Threat actor “Patchwork” uses romance scams to spread espionage apps in India and Pakistan! Learn how they infiltrated Android devices with VajraSpy.


Linux developers are in the process of patching a high-severity vulnerability that, in certain cases, allows the installation of malware that runs at the firmware level, giving infections access to the deepest parts of a device where they’re hard to detect or remove.
The vulnerability resides in shim, which in the context of Linux is a small component that runs in the firmware early in the boot process before the operating system has started. More specifically, the shim accompanying virtually all Linux distributions plays a crucial role in secure boot, a protection built into most modern computing devices to ensure every link in the boot process comes from a verified, trusted supplier. Successful exploitation of the vulnerability allows attackers to neutralize this mechanism by executing malicious firmware at the earliest stages of the boot process before the Unified Extensible Firmware Interface firmware has loaded and handed off control to the operating system.
The vulnerability, tracked as CVE-2023–40547, is what’s known as a buffer overflow, a coding bug that allows attackers to execute code of their choice. It resides in a part of the shim that processes booting up from a central server on a network using the same HTTP that the Internet is based on. Attackers can exploit the code-execution vulnerability in various scenarios, virtually all following some form of successful compromise of either the targeted device or the server or network the device boots from.

Welcome to the latest edition of Security & Tech Insights. In this newsletter, predictions on topics of cybersecurity, emerging computing, artificial intelligence, and space will be explored. Thanks for reading and sharing!
Chuck Brooks, Editor.
https://enterprise.spectrum.com/insights/blog/2024-enterpris…aid-Social.

Not all software is perfect—many apps, programs, and websites are released despite bugs. But the software behind critical systems like cryptographic protocols, medical devices, and space shuttles must be error-free, and ensuring the absence of bugs requires going beyond code reviews and testing. It requires formal verification.
Formal verification involves writing a mathematical proof of your code and is “one of the hardest but also most powerful ways of making sure your code is correct,” says Yuriy Brun, a professorat the University of Massachusetts Amherst.
To make formal verification easier, Brun and his colleagues devised a new AI-powered method called Baldur to automatically generate proofs. The accompanying paper, presented in December 2023 at the ACM Joint European Software Engineering Conference and Symposium on the Foundations of Software Engineering in San Francisco, won a Distinguished Paper award. The team includes Emily First, who completed the study as part of her doctoral dissertation at UMass Amherst; Markus Rabe, a former researcher at Google, where the study was conducted; and Talia Ringer, an assistant professor at the University of Illinois Urbana-Champaign.

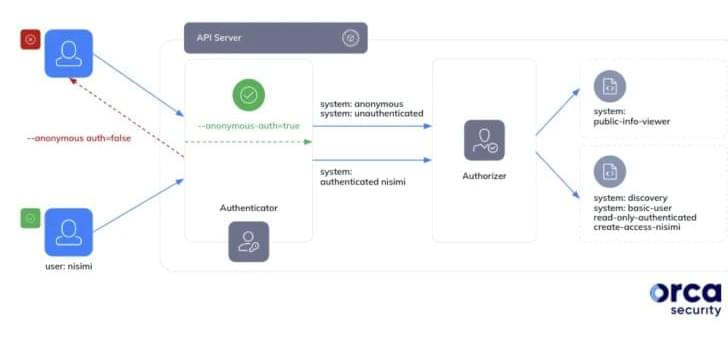
Cybersecurity researchers have discovered a loophole impacting Google Kubernetes Engine (GKE) that could be potentially exploited by threat actors with a Google account to take control of a Kubernetes cluster.
The critical shortcoming has been codenamed Sys: All by cloud security firm Orca. As many as 250,000 active GKE clusters in the wild are estimated to be susceptible to the attack vector.
In a report shared with The Hacker News, security researcher Ofir Yakobi said it “stems from a likely widespread misconception that the system: authenticated group in Google Kubernetes Engine includes only verified and deterministic identities, whereas in fact, it includes any Google authenticated account (even outside the organization).”
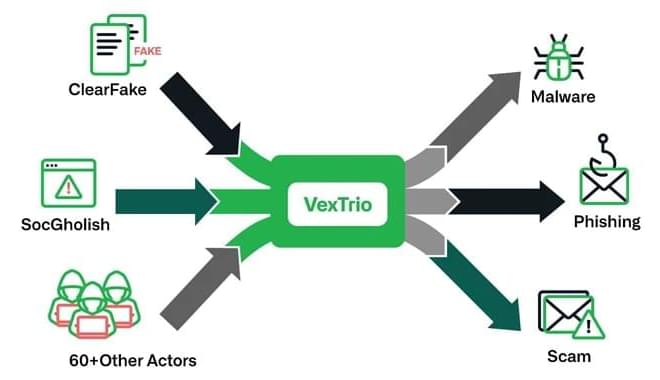
VexTrio, the shadowy entity controlling a massive network of 70,000+ domains, is finally in the spotlight. This “traffic broker” fuels countless scams & malware campaigns, including ClearFake, SocGholish, & more. Read:
The threat actors behind ClearFake, SocGholish, and dozens of other actors have established partnerships with another entity known as VexTrio as part of a massive “criminal affiliate program,” new findings from Infoblox reveal.
The latest development demonstrates the “breadth of their activities and depth of their connections within the cybercrime industry,” the company said, describing VexTrio as the “single largest malicious traffic broker described in security literature.”
VexTrio, which is believed to be have been active since at least 2017, has been attributed to malicious campaigns that use domains generated by a dictionary domain generation algorithm (DDGA) to propagate scams, riskware, spyware, adware, potentially unwanted programs (PUPs), and pornographic content.

The researchers have given the breach the title — MOAB, meaning ‘Mother of All Breaches.’
The security of your personal data hangs in the balance as cybersecurity experts uncover what could be the mother of all breaches, posing a threat of unprecedented proportions.
Researchers have warned that a database containing 26 billion leaked data records has been discovered. The supermassive data leak is likely the biggest found to date.
Your personal information may have been leaked in the ‘Mother of all Breaches’ (MOAB), cybersecurity researchers have warned.
Over 26 billion personal records have been exposed, in what researchers believe to be the biggest-ever data leak.
Sensitive information from several sites including Twitter, Dropbox, and Linkedin was discovered on an unsecured page.