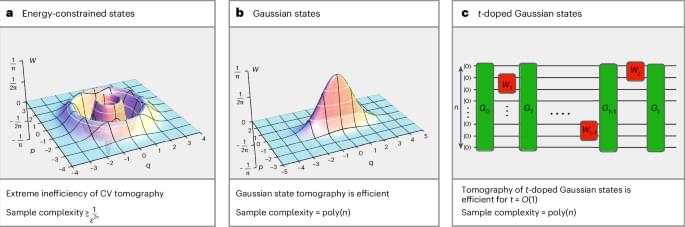
Partial laryngeal radiotherapy was associated with potentially favorable oncologic outcomes and toxic effects profiles compared to whole laryngeal radiotherapy.
This cohort study of clinical stage T1-2N0M0/Tis laryngeal cancer treated with radiotherapy in 233 patients at a single institution with more than 10 years of experience using IMRT between 2013 and 2024 found similar survival outcomes between WLRT and PLRT, with potentially lower toxic effects for PLRT. However, imprecise and unadjusted estimates prevent definitive conclusions. The patient-reported MDADI composite scores at 3 and 6 months postradiotherapy in the PLRT group were higher than the WLRT group.
The 3-year locoregional control outcome from this cohort was 86.5%, which is consistent with the initial observation study from our own institution,5 and previous studies3,7,8,14,15 reported 3-year local control rates of 70.0% to 94.4% of clinical stage T1-2N0M0/Tis laryngeal carcinoma treated with carotid sparing IMRT. Notably, our study had a 3-year locoregional control of 86.5%, which may be an overestimation because the median follow-up period in the PLRT group was only 31 (16−64) months. A history of smoking of 10 or more pack-years was associated with a 4.6-fold increased risk of local failure (HR, 4.62; 95% CI, 1.06−20.00). This finding corresponds with prior studies21-23 and emphasizes the importance of smoking cessation in laryngeal cancer.
Although PLRT for clinical stage T1-2N0M0/Tis laryngeal carcinoma can deliver a more precisely conformed dose to the target while sparing surrounding normal tissue—the uninvolved larynx, carotid arteries, thyroid gland, constrictor muscle, and upper esophagus12, 24 —the PLRT technique has still led to debate on the safety and benefit of this treatment. A major concern with this approach was the risk of geographic RT misses caused by inaccurate target delineation and target motion during RT due to patient swallowing. Few series15, 19, 24, 25 have reported on clinical outcomes of PLRT in clinical stage T1-2N0M0/Tis laryngeal carcinoma. Tans et al19 conducted a study that included 111 patients (108 with T1a and 3 with T2a) treated with PLRT (58.08 Gy) in 16 fractions and reported a 3-year local control rate of 99.1% with good voice handicap index scores.