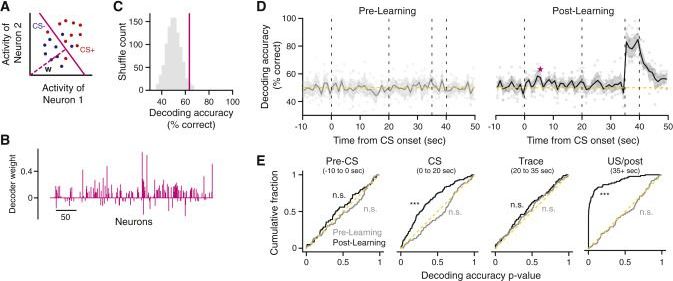
Episodic memory requires linking events in time, a function dependent on the hippocampus. In “trace” fear conditioning, animals learn to associate a neutral cue with an aversive stimulus despite their separation in time by a delay period on the order of tens of seconds. But how this temporal association forms remains unclear. Here we use two-photon calcium imaging of neural population dynamics throughout the course of learning and show that, in contrast to previous theories, hippocampal CA1 does not generate persistent activity to bridge the delay. Instead, learning is concomitant with broad changes in the active neural population. Although neural responses were stochastic in time, cue identity could be read out from population activity over longer timescales after learning. These results question the ubiquity of seconds-long neural sequences during temporal association learning and suggest that trace fear conditioning relies on mechanisms that differ from persistent activity accounts of working memory.
Sirtuins, telomeres, A.I. experiment with vitamin A and personalized medicine, a bit of everything here.
https://facebook.com/LongevityFB https://instagram.com/longevityyy https://twitter.com/Longevityyyyy https://linkedin.com/company/longevityy
- Please also subscribe and hit the notification bell and click “all” on these YouTube channels:
A warning that hackers are exploiting vulnerable email servers doesn’t qualify as an unusual event in general. But when that warning comes from the National Security Agency, and the hackers are some of the most dangerous state-sponsored agents in the world, run-of-the-mill email server hacking becomes significantly more alarming.
On Thursday, the NSA issued an advisory that the Russian hacker group known as Sandworm, a unit of the GRU military intelligence agency, has been actively exploiting a known vulnerability in Exim, a commonly used mail transfer agent—an alternative to bigger players like Exchange and Sendmail—running on email servers around the world. The agency warns that Sandworm has been exploiting vulnerable Exim mail servers since at least August 2019, using the hacked servers as an initial infection point on target systems and likely pivoting to other parts of the victim’s network. And while the NSA hasn’t said who those targets have been, or how many there are, Sandworm’s history as one of the most aggressive and destructive hacking organizations in the world makes any new activity from the group worth noting.
“We still consider this to be one of the most, if not the most aggressive and potentially dangerous actor that we track,” says John Hultquist, the director of intelligence at FireEye, who also led a team at iSight Partners when that company first discovered and named Sandworm in 2014.
The US National Security Agency (NSA) has published today a security alert warning of a new wave of cyberattacks against email servers, attacks conducted by one of Russia’s most advanced cyber-espionage units.
The NSA says that members of Unit 74455 of the GRU Main Center for Special Technologies (GTsST), a division of the Russian military intelligence service, have been attacking email servers running the Exim mail transfer agent (MTA).
Also known as “Sandworm,” this group has been hacking Exim servers since August 2019 by exploiting a critical vulnerability tracked as CVE-2019–10149, the NSA said in a security alert [PDF] shared today with ZDNet.
Circa 2017
Japanese scientists are developing a system to capture and remove space debris.
Editor’s Note: This article originally appeared on Business Insider.
The U.S. Air Force has been experimenting with turning its cargo and transport planes into munitions trucks able to drop devastating bundles of standoff weaponry, the service has revealed.
The Air Force Research Laboratory said Wednesday that Air Force Special Operations Command successfully dropped simulated palletized munitions from a MC-130J Commando II multi-mission combat transport/special operations tanker in a test at Dugway Proving Ground in Utah in January.
In 2019, the price of Bitcoin surged from $3,150 to $14,000 when the inflow of BTC into exchanges plunged, and it just happened again.
Not all viruses set out to cause widespread death and sickness — some have the potential to fight cancer, according to new research.
Researchers from Hokkaido University in Japan have genetically engineered adenoviruses, which is a family of viruses that cause mild symptoms, to replicate inside cancer cells and kill them, according to a new paper in the journal Cancers.
To do this, Fumihiro Higashino, a molecular oncologist, and his team inserted adenylate-uridylate-rich elements (AREs) from two human genes — a stabilizing element found in a type of macromolecule present in all biological cells — into two strains of the virus to help specifically attack cancer cells.
The Russians have their Avangard missiles and the Chinese have a railgun, but the Americans have developed maneuverable hypersonic shells for their existing artillery.
Landmark study identifies the genes that it seems people can and cannot live without and highlights ongoing challenges in making data sets more representative of the world’s population.