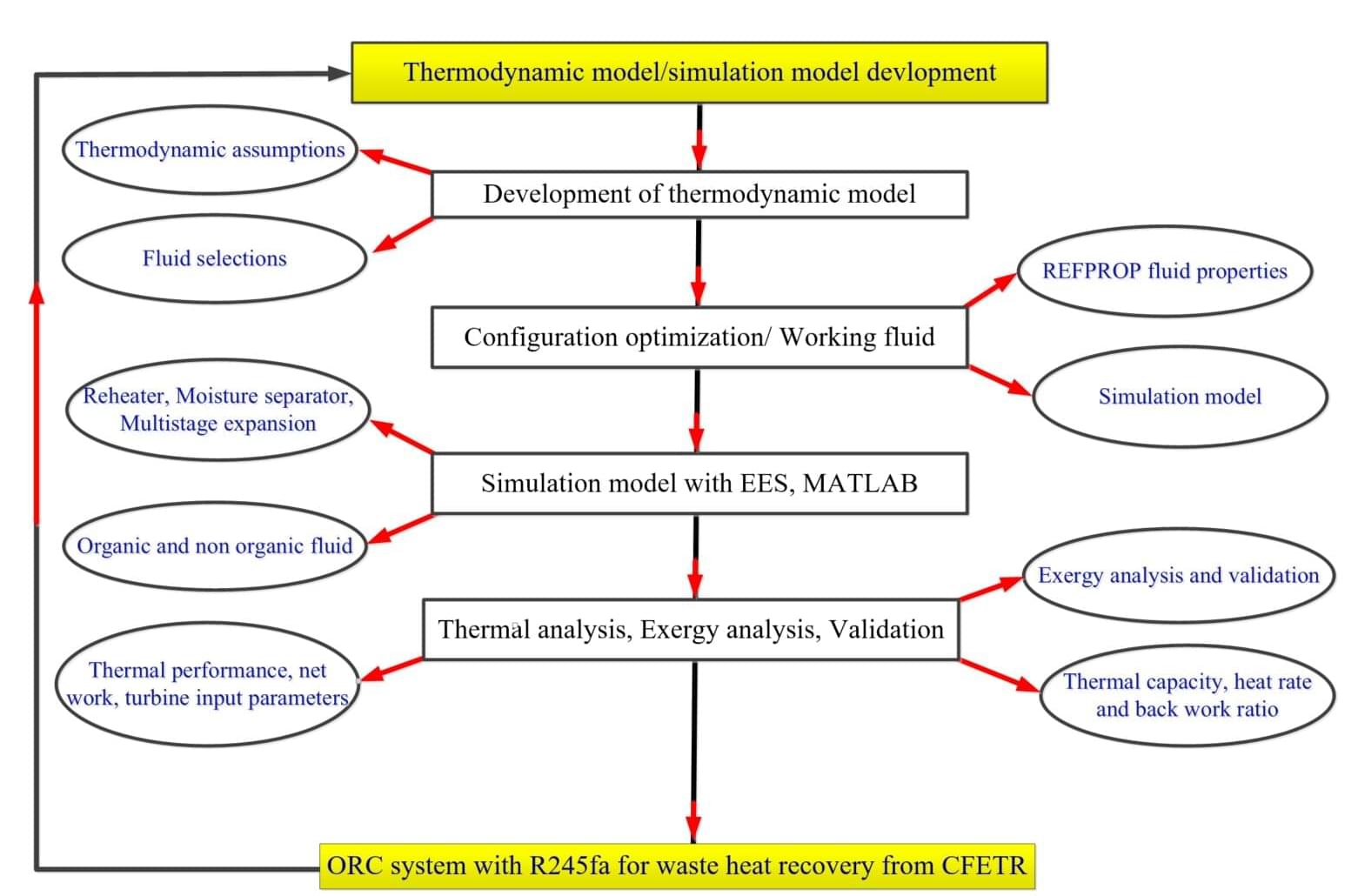
A research team led by Prof. Guo Bin from the Hefei Institutes of Physical Science of the Chinese Academy of Sciences has designed and optimized an organic Rankine cycle (ORC) system specifically for recovering low-grade waste heat from the steady-state Chinese Fusion Engineering Testing Reactor (CFETR) based on organic fluid R245fa, achieving enhanced thermal efficiency and reduced heat loss.
CFETR, a steady-state magnetic fusion reactor, is a crucial step toward realizing commercial fusion energy. However, managing the large amount of low-grade waste heat produced by components such as the divertor and blanket remains a key challenge.
To solve the thermodynamic and heat integration issues, the researchers developed advanced simulation models using Engineering Equation Solver for cycle analysis and MATLAB-based LAMP modeling for dynamic system configuration. These tools enabled a comprehensive investigation and optimization of the ORC configuration, leading to significantly improved thermal performance.