microsoft this week confirmed that it inadvertently exposed information related to thousands of customers following a security lapse that left an endpoint publicly accessible over the internet sans any authentication.
“This misconfiguration resulted in the potential for unauthenticated access to some business transaction data corresponding to interactions between Microsoft and prospective customers, such as the planning or potential implementation and provisioning of Microsoft services,” Microsoft said in an alert.
The misconfiguration of the Azure Blob Storage was spotted on September 24, 2022, by cybersecurity company SOCRadar, which termed the leak BlueBleed. Microsoft said it’s in the process of directly notifying impacted customers.

Almost 900 servers have been hacked using a critical Zimbra Collaboration Suite (ZCS) vulnerability, which at the time was a zero-day without a patch for nearly 1.5 months.
The vulnerability tracked as CVE-2022–41352 is a remote code execution flaw that allows attackers to send an email with a malicious archive attachment that plants a web shell in the ZCS server while, at the same time, bypassing antivirus checks.
According to the cybersecurity company Kaspersky, various APT (advanced persistent threat) groups actively exploited the flaw soon after it was reported on the Zimbra forums.


My book “Tales of the Turing Church: Hacking religion, enlightening science, awakening technology” is available for readers to buy on Amazon (Kindle | paperback).
Please note that there are two separate editions of the book, dated December 2018 and February 2020. The content of the two editions is identical, but the size and price of the paperback version are different.
See also “Tales of the Turing Church: Reactions and Reviews.”
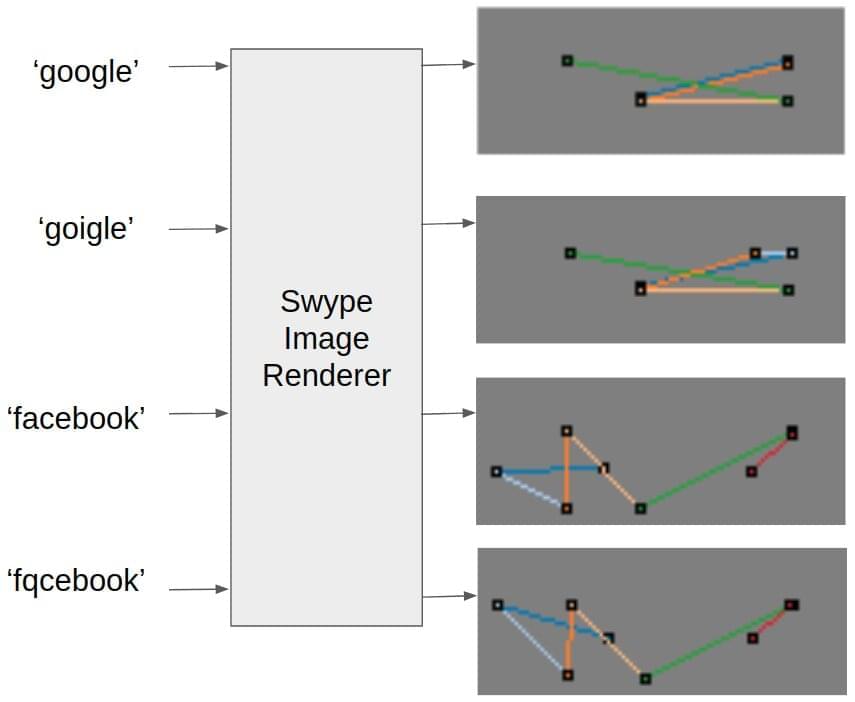
In recent decades, cyberattacks have become increasingly varied, introducing various strategies to lure users onto malicious websites or prompt them to share sensitive data. As a result, computer scientists are continuously trying to develop more advanced tools to detect and neutralize these attacks.
Typosquatting, one of the most common attacks carried out online, exploits the human tendency to misspell words when typing quickly or to misread words when they have small topographical errors. Typosquatting essentially consists in the creation of malicious websites with URLs that resemble established sites, but with slight typos (e.g., “fqcebook” instead of “facebook” or “yuube” instead of “youtube”). When a user mistakenly visits these websites, they might unwillingly download malware or end up sharing personal information with the attackers.
Most existing techniques for detecting these phishing attacks are based on spell-checking tools. While these tools can work in some instances, they do not generalize well, as their performance typically depends on the vocabulary of words used to train them.