Zoom is the leader in modern enterprise cloud communications.






A research team from the School of Engineering at The Hong Kong University of Science and Technology (HKUST) has achieved a breakthrough in brain imaging by developing the world’s first technology to capture high-resolution images of the brains of awake experimental mice in a nearly noninvasive manner.
By eliminating the need for anesthesia, this innovation enables scientists to study brain tissue in its fully functional state. The advancement promises deeper insights into human brain function in both healthy and diseased conditions, opening new frontiers in neuroscience research.
The study was recently published in Nature Communications in a paper titled “Rapid adaptive optics enabling near-noninvasive high-resolution brain imaging in awake behaving mice.”

The sperm is not a passive supplier of genetic material to the egg. A study from Linköping University, Sweden, shows that certain molecules that come with the sperm, so-called micro-RNA, contribute to the development of the embryo several days after conception. The findings, published in the journal Nature Communications, may in the long term, contribute to better diagnosis and treatment of involuntary childlessness.
“It seems that sperms can help with embryo development by bringing other molecules with them, in addition to DNA. These molecules aid in starting embryo development. So you can say that the sperm, or the male part of conception, has a greater significance than was previously understood,” says Anita Öst, professor of cell and molecular biology at Linköping University, who led the study.
Many couples are affected by involuntary childlessness, or infertility. About one in six people suffer from infertility. For some, it is possible to become pregnant through what is known as in vitro fertilization, IVF, which takes place outside the body. The fertilized eggs are then transferred to the uterus and hopefully lead to pregnancy. Embryo quality is one of the major limiting factors for successful IVF treatment. Improved early embryo quality assessment could increase chances that IVF treatment leads to pregnancy.



Imagine a surgeon in the middle of a complex operation, able to get instant biochemical feedback not from a lab down the hall, but from the very tool in their hand. This vision is now one step closer to reality thanks to researchers at the University of Chemistry and Technology, Prague (UCT Prague).
The team, led by Professor Zdeněk Sofer, has developed and validated a “Lab-on-a-Scalpel” concept, a surgical tool with an integrated diagnostic sensor. They published their findings in the journal Analytical Chemistry.
This innovation addresses a critical challenge in surgery: the time lag between sample collection and lab results. During invasive procedures, a patient’s biochemical profile can change rapidly, but traditional testing methods are too slow to provide the real-time data needed for immediate, informed decisions.
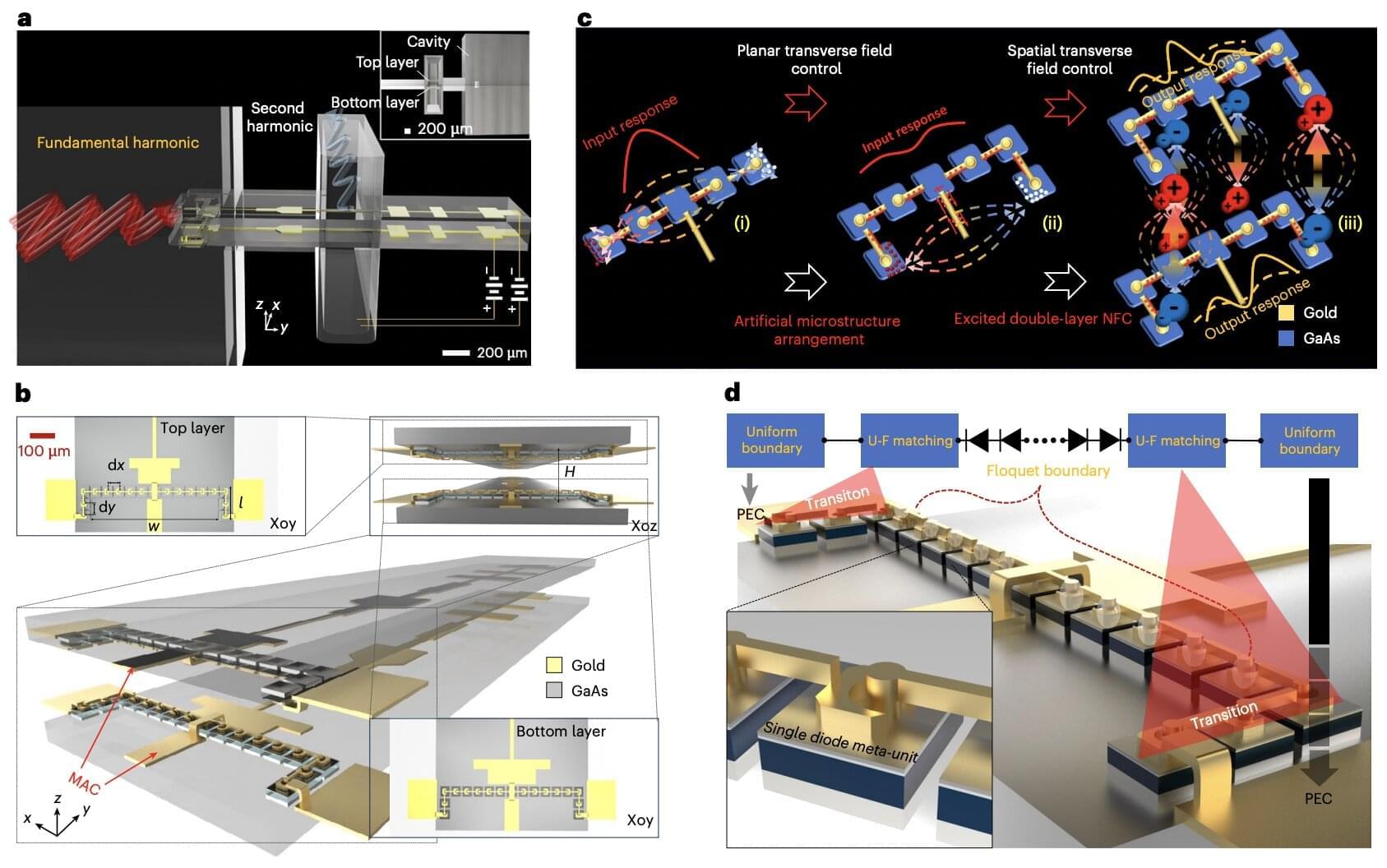
Electromagnetic waves with frequencies between microwave and infrared light, also known as terahertz radiation, are leveraged by many existing technologies, including various imaging tools and wireless communication systems. Despite their widespread use, generating strong and continuous terahertz signals using existing electronics is known to be challenging.
To reliably generate terahertz signals, engineers often rely on frequency multipliers, electronic circuits that can distort an input signal, to generate an output signal with a desired frequency. Some of these circuits are based on Schottky barrier diodes, devices in which the junction between a metal and semiconductor form a one-way electrical contact.
While some frequency multipliers based on Schottky barrier diodes have achieved promising results, devices based on individual diodes can only handle a limited amount of energy. To increase the energy they can manage, engineers can use several diodes arranged in a chain. However, even this approach can have its limitations, as the distribution of the electromagnetic field between the diodes in a chain often becomes uneven.