The controversial scientist freed this year from jail for illegal medical practices has relocated to Beijing for his proposed US$7.2 million project.



This is my rebuttal to the recent MIT Technology Review article by Michael Hendricks. The views expressed here are mine alone and should not be taken as an official statement from the BPF which is an organization with a diverse range of opinions but a common goal to advocate more scientific research into brain preservation…


Regenerative medicine company Frequency Therapeutics is developing new drugs that activate our innate abilities to restore function and reverse degenerative diseases. The company is working on small molecules that selectively activate progenitor cells already present within our bodies to create healthy, functional tissues. Frequency’s initial focus is on hearing loss and multiple sclerosis, and the company has just completed enrolment of a Phase 2b trial in adults with acquired sensorineural hearing loss (SNHL).
Longevity. Technology: Frequency is focused on progenitor cells, which are like stem cells but can only make cells that belong to the same tissue or organ. While progenitor cells remain active in some of our organs and tissues, they can become dormant in others. Frequency’s small molecules are designed to selectively target and induce dormant progenitor cells to create specific cell types to restore tissue structure and function. We caught up with Frequency’s Chief Scientific Officer Dr Chris Loose to learn more.
Nasdaq-listed Frequency was founded in 2014, licensing technology developed by professors Robert Langer from MIT and Jeffrey Karp from Harvard Medical School.
Dr talks taking hardcore science to market without biotech approval risk and the catalyst that is translational research.
We were lucky enough to attend the Longevity Investors Conference last month; this key event attracts those interested in learning about longevity investment opportunities and finding out more about the exciting directions in which the field is accelerating. To put it succinctly, as MIT Tech Review did recently, LIC “brings academic scientists and biotech companies together with deep-pocketed investors. We’re talking millionaires and billionaires.”
One of the driving forces behind the Longevity Investors Conference is Dr Tobias Reichmuth; a company-builder since the age of 21, Reichmuth has invested in more than 20 startups and is one of the founding partners of Maximon, the longevity company building. Along with his Maximon colleague Marc P Bernegger, Riechmuth launched the Longevity Investors Conference, and we couldn’t pass up the chance to grab some time with him to discuss the current longevity market.
Visit Longevity. Technology — https://bit.ly/3PwtH8Y
Follow Longevity. Technology on:
Twitter — https://bit.ly/3AMIXuq.
Facebook — https://bit.ly/3z8H1v5
Instagram — https://bit.ly/3IDvVRX
Linkedin — https://bit.ly/3yIfDmf
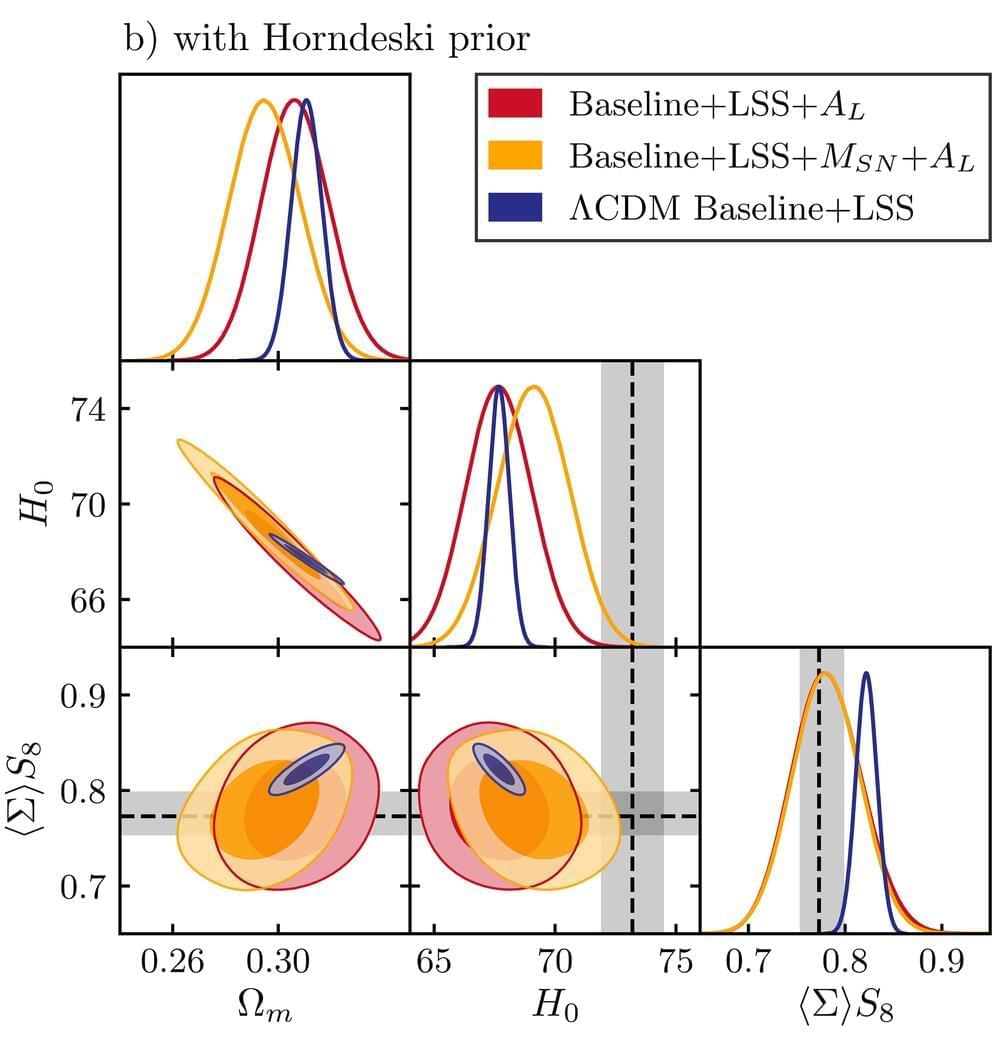
Scientists from around the world have reconstructed the laws of gravity, to help get a more precise picture of the universe and its constitution.
The standard model of cosmology is based on General Relativity, which describes gravity as the curving or warping of space and time. While the Einstein equations have been proven to work very well in our solar system, they had not been observationally confirmed to work over the entire universe.
An international team of cosmologists, including scientists from the University of Portsmouth in England, has now been able to test Einstein’s theory of gravity in the outer-reaches of space.
Sean Carroll: We might solve free will one day. But here’s why I doubt it.
Up next, The great free will debate ► https://youtu.be/3O61I0pNPg8
Debates about the existence of free will have traditionally been fought by two competing camps: those who believe in free will and those who don’t because they believe the Universe is deterministic.
Determinism is the thesis that every event — from when a volcano erupts to what cereal you buy at the supermarket — is a theoretically predictable result of the long chain of events that came before it. Free will, it was long thought, cannot exist in a world where all events are already causally determined.
But free will and determinism aren’t necessarily mutually exclusive. As physicist Sean Carroll told Big Think, the compatibilist conception of free will argues that it makes sense to conceptualize ourselves as able to make free decisions, regardless of whether the Universe is deterministic or indeterministic.
Why? The main argument centers on the phenomenon of emergence.
Less than 20 years ago, Konstantin Novoselov and Andre Geim first created two-dimensional crystals consisting of just one layer of carbon atoms. Known as graphene, this material has had quite a career since then.
Due to its exceptional strength, graphene is used today to reinforce products such as tennis rackets, car tires or aircraft wings. But it is also an interesting subject for fundamental research, as physicists keep discovering new, astonishing phenomena that have not been observed in other materials.

